Recently I have been acting as 'head of Application Security' for a couple UK companies, and one of my most effective actions has been to setup the JIRA workflow that you can see below.
The key to this workflow (and the secret of its success) is the action to get the business owners to click on the 'Accept Risk' button.
That simple action makes the whole difference, since that is the moment that a particular RISK become REAL.
Now, the responsibility/decision/liability of NOT fixing an issue, is clearly mapped to an individual (which in some cases can even be the CTO).
Note that the definition of 'not fixing' should be 'will not be fixed in the next couple weeks'
A personal blog about: transforming Web Application Security into an 'Application Visibility' engine, the OWASP O2 Platform, Application/Data interoperability and a lot more
Friday, 4 December 2015
Paying OWASP Leaders and some ideas on how OWASP should be supporting its projects
(based on an email to the owasp-leaders list)
The reasons why I believe OWASP should not be allowed to pay owasp leaders are listed here http://blog.diniscruz.com/2012/04/why-owasp-cant-pay-owasp-leaders.html
The reasons why I believe OWASP should not be allowed to pay owasp leaders are listed here http://blog.diniscruz.com/2012/04/why-owasp-cant-pay-owasp-leaders.html
And since I have not been on the OWASP board for about 5 years, I think we need to realise that IF it was possible to pay owasp leaders to work on OWASP projects, THAT (paying owasp leaders) would have happened by now (after all, there has been enough budget to make that happen)
The problem is that there is still this 'idea' that "IF ONLY we could do that (pay owasp leaders) amazing stuff would happen".
Labels:
OWASP
Request for OWASP board to approve 100K for a project Summit in 2016
(sent to the OWASP leaders list in early Dec 2015, following the original request made in June 2015)
Bumping this thread, since I believe not much has happened since.
Bumping this thread, since I believe not much has happened since.
I would like to request again for "OWASP board to approve 100K for a project Summit in 2016. And then ask for a team or OWASP leaders to lead that effort"
Labels:
OWASP
Proposed new strategy for OWASP projects - They are Research Projects
(variation of an email send to the owasp leaders list)
I think a key problem is the expectation that OWASP should ever be able to develop professional, best in class and 'secure' apps.
I think a key problem is the expectation that OWASP should ever be able to develop professional, best in class and 'secure' apps.
These conversations always tend to have a base on the idea that OWASP 'should not have a lot of projects' and 'only focus on a couple high-value/high-quality ones'. This never gains traction because that goes completely the model and culture of OWASP projects.
The reality is that really good a solid projects at OWASP are the exception and the outliers.
Labels:
OWASP
Monday, 9 November 2015
Do you deserialize Java objects? Jenkins zero day and vunls in WebLogic, WebSphere, JBoss, OpenNMS and Appache commons
Last week the What Do WebLogic, WebSphere, JBoss, Jenkins, OpenNMS, and Your Application Have in Common? vulnerability research was published and it included a number of quite worrying exploits on Java apps, more specifically on apps that use the Apache commons library (update: it looks like this is not a vuln in Apache commons, but in how it is used).
This is following up the Java Deserialization research published earlier this year on Marshalling Pickles and Exploiting Deserialization Vulnerabilities in Java (which is a variation of the XStream/XMLDecoder vulns/research I was involved in 2013)
It also looks like the Jenkins issue mentioned in the latest research doc is a zero-day on Jenkins: Mitigating unauthenticated remote code execution 0-day in Jenkins CLI
Since this is a vulnerability that allows RCE (Remote Code Execution), it is really important to understand the internal/external exposure to java deserialization, Jenkins and apache commons usage.
This is following up the Java Deserialization research published earlier this year on Marshalling Pickles and Exploiting Deserialization Vulnerabilities in Java (which is a variation of the XStream/XMLDecoder vulns/research I was involved in 2013)
It also looks like the Jenkins issue mentioned in the latest research doc is a zero-day on Jenkins: Mitigating unauthenticated remote code execution 0-day in Jenkins CLI
Since this is a vulnerability that allows RCE (Remote Code Execution), it is really important to understand the internal/external exposure to java deserialization, Jenkins and apache commons usage.
Labels:
Java,
Security,
XmlDecoder,
XStream
Monday, 2 November 2015
Four amazing years and good luck TM 4.0
After working very hard on multiple versions of TeamMentor (TM 2.0, 3.0, 3.5 and 4.0), the time has finally come for me to let TM go, and move my Application Security efforts in other directions.
