At AppSec EU Steven van der Baan approached me with the great idea of seeing if we could do an open source implementation of Java Tainted Strings.
The idea is to (somehow) add metadata to the java.lang.String object and allow an App (or APIs) to taint a string (i.e. mark it as 'potentially malicious') and to modify that App/API's behaviour based on tainted information (for example "don't execute an SQL statement if its sql command string is tainted")
There is still a lot of thinking that needs to happen on this idea, and we are currently in the 'pre PoC' stage.
A personal blog about: transforming Web Application Security into an 'Application Visibility' engine, the OWASP O2 Platform, Application/Data interoperability and a lot more
Monday, 30 September 2013
Physical Books are the best technology for reading, and bookstores should 'give' an eBook with every physical book published
I just bought 5 books at a really nice book store in central London and it is amazing how:
- these bookstores are still afraid of the digital world
- don't have the confidence to say:
-
"... If you buy a physical copy, we will give you (or sell for 10%) the eBook version.
... the reason we 'give' you the eBook, is because the 'real' book is much better, but there are places were you might want to use the eBook.."
Labels:
Book,
Half-baked Idea,
Philosophy
Saturday, 28 September 2013
Script to Git Clone 13 repositories in order to have all TeamMentor Libraries in one folder
Part of the push for the 3.4 release of TeamMentor, I wanted to have a copy of all TeamMentor libraries locally (there are 13 libraries on the 3.4 release).
Since O2 Platform’s FluentSharp has native Git support, I was able to do create the clones using this script (note how simple it is to create a clone from a GitHub repo):
Since O2 Platform’s FluentSharp has native Git support, I was able to do create the clones using this script (note how simple it is to create a clone from a GitHub repo):
Labels:
FluentSharp,
Git,
TeamMentor
Friday, 27 September 2013
Using TeamMentor Checkmarx proxy to scan a vulnerable PHP application inside Eclipse
Michael Hidalgo has posted a really nice article which shows:
Check it out at : http://blog.michaelhidalgo.info/2013/09/using-teammentor-checkmarx-proxy-to.html
- an PHP app,
- inside Eclipse,
- scanned by Checkmark's SAST,
- with security guidance provided by TeamMentor
Check it out at : http://blog.michaelhidalgo.info/2013/09/using-teammentor-checkmarx-proxy-to.html
Labels:
Checkmarx,
TeamMentor
The Open Web Interface for .NET (OWIN) and Katana
Definitely need to take a look at this: http://www.asp.net/aspnet/overview/owin-and-katana/an-overview-of-project-katana (anybody used it?)
Here is its hello world example:
A quick skim of that article showed that they were inspired by Rack and Node.Js , which can't be a bad thing :)
Here is its hello world example:
A quick skim of that article showed that they were inspired by Rack and Node.Js , which can't be a bad thing :)
Labels:
To Read
Wednesday, 25 September 2013
Should developers code naked once a week? (or in a mankini?)
That way developers (or managers) would have more 'empathy' with the 'naked' state of the applications they are developing and publishing :)
I got this idea, following from this comment/suggestion on Guidelines of OWASP:
I got this idea, following from this comment/suggestion on Guidelines of OWASP:
Labels:
Half-baked Idea,
Security
Tuesday, 24 September 2013
Reaching out to Developers, Aspect is doing it right with Contrast
UPDATE: I got the dates wrong when I posted this. The Contrast blog post and presentation are from 2012, it is the award that is from 2013:
In case you missed it OWASP's long time contributor Aspect Security were at Java One conference in presenting their (commercial) product Contrast.
I was not there, but from the noises I'm hearing it was quite a successull event, with lots of developers reached.
Here is a cool picture from their Contrast @ JavaOne post (which contains a link to their presentation (also embedded below));
In case you missed it OWASP's long time contributor Aspect Security were at Java One conference in presenting their (commercial) product Contrast.
I was not there, but from the noises I'm hearing it was quite a successull event, with lots of developers reached.
