Since I don't have a direct contact at Etsy's security team (apart from security-reports@etsy.com), here is the question I would like to ask them (which hopefully will reach the right person).
------------------------------------------------------------------------------------------------
Dear Etsy security team,
How can OWASP help?
A personal blog about: transforming Web Application Security into an 'Application Visibility' engine, the OWASP O2 Platform, Application/Data interoperability and a lot more
Wednesday, 31 October 2012
Etsy.com - A case study on how to do security right?
First a quick disclaimer that as far as I can think of, I don't know anybody at Etsy.com or had any conversations with them in the past.
Following from Nick's presentation on Amazing presentation on integrating security into the SDL , my look into Etsy's Code as Craft blog and my experiment with Graphite (see Measure Anything, Measure Everything, AppSensor and Simple Graphite Hosting).
I have to say that I have been more and more impressed with Etsy's pragmatic and focused approach to application security.
For example check these out:
This is 'real-world' stuff and its what happens when there is a good awareness on the importance and need for doing security.
As you can see, here is a team (from management to engineering) that 'gets' application security, and these are the guys that should be driving a number of OWASP's initiatives, since they represent the 'real-world'. Please correct me if I'm wrong, but a google and owasp search (for 'OWASP Etsy') didn't show a lot of joint activity (the best ones where Nick's participation in the AppSec USA and this job post mentioning the OWASP Top 10). It would be great to see Etsy's guys pushing projects like: AppSensor, ESAPI, Zap, Testing+Developer+Code-Review guides, O2, Exams/Certification, etc...
We (OWASP) need to find ways go get these guys more involved and put them on the driving seat.
In fact, for the next OWASP Summit, we have to make sure these guys are there, working collaboratively with the best minds in Application Security :)
Following from Nick's presentation on Amazing presentation on integrating security into the SDL , my look into Etsy's Code as Craft blog and my experiment with Graphite (see Measure Anything, Measure Everything, AppSensor and Simple Graphite Hosting).
I have to say that I have been more and more impressed with Etsy's pragmatic and focused approach to application security.
For example check these out:
- Scaling User Security (where they described their experience in: 'Rolling out Full Site SSL' and 'Two factor authentication'
- Announcing the Etsy Security Bug Bounty Program
- Couple more posts tagged as 'security': http://codeascraft.etsy.com/category/security/
- Etsy has been one of the best companies I've reported holes to. (reddit thread)
- Effective approaches to web application security (haven't read it but looks like another really 'must see' presentation'
This is 'real-world' stuff and its what happens when there is a good awareness on the importance and need for doing security.
As you can see, here is a team (from management to engineering) that 'gets' application security, and these are the guys that should be driving a number of OWASP's initiatives, since they represent the 'real-world'. Please correct me if I'm wrong, but a google and owasp search (for 'OWASP Etsy') didn't show a lot of joint activity (the best ones where Nick's participation in the AppSec USA and this job post mentioning the OWASP Top 10). It would be great to see Etsy's guys pushing projects like: AppSensor, ESAPI, Zap, Testing+Developer+Code-Review guides, O2, Exams/Certification, etc...
We (OWASP) need to find ways go get these guys more involved and put them on the driving seat.
In fact, for the next OWASP Summit, we have to make sure these guys are there, working collaboratively with the best minds in Application Security :)
Labels:
OWASP MIA
CsQuery - C# jQuery Port for .NET 4.0
CsQuery sounds like a very interresting project, specially it's DOM parsing capabilities.
Need to take it for a test drive and see how well it works.
Need to take it for a test drive and see how well it works.
Labels:
To add to O2,
Tools
Measure Anything, Measure Everything, AppSensor and Simple Graphite Hosting
One of Nick's key concepts in his Amazing presentation on integrating security into the SDL presentation is the need to measure and visualize what is happening with an application (and the side-effects of code deployments/fixes).
A key reference is the Measure Anything, Measure Everything and Tracking Every Release posts which talk about how etsy.com uses the Graphite ('Scalable Realtime Graphing') tool with some events consolidation/aggregation via StatsD
What is really interesting about this 'events monitoring capabilities' is that it can be used to monitor Network/Application behaviour/status, and capture/visualize security events (check out the login failures graph in the Measure Anything, Measure Everything post). And if you add this to an OWASP AppSensor aware app, we start to have a very interesting/powerful solution.