The last 4 years at SI have been an amazing experience and I've learned a lot.
Not only I increased my development skills (.NET, Java, Eclipse, Node, Javascript), I finally understood what TDD is all about and where security fits within the SDLC.
I really want to thank Ed and Jason for the opportunity, and the amazing worldwide TM development team (Serge, Michael, Lucy, Roman, Salle) for making TM 4.0 a reality.
I'm sure mine and SI paths will meet again. In fact I'm still contributing a couple bug fixes to TM, so I'm still around :)
Good luck to SI and all the team
PS: In case you are curious, I'm now helping UK companies to set up their Application Security Programmes (i.e. I'm a part-time 'Head of Application Security')
The last 4 years at SI have been an amazing experience and I've learned a lot.
Not only I increased my development skills (.NET, Java, Eclipse, Node, Javascript), I finally understood what TDD is all about and where security fits within the SDLC.
I really want to thank Ed and Jason for the opportunity, and the amazing worldwide TM development team (Serge, Michael, Lucy, Roman, Salle) for making TM 4.0 a reality.
I'm sure mine and SI paths will meet again. In fact I'm still contributing a couple bug fixes to TM, so I'm still around :)
Good luck to SI and all the team
PS: In case you are curious, I'm now helping UK companies to set up their Application Security Programmes (i.e. I'm a part-time 'Head of Application Security')
Labels:
Security,
TeamMentor
Thursday, 29 October 2015
How to detect SQL Injection at SQL Server level (via SQL Errors)
Question: how to detect SQL injection on an high-volume SQL Server just by looking at SQL Queries errors?
I know some guys (like ETSY) are doing this, but when I was talking with some MS SQL Server DBAs today, they couldn't find an easy way to do it at the SQL server.
The logic is that there should be no SQL compilation errors in an Production SQL server, so any errors that occur, must be:
Labels:
Security
Monday, 19 October 2015
What are Security Champions and what do they do?
Security Champions are a key element of an AppSec team, since they create an cross-functional team focused on Application Security
Here is an good definition for you to customise to your culture and workflows:
What is an Security Champion?
- Security Champions are active members of a team that may help to make decisions about when to engage the Security Team
- Act as the "voice" of security for the given product or team
- Assist in the triage of security bugs for their team or area
What do they do?
- Actively participate in the AppSec JIRA and WIKI
- Collaborate with other security champions
- Review impact of 'breaking changes' made in other projects
- Attend weekly meetings
- Are the single point of contact for their assigned team
- Ensure that security is not a blocker on active development or reviews
- Assist in making security decisions for their team
- Low-Moderate security impact
- Empowered to make decisions
- Document decisions made in bugs or wiki
- High-Critical security impact
- Work with AppSec team on mitigations strategies
- Low-Moderate security impact
- Help with QA and Testing
- Write Tests (from Unit Tests to Integration tests)
- Help with development of CI (Continuous Integration) environments
Further reading
Labels:
Security,
Security Champions
Wednesday, 14 October 2015
Mapping the attack surface for client side code (i.e. JS code)
Although at first it might look that on a browser the concept of attack surface doesn’t matter, unless you are building a pure html website with NO Javascript, you will also need to consider the attack surface of your code.
The attack surface is basically the ways the code execution can be affected/influenced by an attacker’s data/actions
For Javascript code that is running on browser there are three main sources of malicious data
Saturday, 25 July 2015
500 USD budget available for Google Cloud use by OWASP Projects
(below is an email I just sent to the owasp-leaders list about the 500 USD budget I requested from the 'OWASP budget available for OWASP projects')
OWASP leaders, FYI we now have a 500 USD budget approved to spend on Google Cloud (some more details on the thread below).
OWASP leaders, FYI we now have a 500 USD budget approved to spend on Google Cloud (some more details on the thread below).
This is basically open to any OWASP leader to use on OWASP projects.
Part of the idea is to figure out good use cases of using cloud resources (like the ones provided by Google Cloud) on OWASP projects
I've setup an Slack channel to talk about this and to manage its use: https://owasp.slack.com/archives/projects-in-cloud
If you want access to the admin console (for example to setup your linux/docker/windows VM) drop me, Fabio or Matt (ideally via Slack) a simple email and we'll add you to the cloud users ground.
