The O2 Platform script is called PoC - Selenium - Gui with 3 Hijacked Browser Windows.h2, and this is what it looks like when opened up:
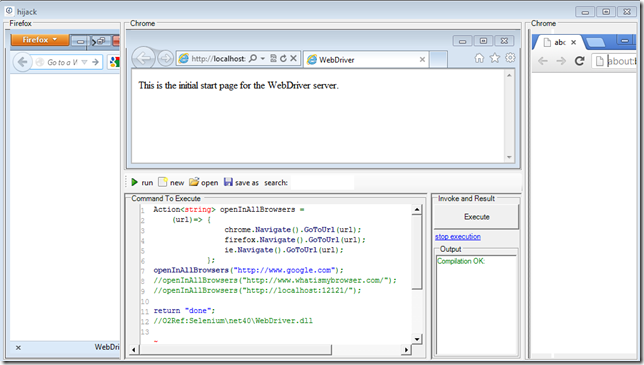
In this stand-alone exe/gui you can see:
- Firefox ‘hijacked’ window (left panel)
- IE ‘hijacked’ window (top middle panel)
- Chrome ‘hijacked’ window (right panel)
- C# REPL script (bottom middle panel)
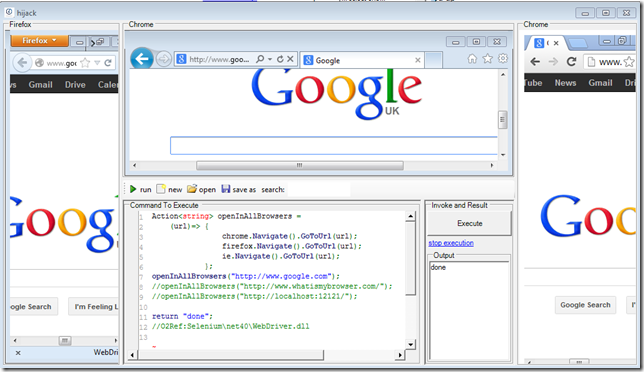
We can also confirm that we are indeed seeing the rendering of 3 individual browsers by going to the www.whatismybrowser.com website:

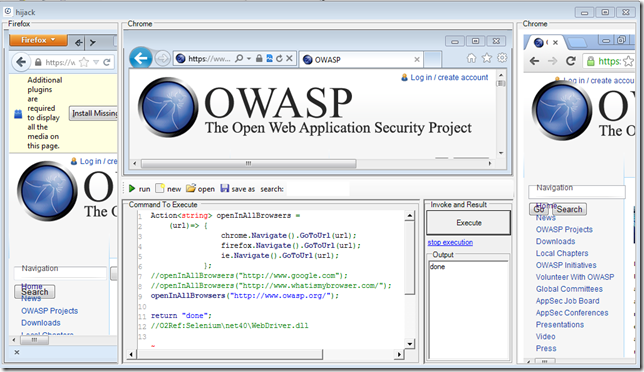
or owasp.org:
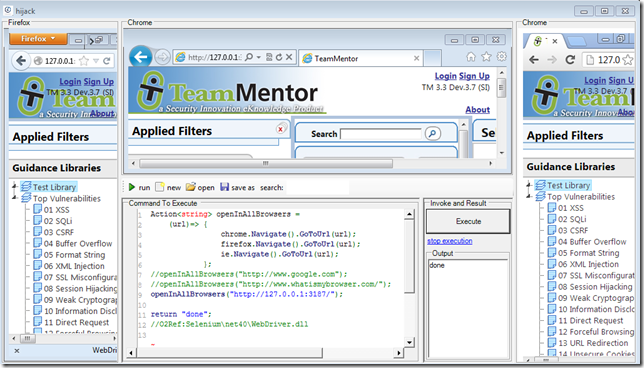
or a local copy of TeamMentor:
The key concept behind this PoC is the fact that we are NOT embedding ActiveX or COM objects in this Windows GUI :)
What you are seeing above are the (fully functional) browser’s main windows, each running in its own process.
To control the 3 browers, I use Selenium's browser-specific WebDriver apis/tools.
To grab the windows, I used the O2’s Window Handle Hijack technique that you can read about in these posts:
- Util - Win32 Window Handle Hijack (4x host panels) v1.0.exe
- Util - Win32 Window Handle Hijack (simple) v1.0.exe
- IBM AppScan Source's and AppScan Standard's TreeViews running side-by-site in the same GUI
- Util - Windows Handles - View Handle Screenshot v1.0.exe
- Showing Chrome, Eclipse, IBM AppScan Standard and VisualStudio in the same Process/Window
- Util - Windows Handles Viewer (with Child Windows) v1.0.exe
- Util - Windows Handles - View Handle Screenshot v1.0.exe
- Windows Shatter attacks (research links)
- Util - Windows Handles Viewer (Simple GUI with REPL) v1.0.exe
- Util - Windows Handles Viewer (Simple Gui) v1.0.exe
- Good resources on User32.dll windows messaging
- Injecting a .NET REPL into an Unmanaged/C++ application (Notepad)
See also Ian Spiro (AppScan Source guru) who posted Application Injection - Hooking into AppScan Standard in his IBM's Developer Works blog