Here is a cool picture from their Contrast @ JavaOne post (which contains a link to their presentation (also embedded below));
Labels:
OWASP
Monday, 23 September 2013
Chaos Computer Club breaks Apple TouchID (the bad idea that is fingerprint biometrics and 'its cool to hack Apple now')
Well it didn't took long: Chaos Computer Club breaks Apple TouchID
For me the key statement of that post is: "We hope that this finally puts to rest the illusions people have about fingerprint biometrics. It is plain stupid to use something that you can´t change and that you leave everywhere every day as a security token"
I have to say that I have never been involved in designing or testing fingerprint biometrics, but I always had this voice in the back on my head saying "...humm... it really doesn't sound good the idea that the security ID cannot be changed, and once that ID is stored in digital format, there is nothing that can be done to prevent its reuse...."
For me the key statement of that post is: "We hope that this finally puts to rest the illusions people have about fingerprint biometrics. It is plain stupid to use something that you can´t change and that you leave everywhere every day as a security token"
I have to say that I have never been involved in designing or testing fingerprint biometrics, but I always had this voice in the back on my head saying "...humm... it really doesn't sound good the idea that the security ID cannot be changed, and once that ID is stored in digital format, there is nothing that can be done to prevent its reuse...."
Labels:
Security
OWASP Flight Booking using Amex and Project's Mini-Summit at OWASP AppSec USA 2013
I just booked my flight using the new OWASP 'Amex travel' partnership and it was a great experience
Labels:
OWASP
Guidelines of OWASP
OWASP got a great quote on this EU Regulations document which is aimed at laying down technical specifications for online collection systems pursuant to Regulation (EU) No 211/2011 of the European Parliament and of the Council on the citizens’ initiative)
Labels:
OWASP
Wednesday, 18 September 2013
Video: Coding WebInspect in real-time to Inject Fortify Plugin Views
Here is a detailed video that shows the multiple steps required to inject windows originally hosted in Eclipse (Java process) into WebInspect (.NET process).
Of course that this workflow could be automated using a script, but I hope that the video below helps to explain how it is actually works, and how windows are hijacked from one process into another:
Of course that this workflow could be automated using a script, but I hope that the video below helps to explain how it is actually works, and how windows are hijacked from one process into another:
Labels:
Fortify,
TeamMentor,
WinAPI
Two Videos showing TeamMentor Eclipse Plugin integration with Fortify Eclipse Plugin (as shown in HP Protect 2013 conference)
Here are main videos shown at the HP Protect 2013 conference.
This is our first working version of an TeamMentor Eclipse plug-in that is able to show security guidance natively on Eclipse.
This is our first working version of an TeamMentor Eclipse plug-in that is able to show security guidance natively on Eclipse.
Labels:
Fortify,
TeamMentor
Injecting Fortify Eclipse Plug-in Views into Notepad and WebInspect (and key difference between Fortify content and TeamMentor content)
Following from Opening up a native Chrome Browser window inside Eclipse (raw version) and Injecting HP Fortify Eclipse Plug-in Views into HP’s WebInspect UI here are a couple more examples of how to reuse Fortify Eclipse Plug-in Views into other processes.
Example 1: WebInspect with Fortify and TeamMentor (inside Chrome)
Example 1: WebInspect with Fortify and TeamMentor (inside Chrome)
Injecting HP Fortify Eclipse Plug-in Views into HP’s WebInspect UI
Using the O2’s Win32 Window Hijacking capabilities (see also Opening up a native Chrome Browser window inside Eclipse (raw version)) , here is a PoC on how to inject a couple Eclipse Views from the HP Fortify Eclipse plug-in (which is Java app running under an JVM) into the HP WebInspect UI (which is .NET app running under an CLR).
The power of this PoC is to show that we can have the best of both worlds and show security consultants and developers the best possible environment/UI for them to analyze, review and fix security vulnerabilities.
The power of this PoC is to show that we can have the best of both worlds and show security consultants and developers the best possible environment/UI for them to analyze, review and fix security vulnerabilities.