So (since we need a solution to monitor what is going on with Teammentor.net) I want to give Graphite a test drive.
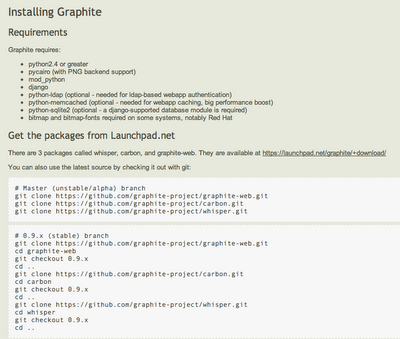
The first problem is that the Graphite Installation page has a couple more dependencies and steps than I would like (I was expecting one download and two steps: download + Run :) )
A key reference is the Measure Anything, Measure Everything and Tracking Every Release posts which talk about how etsy.com uses the Graphite ('Scalable Realtime Graphing') tool with some events consolidation/aggregation via StatsD
What is really interesting about this 'events monitoring capabilities' is that it can be used to monitor Network/Application behaviour/status, and capture/visualize security events (check out the login failures graph in the Measure Anything, Measure Everything post). And if you add this to an OWASP AppSensor aware app, we start to have a very interesting/powerful solution.
So (since we need a solution to monitor what is going on with Teammentor.net) I want to give Graphite a test drive.
The first problem is that the Graphite Installation page has a couple more dependencies and steps than I would like (I was expecting one download and two steps: download + Run :) )
So since I'm not in the mood (or have the time) to do some linux hacking, I googled for a hosted solution and found the Hosted Graphite company who is providing what I need at a price that allows me to experiment them:
Let's see what happens :)
Labels:
Tools
My TeamMentor 'to-do' list for the next 6/12 months :)
I was thinking today about the areas/ideas that I think should/could be developed over the next 6/12 months on TeamMentor and come up with the list below (I stopped after a while since the list was getting quite big :) )
The good news is that with the new TeamMentor 3.2 codebase and architecture, this is all doable, specially when compared with what has already been implemented over the past 18 months (btw, if you are a TM user feel free to put 'pressure' on which ones should happen first :) ).
With the caveat that these (very draft/raw) ideas are not in the right order in terms of priority or effort:
Key Scenarios to support/improve:
- How Developers find/are-exposed-to TM content
- Time that it takes to create an Article
- Time that it takes to push changes to an article (from the first email/reddit comment, to its creation/edition, to its publishing in the official SI library, to the moment it is available in a customer site)
- Improve TM hyperlinks and its connections to/from the best content out there
- Ability for TM to help developers to fix code
- Ability of TM to help policy makers to define, distribute and enforce security policies
- Ability to 'react to current events' and have relevant TM articles about it
- How Security teams create and distribute their findings
- How Security Knowledge and 'Best Practices' are created
- How Security tools show guidance for the security issues their tools are able to find
- How easy it is to create/convert content into the TM_Article schema
TM integration with 3rd party tools:
- Consume TM in:
- Security tools:
- AppScan suite, HP tools, ThreadFix, Armorize, Veracode, Whitehat, Zap, ThreatModeller, Qualys, Metasploit Netsparker (see more tools here)
- 'Policy' tools (and CMS)
- MediaWiki, Sharepoint and what ever tools the CIOs and 'Policy-guys' use
- IDEs:
- VisualStudio (better plugin) Eclipse, MonoDevelop, Notepad, latest online javascript editor, GitHub, etc... (see IDE list here)
- Import/Export
- security-findings conversion into TM Article Schema,
- Allow TM to directly invoke (and control) external tools for example:
- Trigger scans from TeamMentor GUI
- Use the fact that we use TM ourselves to show how/where TM adds value
- On TeamMentor.net give the marketing team maximum visibility into what is going and integrate/export 'TM generated data' with the tools they use (email, SalesForce, HubSpot,etc...)