This is early days of this experiment and we still need to create a couple Rules of Engagement and scripts to manage the environment, so if you want to be involved in that part of the action it would help to make this resource available to a wider community.
As a example of the kind of usage that OWASP projects can have of these Google Cloud resources, based on a recent thread on the O2 Platform mailing list (How-To Request: Running Real Time feedback inside Visual Studio with C# REPL) we are setting up a Windows VM with VisualStudio 2010
Labels:
OWASP
Wednesday, 1 July 2015
UnitTest to auto reload a compiled jade template (with angularJS written in CoffeeScript)
Here is a jade template that is being autocompiled into html (using gulp) which uses coffee-script to create the AngularJS app/controller.
Monday, 29 June 2015
Some comments on jQuery security and our current development stack (based on Node, CoffeeScript, Jade and AngularJS)
Following from Why we are going to use AngularJs 1.3 on TM ...
On jQuery, my experience (in both developing and reviewing jQuery apps) is that it tends to promote an 'lets just hack it to make it work' kind of development workflow. In jQuert code, there are always tons of DOM manipulations, which will always include (browser specific and other) hacks, and create code with quite a lot of dependencies and lack-of-isolation between components. Basically you shown me an large jQuery app (like the one we developed) and It most likely be an app hard to refactor, hard to maintain and hard to understand what really is going on (ironically the power of jQuery tends to create this stuff, since it is always possible to 'fix something' by adding a bit of jQuery somewhere).
And of course jQuery is also a nightmare from a security point of view, since there are quite a lot of sinks that will transform strings into code.
In order to make TeamMentor secure and easy to code we are using the following stack/technologies:
Sunday, 28 June 2015
Why we are going to use AngularJs 1.3 on TM (vs ReactJs)
(As posted on the Angular JS vs React in Flare issue)
For reference I just had another look at ReactJS vs AngularJS and here are the reasons why I think we should keep on the current path and use Angular on TM 4.0
For reference I just had another look at ReactJS vs AngularJS and here are the reasons why I think we should keep on the current path and use Angular on TM 4.0
- Angular 1.3 is an MVC framework with really good support for: Controllers, Services and Views (React on its own admission is mainly focused on the 'View' component)
- Angular 2.0 seems to contain most of the big advantages currently mapped to React, so although the jump from Angular 1.3 to 2.0 seems to be quite steep, it will allow us to have access (if needed) to the current perceived React advantages
- It seems that one of the big advantages of React is it speed, and I don't think we will need that kind of DOM manipulation speed anytime soon (since we will be using the server-side graphdb for that)
- Most comparisons on Angular vs React seem to:
- a) conclude that React is better
- b) be written by users that did not had a lot of experience with AngularJS, and I would say with a lot of experience of jQuery (note that If I get my way we will NOT be using jQuery on TM 4.0 (i.e. it is a banned API :) ))
- c) focus on simple scenarios (where Angular might be overkill)
- d) complain about Angular 'complexity' (which again implies not very deep Angular knowledge)
- e) don't cover how to test Angular/React
- There are not a lot of published books about React (with the first ones coming out at the end of 2015). Compare this with the dozen books written about Angular
- The current TM dev team already has good knowledge of Angular (specially since we use it on TM 3.5)
- AngularJS security seems more mature than React (note for example the use of CSP) and documentation about it
- I quite like how AngularJS Javascript looks like (specially when written in CoffeeScript) vs ReactJS Javascript which does seem to contain a lot more DOM manipulation (ie. just like jQuery). Of course that on this one I'm bias for Angular because I know more Angular than React :)
Labels:
AngularJS
Friday, 26 June 2015
Angular 1.4 with Jade with coffee (all in one file)
Simple example of using all these technologies together :)
Labels:
AngularJS,
Coffee-Script,
Jade
Saturday, 23 May 2015
Looking at ElasticSearch, Kibana and LogStash
Which look like a really powerful way to capture and visualise data. Here are the best links I found on the topic (i.e. tabs that I had open)
Labels:
Security,
Visualization
Thursday, 21 May 2015
Thoughts on Security Authentication and on adding security into an SDL
Here is an (slightly edited) 'brain dump' I just wrote on the topic of Authorisation and SDL.
Let me know what are your views on the ideas presented below:
---------------------------------------------------------------------
Let me know what are your views on the ideas presented below:
---------------------------------------------------------------------
The need for a strong Auth strategy
Knowing 'who is talking to whom' is a key pillar of security. Since there is going to be a number of parties and players involved, it will not be possible to have a one-size-fits-all Authentication technology/workflow (specially when dealing with the partner's systems and existing SSO technology).