Opening up a native Chrome Browser window inside Eclipse (raw version)
On the Win32 Window’s Hijack theme, here is a raw version of how to show an actual Chrome browser window inside an Eclipse view (ie. a window from a C++ process inside a JVM-based Process).
Using the Groovy execution capabilities described in the Programming Eclipse in Real-Time (using an 'Groovy based' Eclipse Plug-in) post, in Eclipse, I start by creating an instance of a SWT panel and get its handle:
Using the Groovy execution capabilities described in the Programming Eclipse in Real-Time (using an 'Groovy based' Eclipse Plug-in) post, in Eclipse, I start by creating an instance of a SWT panel and get its handle:
Using IKVM on a Apache Derby Database
After creating the .Net version of the Derby dlls using:
Labels:
IKVM
Saturday, 14 September 2013
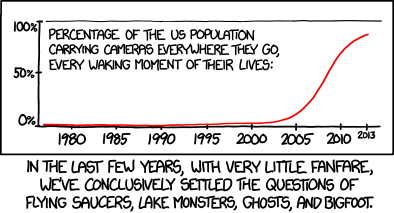
No more UFOs :)
Great post from Seth: Cell phone cameras repel UFOs which points to this XKCD cartoon:
On the topic of 'devices' being carried by everywhere, I wonder how long until we'll find out how easy it is (or not) for 3rd parties (NSA, criminals, etc...) to remotely enable a mobile/laptop microphone and push the captured data (in real-time or not) into an external location :)
Labels:
Funny
Microsoft should sell Fully Patched Windows XP licenses (or open source it)
Microsoft should sell Windows XP because its newer operating systems should be so much better than Windows XP that its customers would be happy to buy the newer versions.
Labels:
Philosophy,
Simple Microsoft
May the 'Farm' be with you - Grocery Store Wars (2005)
This is a funny video from 2005 which talks about a very important topic in a really cleaver way
Labels:
Funny,
Philosophy
Wednesday, 11 September 2013
Running Groovy natively in .NET using IKVM
I’m really getting into Groovy (see also Programming Eclipse in Real-Time (using an 'Groovy based' Eclipse Plug-in)), but one problem is that Groovy runs natively on the JVM!
And although I could use Jni4Net to create a bridge between a JVM and the CLR, it would be much nicer if I could write Groovy scripts under the CLR (with live access the FluentSharp APIs and O2 created objects).
And by using IKVM I was able to do exactly that :)
I was able to convert the main Groovy jar JVM bytecode into .NET CLR bytecode, and evaluate Groovy scripts directly in C# (i.e. without a JVM loaded in the current process). For more O2 usage of the amazing IKVM API's see Util - O2 Java Tools (IKVM Based) v1.0
Evaluating an Groovy script in .NET:
After created the groovy-all-2.1.6.dll .Net IKVM dll (see Appendix 1) Creating groovy-all-2.1.6.dll below), I was able to consume it (in O2’s C# REPL) like this:
And although I could use Jni4Net to create a bridge between a JVM and the CLR, it would be much nicer if I could write Groovy scripts under the CLR (with live access the FluentSharp APIs and O2 created objects).
And by using IKVM I was able to do exactly that :)
I was able to convert the main Groovy jar JVM bytecode into .NET CLR bytecode, and evaluate Groovy scripts directly in C# (i.e. without a JVM loaded in the current process). For more O2 usage of the amazing IKVM API's see Util - O2 Java Tools (IKVM Based) v1.0
Evaluating an Groovy script in .NET:
After created the groovy-all-2.1.6.dll .Net IKVM dll (see Appendix 1) Creating groovy-all-2.1.6.dll below), I was able to consume it (in O2’s C# REPL) like this:
Labels:
Groovy,
O2 Platform
Consuming password protected TeamMentor Articles using REST GET APIs (and creating mini-tool to view article's data)
As described by the TeamMentor’s CX integration requires TM instance that is serving the content to be open to anonymous access issue, there are times when programmatic access is needed to password protected TeamMentor articles.