- Add issues documented in https://github.com/TeamMentor/Master/issues?milestone=3&state=open and the next batch of their requests
Make TeamMentor a case study of a 'Secure app'
- Document TM's security architecture and use it as a case study of 'how things should be done' (working with the AppSec community on what that actually means)
- Continue with the practice of 'please hack teammentor' and the 'TM security bounty'
- Add security features like HSTS and CSP (Content Security Policies)
- Find a way to scan/test TeamMentor using the best security tools out there (Commercial and Open Source)
Consume/Map external data
- NIST, CWE, SANS, OWASP, MSDN, StackExchange, Google
- Better ways to consume/present TM data:
- 'Google like' search engine mode
- Article's mappings schemas,
- Better design
- Link's visualisation,
Change TM Articles from the current 'flat content format' to a 'content + mappings' format:
- Figure out a way to create, package and create TM Articles based on the concept of 'virtual mappings'
- A key scenario to support is the reuse of the same landing pages for multiple technologies (i.e. '1 landing page + n mappings' into 'technologic specific' content/article)
- This 'technologic specific' content, can be another TM Article or an external resource (a page in CWE site) or even just a title/topic ('Section XYZ of PCI ABC standard')
TeamMentor Mobile/Tablet
- Auto detection and display 'TM mobile version' to mobile users
- Create downloadable/installable versions of TM Libraries (which can be sold in Apple's or Android's AppStore)
- Use this version to explore multiple GUI options and to implemente (a much needed REST API for the fetch of Library/Folder/View data)
- Find a way to package 'security reports' in TM Libraries that can be securely consumed on a tablet
- Explore the reuse of the GUIs created for tablets in the developer's IDEs (i.e the same Web Interface used to consume (navigate into) an TM Article would be the same in an (Android) Tablet and in the developer's (VisualStudio) IDE.
- This is a really important concept and one that I think will make a massive difference in TM's adoption and use
Improve TM Design
- First 'clean rough edges' Design pass
- 'What should TM 4.0 look like' design pass
- Focus on making TM 'Simple to use'
- Think about better ways to present the main TM web GUI (which at the moment is quite cluttered)
Technologic changes needed on TM code base:
- Improve Unit Tests support and use them as part of TM continuous build
- New control panel
- Improve User Management and Automation of User provisioning/management
- Improve TM's use of Git's engine
- Auto Commit on code changes
- View Articles changes
- Ability to change between TM versions (i.e. to go back into 'GitHub history')
- Use Asp.Net MVC 4.0 for request routing
- Add activity/request monitoring capabilities (maybe using Graphite) and add support for AppSensor-like capabilities
- Remove legacy APIs and dead code (from TM 2.0)
- Improve TM article cache architecture
- Better HTML online editing capabilities
- Better WikiText/Markup online editing capabilities (starting by adding Markup support)
- Ability to Import data from other sources (word docs, web pages, etc..)
- Allow the secure storage of data (by encrypting an Article's content (not the metadata))
- Add TM installer for IIS and a better launcher (i.e. remove that 'start TeamMentor.bat')
- Add support for OAuth authentication where it would be possible to authenticate using (for example) Google/Gmail, Twitter, Facebook, etc..
- Add online-payments support to TM where the user can buy a TM license or to a TM Library from TM's user's control panel
- Create a read-only version of TM
- Add support for 'providing anonymous feedback on TM usage' (with usage data and bugs/problems sent to SI)
Support for scheduled tasks:
- Auto fetch of Content changes (and if desired, with auto merge with existing content)
- Auto update (latest version of Code)
- Auto rebuild (for sites like TeamMentor.net that need to always been in a pristine state)
- Stats-web-traffic data analysis and email to devs and marketing
- User Management (for example to expire users)
User-centric capabilities
- Ability to track user's usage of TM
- Ability to store user data and activities
- Ability to change GUI based on store user data (namely its activities, behaviour and tasks)
- Ability to define what a user should do in TM
TM deployments monitoring technologues,
- Ability to deploy first 10s then 100s of new TM instances per day
- TM Cloud Provisioning 'Control Panel' - with ability to create/start/stop new TM instances with a couple clicks
Improve 'Content Changes/Comments' workflow
- Improve GUI to track and visualize content changes
- Add support for 'Article' Forks (just like https://gist.github.com/ )
- Allow users to make comments (and link to) to specific parts of an article (this could be done on a per user article fork)
Inter-TM communication where TM instances can
- talk to each other and automatically Download/upload content
- send/receive user data/activities/tasks
Labels:
TeamMentor
Trust should be the currency of software
See Rachel Botsman's Ted talk The currency of the new economy is trust and think about how we could use similar trust models to map out the security properties of applications, APIs or even code snippets
Labels:
Philosophy
Tuesday, 30 October 2012
The next level App Security Social Graph
My core belief is that openness and visibility will eventually create a model/environment where the 'right thing' tends to happen, since it is not sustainable (or acceptable) to do the 'wrong thing' (which without that visibility is usually not exposed and contested). See the first couple minutes on the Git and Demoracy presentation for a real powerful example of this 'popular/viral awareness' in action.