Labels:
Ideas,
Security,
Security Champions
Teach kids how to code by solving their own Maths problems
When i was participating the Hack the Curriculum event last month I realised that we risk doing to coding what we have done to Maths (see A Mathematician's Lament: How School Cheats Us Out of Our Most Fascinating and Imaginative Art Form, available as pdf or book)
We are trying to teach kids how to code in an abstract and 'technical' way, instead of letting them use programming to make the computer do 'something' (which is exactly how most of us learned how to code)
Teaching kids what is a variable, or a function, or an algorithm, is not going to make any sense to them, since those are just 'techniques' into achieving something. The reason kids love Scratch is because it makes programming/coding much more practical and real.
When I was thinking about what else could we use to teach kids how to code, I had my epiphany when I thought about the fact that Kids already solve complex programming problems everyday!!!
It's called MATHS.
We are trying to teach kids how to code in an abstract and 'technical' way, instead of letting them use programming to make the computer do 'something' (which is exactly how most of us learned how to code)
Teaching kids what is a variable, or a function, or an algorithm, is not going to make any sense to them, since those are just 'techniques' into achieving something. The reason kids love Scratch is because it makes programming/coding much more practical and real.
When I was thinking about what else could we use to teach kids how to code, I had my epiphany when I thought about the fact that Kids already solve complex programming problems everyday!!!
It's called MATHS.
Labels:
Education
Wednesday, 20 May 2015
Can you deliver this 3 day C++/Java course in the UK?
I was asked to deliver the course below in the UK but it is too structured for my style of training and I don't have the time to delivered it.
So if you have the skills and can do it, ping me and I'll put you in touch with the company organising it
So if you have the skills and can do it, ping me and I'll put you in touch with the company organising it
Labels:
Contract Work
My C++ experience, the power of blogs and 'the online brand of an developer'
If you are a developer one of the most powerful things you can do for your carer is to have a solid online 'brand'.
Don't think of it as a place where you tell the world how amazing you are, but as a place where you keep a log of your past ideas and achievements.
In fact, your GitHub account is the place where your skills will be displayed in its purest format, so make sure you have a nice active and healthy presence.
Below you will find the contents of an email I just sent after I was asked 'So ... what is your C++ experience?', and note the difference between the period before and after I starter blogging (i.e links vs no-links)
And the worse part, is that not only I did not share those ideas with you (blog reader), I am also left of out it! (since those ideas and docs and now lost in old memories and laptops/vms long gone)
See Blogging is like speaking to my 'Future Self' for more on the idea that blogging is more about allow you in the future to have access to your ideas today
Don't think of it as a place where you tell the world how amazing you are, but as a place where you keep a log of your past ideas and achievements.
In fact, your GitHub account is the place where your skills will be displayed in its purest format, so make sure you have a nice active and healthy presence.
Below you will find the contents of an email I just sent after I was asked 'So ... what is your C++ experience?', and note the difference between the period before and after I starter blogging (i.e links vs no-links)
And the worse part, is that not only I did not share those ideas with you (blog reader), I am also left of out it! (since those ideas and docs and now lost in old memories and laptops/vms long gone)
See Blogging is like speaking to my 'Future Self' for more on the idea that blogging is more about allow you in the future to have access to your ideas today
Labels:
Security
OWASP and O2 Platform on Slack
There is a new Slack for OWASP https://owasp.slack.com which you can join using the invite at http://owasp.herokuapp.com
In there you will find the https://owasp.slack.com/messages/project-o2 which can be used for all sort of O2 questions and scripts developments :)
See you there
In there you will find the https://owasp.slack.com/messages/project-o2 which can be used for all sort of O2 questions and scripts developments :)
See you there
Labels:
OWASP
Published to Github Security-Research repo the files I had on DropBox Share
 Since dropbox is still refusing to ...