Let’s take for example the Add Unique Tokens to HTTP Requests Using ESAPI article, which has the 7d647e95-e47f-42e3-bb84-fd0dd727245c GUID, and can be opened directly at https://teammentor.net/article/7d647e95-e47f-42e3-bb84-fd0dd727245c (free account is needed to see that link)
Let’s take for example the Add Unique Tokens to HTTP Requests Using ESAPI article, which has the 7d647e95-e47f-42e3-bb84-fd0dd727245c GUID, and can be opened directly at https://teammentor.net/article/7d647e95-e47f-42e3-bb84-fd0dd727245c (free account is needed to see that link)
Labels:
TeamMentor
Tuesday, 10 September 2013
Example of using GitHub Pull Requests to merge changes made on Branches
After the fixes explained in the Git Flow - Moving patches from one Commit into another Commit post and the reset of the TeamMentor 3.4 branch, Michael reapplied his other changes/fixes to the correct 3.4 commit, and I’m now in the process merging his Pull Requests into the 3.4_Release branch (and eventually into the master branch).
This post walks through my current workflow.
At the moment there are a number of Pull Requests to process:
This post walks through my current workflow.
At the moment there are a number of Pull Requests to process:
Labels:
Git,
GitHub,
TeamMentor
Saturday, 7 September 2013
Do you use the O2 Platform? (and O2 page at ohloh.net)
I just updated the O2 Platform project page at OHLOH see https://www.ohloh.net/p/o2platform and if you use it, please register your interest :)
Note that the stats only include the main O2 Platform code and the commits made to GitHub (the multiple O2 Forks and past SVN stats are not there)
Note that the stats only include the main O2 Platform code and the commits made to GitHub (the multiple O2 Forks and past SVN stats are not there)
Labels:
O2 Platform
Thursday, 5 September 2013
Git Flow - Moving patches from one Commit into another Commit
This (longish) post will cover detailed git workflows and is part of the series of blog posts that show how we use the Git Flow workflow to manage TeamMentor's source code (you will also see practical applications of GitHub's powerful of powerful features like Network Graphs and Pull Requests).
The key problem that we are going to solve, is the situation created by Michael Hidalgo’s TeamMentor fixes/commits/branches that were done against an commit (38bfcd54d8046372c0ace2409324ecc965761504) which was originally planed to be part of the next release, but we decided that the next 3.4 Release of TeamMentor will be based on the current 3.3.3 version (with is based on the earlier commit: b97a470ffa173d67a9c74373593eea03eb7a2da4).
The key reason is that he 38bfcd54d8046372c0ace2409324ecc965761504 commit (currently the parent of Michael’s fixes/branches) is not stable and is going now to be the basis of the 3.5_Release (this code contains a number of big changes which need more TLD and testing: native ASP.NET MVC routing, better Git support, native Markdown editor, depreciation of HTML WYSIWYG editor, and more)
In a nutshell, we need to re-apply Michael’s bug fixes to an earlier commit than the one used (i.e. backport those commits).
The key problem that we are going to solve, is the situation created by Michael Hidalgo’s TeamMentor fixes/commits/branches that were done against an commit (38bfcd54d8046372c0ace2409324ecc965761504) which was originally planed to be part of the next release, but we decided that the next 3.4 Release of TeamMentor will be based on the current 3.3.3 version (with is based on the earlier commit: b97a470ffa173d67a9c74373593eea03eb7a2da4).
The key reason is that he 38bfcd54d8046372c0ace2409324ecc965761504 commit (currently the parent of Michael’s fixes/branches) is not stable and is going now to be the basis of the 3.5_Release (this code contains a number of big changes which need more TLD and testing: native ASP.NET MVC routing, better Git support, native Markdown editor, depreciation of HTML WYSIWYG editor, and more)
In a nutshell, we need to re-apply Michael’s bug fixes to an earlier commit than the one used (i.e. backport those commits).
Labels:
Git,
GitHub,
TeamMentor
Subscribe to:
Posts (Atom)