When I look at my country (Portugal and now UK) or my industry (WebAppSec) I see countless examples of scenarios where if information was being disclosed and presented in a consumable way, A LOT of what happens would not be tolerated.
For example, we (in WebAppSec) industry know how bad the software and applications created every day are. And we (and the customers) have accepted that vulnerabilities are just part of creating software, and that the best we can do is to improve the SDL (and reduce risk).
But, if the real scale of the problem was known, would we (as a society or industry) accept it? Would we accept that large parts of our society are built on top of applications that very few people have any idea of how they work? (might as well if they are secure).
So while OWASP is busy booking meetings to have meetings, the rest of the world is moving on, and is trying to find ways to connect data sets in a way that 'reality is understandable/visible', so that what is really going on, is exposed in a easy to consume and actionable way.
For example take a look at the Next Level Doctor Social Graph for an attempt at driving change while trying to figure out a commercially viable way of doing it (check out their '“Open Source Eventually” idea)
From that page, here is is their description of the problem:
"It is very difficult to fairly evaluate the quality of doctors in this country. Our State Medical Boards only go after the most outrageous doctors. The doctor review websites are generally popularity contests. Doctors with a good bedside manner do well. Doctors without strong social skills can do poorly, even if they are good doctors. It is difficult to evaluate doctors fairly. Using this data set, it should be possible to build software that evaluates doctors by viewing referrals as “votes” for each other." (see related reddit thread here)
This is what they call the Next Level Doctor Social Graph , and when I was reading it I was thinking about doing the same for software/apps under the title: The next level App Security Social Graph
Here is the same text with some minor changes (in bold) on what the The next level App Security Social Graph could be:
"It is very difficult to fairly evaluate the quality of software/application's security in this country. Our regulators only go after the most outrageous incidents/data-breaches. The product/services websites are generally popularity contests. Applications with a good marketing do well. Applications without strong presentation skills can do poorly, even if they are secure applications. It is difficult to evaluate security fairly. Using this data set, it should be possible to build software that evaluates application's security by viewing ..... (to be defined)"
It would be great if the current debate was on that ..... (to be defined) bit (ideally with a number of active experiments going on to figure out the best metrics) ... but we quite far away from that world ....
... meanwhile another 8763 vulnerabilities (change this value to a quantity you think is right) have just been created since you started reading this post. These 'freshly baked' vulnerabilities are now in some code repository and will be coming soon to an app that you use (and your best defence is to hope that you are not caught by its side-effects)
When I look at my country (Portugal and now UK) or my industry (WebAppSec) I see countless examples of scenarios where if information was being disclosed and presented in a consumable way, A LOT of what happens would not be tolerated.
For example, we (in WebAppSec) industry know how bad the software and applications created every day are. And we (and the customers) have accepted that vulnerabilities are just part of creating software, and that the best we can do is to improve the SDL (and reduce risk).
But, if the real scale of the problem was known, would we (as a society or industry) accept it? Would we accept that large parts of our society are built on top of applications that very few people have any idea of how they work? (might as well if they are secure).
So while OWASP is busy booking meetings to have meetings, the rest of the world is moving on, and is trying to find ways to connect data sets in a way that 'reality is understandable/visible', so that what is really going on, is exposed in a easy to consume and actionable way.
For example take a look at the Next Level Doctor Social Graph for an attempt at driving change while trying to figure out a commercially viable way of doing it (check out their '“Open Source Eventually” idea)
"It is very difficult to fairly evaluate the quality of doctors in this country. Our State Medical Boards only go after the most outrageous doctors. The doctor review websites are generally popularity contests. Doctors with a good bedside manner do well. Doctors without strong social skills can do poorly, even if they are good doctors. It is difficult to evaluate doctors fairly. Using this data set, it should be possible to build software that evaluates doctors by viewing referrals as “votes” for each other." (see related reddit thread here)
This is what they call the Next Level Doctor Social Graph , and when I was reading it I was thinking about doing the same for software/apps under the title: The next level App Security Social Graph
Here is the same text with some minor changes (in bold) on what the The next level App Security Social Graph could be:
"It is very difficult to fairly evaluate the quality of software/application's security in this country. Our regulators only go after the most outrageous incidents/data-breaches. The product/services websites are generally popularity contests. Applications with a good marketing do well. Applications without strong presentation skills can do poorly, even if they are secure applications. It is difficult to evaluate security fairly. Using this data set, it should be possible to build software that evaluates application's security by viewing ..... (to be defined)"
It would be great if the current debate was on that ..... (to be defined) bit (ideally with a number of active experiments going on to figure out the best metrics) ... but we quite far away from that world ....