Since dropbox is still refusing to ...a) host the pdfs I shared (and linked from this blog)
b) let me know which files are the offending ones (see image on right for error show)
... I've just moved all those files into GuiHub
You can get them from https://github.com/DinisCruz/Security-Research/tree/master/O2%20Raw%20Docs
Below is a list of files uploaded. Lots of it is is quite raw format, but there are some good nugets of research in there :)
Sunday, 10 May 2015
Writing Unit Tests in Bash using BATS
Since every code we write should have Tests, here is a good tool to test bash scripts:
- https://github.com/vim-scripts/bats.vim
- https://blog.engineyard.com/2014/bats-test-command-line-tools
- https://github.com/duggan/pontoon/blob/master/.travis.yml (example of how to use it with travis)
- http://www.kinnetica.com/2011/05/29/using-screen-on-mac-os-x/ (used to split the screen and see both vim editor and shell execution at the same time)
Labels:
Unit Tests
Thursday, 7 May 2015
Making users the 'client' not the product (becoming an 'Data Guardian')
There is space in the market for a company to become an Data Guardian for the digital trails and activities created everyday by everybody that users the Internet.
This would be a service provided to the end user (person or company) that would store and anonymize the user's data (as stored or used by 3rd party services), in a way that the user would be able to control who, what, how and when their data is shared and used.
In practice this means that the user would stop being 'the product' (whose data is used and sold without his/her control), and would become 'the customer' (able to control/manage its own data).
This would be a service provided to the end user (person or company) that would store and anonymize the user's data (as stored or used by 3rd party services), in a way that the user would be able to control who, what, how and when their data is shared and used.
In practice this means that the user would stop being 'the product' (whose data is used and sold without his/her control), and would become 'the customer' (able to control/manage its own data).
Labels:
Philosophy,
Security
Tuesday, 21 April 2015
Secure coding in a SCRUM cloud (for UK Azure User Group)
Next Monday (27th of April) I'm presenting at the UK Azure User Group in London on the topic of: Secure coding in a SCRUM cloud
 You can see on the Research on Azure WebSite security: Process Execution (cmd.exe, git.exe, node.exe, xyz.exe) and Folder Browsing (outside azure root) post what I presented last time (July 2013)
You can see on the Research on Azure WebSite security: Process Execution (cmd.exe, git.exe, node.exe, xyz.exe) and Folder Browsing (outside azure root) post what I presented last time (July 2013)
This time around I'm going to focus more on secure coding, real-time unit test execution, continuous deployment, static analysis, and real-time code scanning (for example Real-Time Vulnerability Feedback in VisualStudio)
Hopefully I will also have an new version of the O2 Platform to show :)
If you are around London (from 7 till 10), please join us.
You can RSVP at: http://www.meetup.com/UKAzureUserGroup/events/220849015/
 You can see on the Research on Azure WebSite security: Process Execution (cmd.exe, git.exe, node.exe, xyz.exe) and Folder Browsing (outside azure root) post what I presented last time (July 2013)
You can see on the Research on Azure WebSite security: Process Execution (cmd.exe, git.exe, node.exe, xyz.exe) and Folder Browsing (outside azure root) post what I presented last time (July 2013)This time around I'm going to focus more on secure coding, real-time unit test execution, continuous deployment, static analysis, and real-time code scanning (for example Real-Time Vulnerability Feedback in VisualStudio)
Hopefully I will also have an new version of the O2 Platform to show :)
If you are around London (from 7 till 10), please join us.
You can RSVP at: http://www.meetup.com/UKAzureUserGroup/events/220849015/
Labels:
Azure,
London,
O2 Platform
Tuesday, 14 April 2015
London Hack the Curriculum - focused on for key Stage 3 Computing curriculum (11-13 years old kids)
Check this out, https://www.eventbrite.co.uk/e/hack-the-curriculum-and-include-birthday-celebration-tickets-15351043384
This looks like an really interesting event, and a great way to help to shape the next generation of coders :)
I'm planning to attend, so if you have any good ideas on how we (OWASP or AppSec industry) can help, let me know and I'll relay those ideas
This looks like an really interesting event, and a great way to help to shape the next generation of coders :)
I'm planning to attend, so if you have any good ideas on how we (OWASP or AppSec industry) can help, let me know and I'll relay those ideas
Labels:
Education
Sunday, 8 February 2015
On the current OWASP Project Summit efforts (in Feb 2015)
It's really hard to create an OWASP Project Summit with the current model (with little funding, with no dedicated team, attached to a conference, etc..)