... meanwhile another 8763 vulnerabilities (change this value to a quantity you think is right) have just been created since you started reading this post. These 'freshly baked' vulnerabilities are now in some code repository and will be coming soon to an app that you use (and your best defence is to hope that you are not caught by its side-effects)
Labels:
OWASP MIA
Opposite of 'Security as TAX'
In the multiple articles tagged with Security as TAX I tried to show examples where security and 'secure coding' doesn't add (direct) value to an application/developer and is something the devs/companies have to pay in order to publish/release an application.
They are usually cases where the app was working ok in the 'insecure' state and the fixes had some nasty side effects (or where hard to implement).
But as I am planning to write a couple example of where security DOES add value (think: Amazing presentation on integrating security into the SDL), I was wondering what is the opposite of 'Security as TAX':
They are usually cases where the app was working ok in the 'insecure' state and the fixes had some nasty side effects (or where hard to implement).
But as I am planning to write a couple example of where security DOES add value (think: Amazing presentation on integrating security into the SDL), I was wondering what is the opposite of 'Security as TAX':
- Security as Bonus or just Security Bonus
- Security as Added-Value
- Security as a Good Fairy
- Security as Friend
- Security NOT as TAX
- Security as TAX Refund
- OWASP's Security
- Security Zen
- Beautiful Security
- Application Security done in a way that will not drive Developers crazy
- Here something from your best friend: Security
- SecDDev - see SecDDev - Security Driven Development
- Invisible Security or Security Invisible - see "Making Security Invisible by Becoming the Developer's Best Friends" presentation
Humm... none of them works very well...
Let me know if you have any good ideas
Labels:
Security as TAX
Monday, 29 October 2012
Handling code samples on translation of technical content
Here an interesting problem, how to deal with code-samples when doing translations?
We are in the process of translating TeamMentor into a couple languages and the issue come up on how to identify the Code Samples for the translators (which at the moment should all be wrapped using <pre> tags (since that is how the Javascript-based-code-formatting works)).
Here is my first raw idea:
- create a fork (of the target library) for a particular translation
- run a script on all articles that remotes ALL code samples and replaces it with a unique ID (the extracted code snipptets would be stored separately)
- the translators work on the articles (which now have no code samples)
- the translators commit their change into their fork (we can help them if they want)
- we re-apply the code samples
What I like about this idea is:
1) we remove 'areas for translators to make mistakes' (i.e. there are no code samples in their content)
2) we are able to visualize all code samples in one place
3) we can make a pontual decision on the cases where it makes sense to do some translation on the code samples (cases where there is a lot important code comments)
Since the translation house(s) have its own tools (and parsers), the final solution is probably going to be a mix of this idea and what they already do with their technology (no need to solve problems that already have solutions :) )
Any good solutions out there that work well for Html content with code samples?
Labels:
Half-baked Idea,
TeamMentor
Util - O2 Java Tools (IKVM Based) v1.0
For the Java users, here are a couple O2 Tools that expose GUIs to view java class files and programatically analyze them.
These tools leverage the amazing IKVM project to parse the Java class files into C# classes.
You can download the exe from Util - O2 Java Tools - IKVM Based v1.0.exe (its 20Mb since it includes the latest version of IKVM)
These tools leverage the amazing IKVM project to parse the Java class files into C# classes.
You can download the exe from Util - O2 Java Tools - IKVM Based v1.0.exe (its 20Mb since it includes the latest version of IKVM)
Labels:
Java,
O2 Platform Tool
So nice of Microsoft to keep the level low :)
As I am starting to worry about 99.999% website uptime and availability for TeamMentor.net (let me know if you know any good website monitoring services, or tools, or APIs), it is nice to know that if do we achieve that, we will be way above the average :)
For example, here is what happened today (2:13am on 29th/Oct/2012) if you click on 'Schedule service' or 'Check service status' from the new shiny Microsoft Suface website:
Oops , this what we get on https://myservice.surface.com :
Don't they have website monitoring or WAFs over there?
It looks like the problem is in the https part of the surface.com site (the http redirects to a microsoft.com url)
Now here an interesting twist, I was going to recommend that they used ASafaWeb but all looks good from its point of view (note how the main request returns a valid page)
so I though that maybe the problem was with using Chrome, and IE would work, but no such luck, IE shows the same error:
For example, here is what happened today (2:13am on 29th/Oct/2012) if you click on 'Schedule service' or 'Check service status' from the new shiny Microsoft Suface website:
Oops , this what we get on https://myservice.surface.com :
Don't they have website monitoring or WAFs over there?
It looks like the problem is in the https part of the surface.com site (the http redirects to a microsoft.com url)
Now here an interesting twist, I was going to recommend that they used ASafaWeb but all looks good from its point of view (note how the main request returns a valid page)
so I though that maybe the problem was with using Chrome, and IE would work, but no such luck, IE shows the same error:
There is definitely something interesting going on here, I wonder what it is :)
The realisty is that it is really complex to provide online services. Its an environment with very little margin for error, where every small detail counts and semi-real-time feedback/reaction is really important.
The Day Microsoft killed Partial Trust
I missed this when it come out (was in June 2012?) , but I guess that Microsoft ask finally killed ASP.NET partial trust:
I have always been a fan of .NET's partial trust, which was MUCH better designed and implemented than the Java Security Manager, and for a while it showed a path into a much safer .Net development environment.
This is how the ASP.NET Partial Trust does not guarantee application isolation KB article describes it:"...We previously described ASP.NET partial trust as a mechanism for enforcing application isolation in a shared hosting environment in which multiple applications that have different trust levels are hosted on the same web server. We are updating our guidance about this to reflect that running an ASP.NET page framework application in partial trust does not guarantee complete isolation from other applications that are running in the same process or on the same computer..."
I guess I could see this coming, since Partial Trust has been a massive failure with very little adoption and commercial use.
I wonder what prompted this announcement? I would bet that Microsoft found some nasty vulns in the PartialTrust environment which they can't (or won't) fix, so it's better to drop Partial Trust than to wait for a public disclosure.
It's actually quite sad to see such powerful idea and technology being dropped, but at least the good news is that it makes it more clear that running .NET code is a very dangerous activity and that we need better Sandboxing and SAST technologies.
I have always been a fan of .NET's partial trust, which was MUCH better designed and implemented than the Java Security Manager, and for a while it showed a path into a much safer .Net development environment.
Nice Java real world app with real world complexity
Just found the caTissue Suite java application which is part of the Tissue-Biospecimen Banking and Technology Tools Knowledge Center which seems to be a nice complex project (with an open license)
Here is the 400m download file: Download caTissue Suite v1.2 Installation Files
Here is the 400m download file: Download caTissue Suite v1.2 Installation Files
The main wiki is at https://wiki.nci.nih.gov/display/caTissuedoc/caTissue+Documentation+Wiki and this project seams to have run out of initial funding:
What I like about it, is that it looks like a good example of the type of real-world apps that we need our security tools to support.
Sunday, 28 October 2012
Starting to use the O2 Spring MVC viewer on ThreadFix
Using the Tool - O2 Cmd SpringMVC v1.0.exe (see more details on this post: Tool - O2 Cmd SpringMVC v1.0.exe - as standalone exe) here is how to start using it on ThreadFix from Denim Group ("ThreadFix is a software vulnerability aggregation and management system that helps organizations aggregate vulnerability data, generate virtual patches, and interact with software defect tracking systems.")
I downloaded the ThreadFix binaries from the download page : ThreadFix_1_0_1.zip
And since I couldn't find a download for the source code, I used git by executing: $ git clone https://code.google.com/p/threadfix/
I downloaded the ThreadFix binaries from the download page : ThreadFix_1_0_1.zip
And since I couldn't find a download for the source code, I used git by executing: $ git clone https://code.google.com/p/threadfix/
Labels:
Spring Framework
Amazing presentation on integrating security into the SDL
Nick Galbreath (@NGalbreath) has published the great presentation he delivered at OWASP's AppSec USA last week.