The formula that worked in the past was to start with a set budget (lets say 50k to 100k) and :
- use those funds to make sure the key players (in this case project leaders and 'new players') are going to attend (by offering to cover all travel and accommodation expenses (while asking them if they can get their employee to pay instead))
- hire a dedicated summit team (for that period)
- secure dedicated venue and summit resources
- generate a huge amount of energy about the summit sessions (starting by inventing all sorts of sessions, until the real sessions become solid)
- cast a very wide net of 'invitations to attend the summit' (with the vision that 'the summit is THE place to be, where all the key players will be in the same location, and where REAL work can be done')
Labels:
OWASP
Saturday, 24 January 2015
Real-Time code coverage in NodeJS app using Atom
Here is my current dev environment on Atom's Editor where I am able to have quasi-real-time (i.e. in about 1s to 2s) feedback on the test executed and its code coverage
For example here is what I see when there is a test failing:
For example here is what I see when there is a test failing:
- note the red dots on the left (after line 44)
- note the error message right (where '1.2' is not'1.3')
- code coverage is at 92.50%
Labels:
Atom,
Code Coverage,
Testing
Sunday, 18 January 2015
Does your team has a Security Champion? If not, get this Mug and Library
If your dev team doesn't have an assigned security team champion, get one of these Mugs :)
Basically that 'Security Expert' Mug should represent the fact that at the moment when a developer has an Application Security question, he might as well ask the dude on that Mug for help :)
I also like that it re-enforces the idea, that for most developer teams, just having somebody assigned to application security, is already a massive step forward!!
I also like that it re-enforces the idea, that for most developer teams, just having somebody assigned to application security, is already a massive step forward!!
Labels:
Security Champions
Saturday, 17 January 2015
Thinking and coding in Graphs, some screenshots of last 6 months
In the past 6 months I have been working on TeamMentor 4.0 (new version) which is based on a graph database and written in node.
I was cleaning up my desktop today and found the images below which represent the multiple experiments I have been doing in ways to visualise the content data we have.
This is quite a raw dump, but if you would like some descriptions about what each one means (and believe me that each one as nice story behind), let me know and I'll write more about them
I was cleaning up my desktop today and found the images below which represent the multiple experiments I have been doing in ways to visualise the content data we have.
This is quite a raw dump, but if you would like some descriptions about what each one means (and believe me that each one as nice story behind), let me know and I'll write more about them
Labels:
Graphs,
TeamMentor
Sunday, 11 January 2015
So why can't I in 2015 write a post in Blogger using Markdow (and paste screenshots)
I just wrote this [Atom Editor] How to run tests from a loaded package using GitHub's Issue UI, and it was a great writing experience (and a real-time preview like discourse would had made it even better)
But I can't post it here!!! Because Blogger does not support markdown!!!
Talk about not keeping up the pace of innovation
What this really means is that I'm getting closer and closer to moving this blog into another platform (the question is which one?)
But I can't post it here!!! Because Blogger does not support markdown!!!
Talk about not keeping up the pace of innovation
What this really means is that I'm getting closer and closer to moving this blog into another platform (the question is which one?)
Labels:
Rant
Thursday, 8 January 2015
FluentSharp, FluentNode or NWR needs your help
If you are into C# take on an issue from https://github.com/o2platform/FluentSharp/issues
If you are into NodeJS take on an issue from https://github.com/o2platform/FluentNode/issues
If you are into Chrome or Selenium take on an issue from https://github.com/O2Platform/nwr/issues
Thanks :)
If you are into NodeJS take on an issue from https://github.com/o2platform/FluentNode/issues
If you are into Chrome or Selenium take on an issue from https://github.com/O2Platform/nwr/issues
Thanks :)
Labels:
Chrome,
FluentNode,
FluentSharp
Achieving 98% Code Coverage, by running mocha Web Automation Tests in Chrome (from WebStorm)
Here is what the high-productive Node + Chrome TDD test environment (that I use every day) looks like, when executing the TM_4_0_QA UI Automation tests
This is the setup that allows me to have 98% to 100% code coverage (see The quest for 100% Code Coverage, the 96cc idea and 'apps with low CC must be insure' for more details)
The Chrome window on the right is powered by O2 Platform's NWR project
The use of WebStorm is not required for the tests to run, since the same result can be achieved by running npm test from the console.
Video: Running mocha Web Automation Tests in Chrome (from WebStorm)
This is the setup that allows me to have 98% to 100% code coverage (see The quest for 100% Code Coverage, the 96cc idea and 'apps with low CC must be insure' for more details)
The Chrome window on the right is powered by O2 Platform's NWR project
The use of WebStorm is not required for the tests to run, since the same result can be achieved by running npm test from the console.