You can read it on his Rebooting (secure) (web) software development with Continuous Deployment blog entry or use the embedded slide-share viewer below:
There are lots of great ideas and concepts in there, but for me the slide that really describes what we are trying to do (and how we have to solve the 'software security problem') is this one:
"If we want to fix Security .... we have to fix Development"
"If we want to fix Security .... we have to fix Development"
"If we want to fix Security .... we have to fix Development"
.... (write/say 100x until internalized)
"If we want to fix Security .... we have to fix Development"
One of the reasons why driving security changes and making code-fixes is so hard, is because security doesn't live in isolation and it is 100% depended on the development process that exists on the other side.
What I like about Nick's pragmatic approach is that he is showing (with real examples) that when there is a slick, fast and effective SDL (with daily pushes to production), security is much easier to embed and there is a much better architecture to 'inject security' into the SDL (and to understand the side effects of those security changes)
The good news is that we 'the security dudes' have such a good reputation with developers, and they trust us so much, that we are the best guys to drive this change.............
.... I can just hear the developers calling the security teams and say "....Hey we want to change how we develop our applications/websites, can't you come over and tell us what to do? ... Since you've been trying to 'tell us what to do' forever ... you must have good solutions for how to create the type of Development environment that Nick is talking about'..."
....yeah ..... right :(
Related posts:
You can read it on his Rebooting (secure) (web) software development with Continuous Deployment blog entry or use the embedded slide-share viewer below:
There are lots of great ideas and concepts in there, but for me the slide that really describes what we are trying to do (and how we have to solve the 'software security problem') is this one:
"If we want to fix Security .... we have to fix Development"
"If we want to fix Security .... we have to fix Development"
"If we want to fix Security .... we have to fix Development"
.... (write/say 100x until internalized)
"If we want to fix Security .... we have to fix Development"
One of the reasons why driving security changes and making code-fixes is so hard, is because security doesn't live in isolation and it is 100% depended on the development process that exists on the other side.
What I like about Nick's pragmatic approach is that he is showing (with real examples) that when there is a slick, fast and effective SDL (with daily pushes to production), security is much easier to embed and there is a much better architecture to 'inject security' into the SDL (and to understand the side effects of those security changes)
The good news is that we 'the security dudes' have such a good reputation with developers, and they trust us so much, that we are the best guys to drive this change.............
.... I can just hear the developers calling the security teams and say "....Hey we want to change how we develop our applications/websites, can't you come over and tell us what to do? ... Since you've been trying to 'tell us what to do' forever ... you must have good solutions for how to create the type of Development environment that Nick is talking about'..."
....yeah ..... right :(
Related posts:
- SecDDev - Security Driven Development
- 'About' page broken due to ClickJacking protection
- Couple XSS issues and XSS-By-Design (in TeamMentor)
- Security evolution into Engineering Productivity
- My presentation at OWASP AppSec Brazil: "Making Security Invisible by Becoming the Developer's Best Friends" or "Making Security Invisible by Becoming the Developer's Best Friends" presentation
- What are the challenges with SAST that don't need a better engine
- Why should a developer care about security training?
Labels:
Rant,
Security as TAX
SecDDev - Security Driven Development
I was thinking today about the areas where security (and secure development) can add value to the SDL and hit on the concept of Security-Driven-Development (SecDDev)
SecDDev is security coding activities driven by security focused developers (which is much more productive than the current security as TAX model we have today)
The way I got into this idea was that I was thinking about one of the TeamMentor (TM) refactorings that I would like to see happening, namely the need to create a 'read-only' version of TeamMentor for sites like TeamMentor.net
This would be a version of TM that has no ability to change the Libraries and Article's content, which is a great way to achieve security, since it is harder to exploit a feature when the code is not there :)
What is interesting on this scenario ('Read-Only TM') is that the business requirement ('have a rock-solid version of TM hosted in TeamMentor.net that can be sold to customers') doesn't NEED this isolation! It possible (and easier) to deploy a version that has the full (very powerful) TM editing capabilities and hope that those features are not exploited, or that none of the editors and admin users delete anything (see missing iOS Library incident). This lack of business requirement, means that unless there is an additional driver to create this 'read-only' version, it won't happen (which explains why we end-up with the bloated 'security-vulns-rich' applications we have today).