Video: Running mocha Web Automation Tests in Chrome (from WebStorm)
Labels:
FluentNode,
TeamMentor,
Unit Tests
Thursday, 1 January 2015
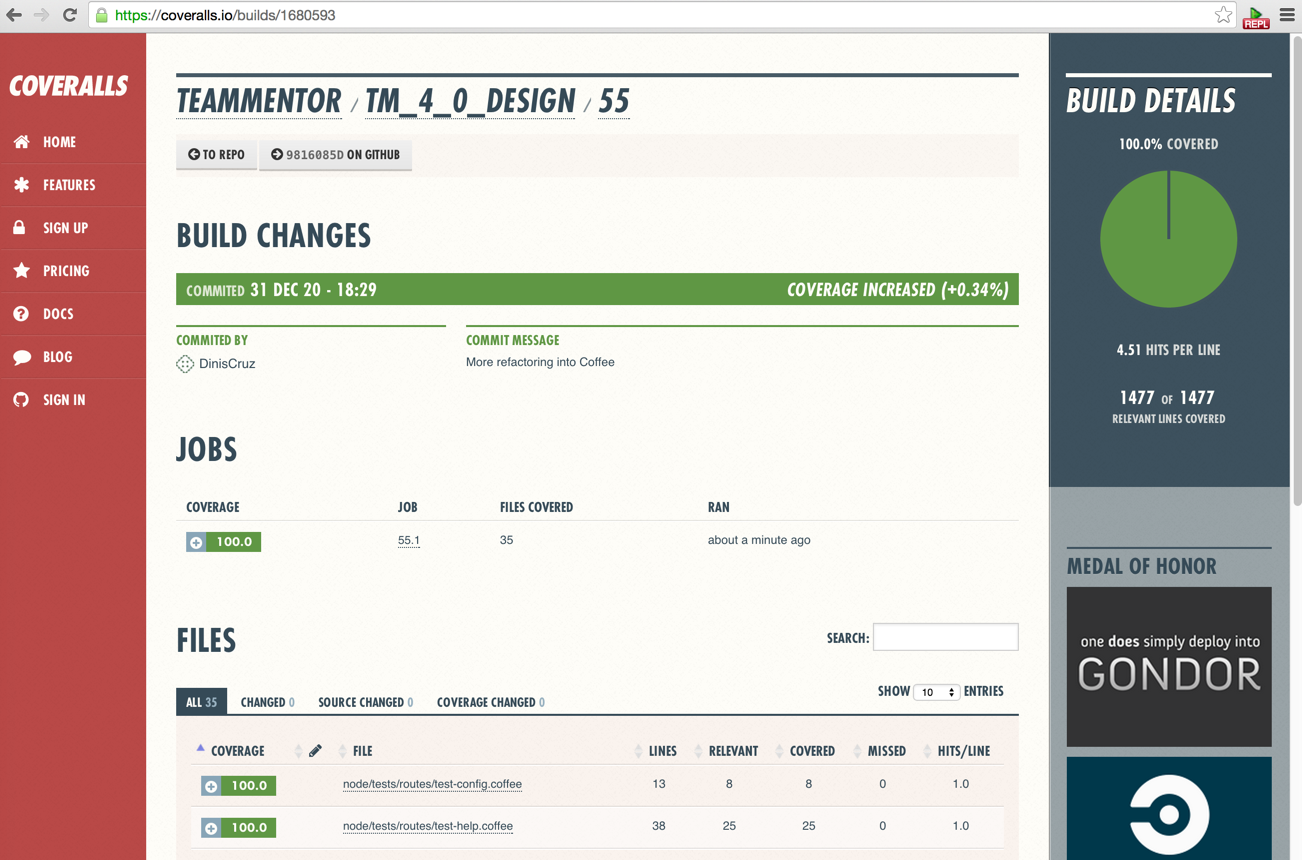
The quest for 100% Code Coverage, the 96cc idea and 'apps with low CC must be insure'
I've spent the last day improving the UnitTest coverage of TM_4_0_Design and since this codebase as been developed with a nice TDD workflow, after a bit of code-cleanup and refactoring I was able to achieve 100% Code Coverage :)
Labels:
TeamMentor,
Unit Tests
Subscribe to:
Posts (Atom)