Now there is a good business case for 'application isolation and robustness' but those tend to be fuzzy concepts which are hard to measure. For example, in this kind of activities, there is a massive lack of external recognisable metrics, where the site looks and behaves the same before and after the refactoring (until it is able to sustain an exploit/mistake or massive traffic spike). In fact these changes tend to introduce massive side effects (see 'About' page broken due to ClickJacking protection)
And this is where the idea of SecDDev occurred to me where I was thinking 'if only I had a security focused development guy/team that would help me in doing this refactoring'.
Since that person (the Security-Driven-Developer) would have has as part of his job spec the "improvement of TM's security" (where that is just one of the (many) roles and responsibilities that I have in TM's SDL) he/she would be much more focused into making it happen.
Creating a read-only version of TM, which in practice means the isolation of the read-code and the edit-code into separate sites/areas which can be easily removed, is a good example of an important-but-not-urgent activity that would make a massive difference in TM's overal security architecture.
To complicate matter worse, it is hard to make this type of code changes. Even after all my efforts to develop TM in a modular architecture, the technologies and frameworks used (Html, Javascript, jquery, .Net) promote/reward tight integration and inter-dependencies (for example it would be 'security by obscurity' to remove the edit-code from the front-end, but leave it all on the webservices back-end).
This is why when you look at most apps, the code is always in 'development activities blocks' instead of 'security focused blocks'
Another area that SecDDev would have to focus a lot is on UnitTests, since they would struggle to make/propose any meaningful change without the support and cushion of a solid Unit/Integration test suite. And anybody that gives me a working UnitTest for TM, is somebody that is adding value to me as a developer! (in fact, SI will even pay for those Unit Test :) )
Another interesting 'political' problem happens when the product managers/owners have a lot of power and want to 'lock-in the customer' into a product's technology. For example, a real secure way to create a 'read-only' version of TeamMentor, would be to remove 99% of its code (on both client and server sides) and built a flat-file version (i.e. pure HTML) protected by a simple OAuth-based authentication/authorisation layer (which could even be done as an external service). But this would mean that the 'TeamMentor' product would 'disappear' and all that would be left would be the Content. The good news (for TeamMentor) is that since SI's center of gravity is on the 'Content + Services side' there are no problems in following what is the best engineering route, but when you look at why some applications/websites are so bloated (and don't like to allow the exporting of its data), you will usually find that it happens due to political/strategic decisions instead of engineering ones)
Finally, where are we going to get those SecDDevs from? Well Mark has a good idea for that, see: Let's make this happen: "Investing in Developing Software Security Talent"
SecDDev is security coding activities driven by security focused developers (which is much more productive than the current security as TAX model we have today)
The way I got into this idea was that I was thinking about one of the TeamMentor (TM) refactorings that I would like to see happening, namely the need to create a 'read-only' version of TeamMentor for sites like TeamMentor.net
This would be a version of TM that has no ability to change the Libraries and Article's content, which is a great way to achieve security, since it is harder to exploit a feature when the code is not there :)
What is interesting on this scenario ('Read-Only TM') is that the business requirement ('have a rock-solid version of TM hosted in TeamMentor.net that can be sold to customers') doesn't NEED this isolation! It possible (and easier) to deploy a version that has the full (very powerful) TM editing capabilities and hope that those features are not exploited, or that none of the editors and admin users delete anything (see missing iOS Library incident). This lack of business requirement, means that unless there is an additional driver to create this 'read-only' version, it won't happen (which explains why we end-up with the bloated 'security-vulns-rich' applications we have today).
Now there is a good business case for 'application isolation and robustness' but those tend to be fuzzy concepts which are hard to measure. For example, in this kind of activities, there is a massive lack of external recognisable metrics, where the site looks and behaves the same before and after the refactoring (until it is able to sustain an exploit/mistake or massive traffic spike). In fact these changes tend to introduce massive side effects (see 'About' page broken due to ClickJacking protection)
And this is where the idea of SecDDev occurred to me where I was thinking 'if only I had a security focused development guy/team that would help me in doing this refactoring'.
Since that person (the Security-Driven-Developer) would have has as part of his job spec the "improvement of TM's security" (where that is just one of the (many) roles and responsibilities that I have in TM's SDL) he/she would be much more focused into making it happen.
Creating a read-only version of TM, which in practice means the isolation of the read-code and the edit-code into separate sites/areas which can be easily removed, is a good example of an important-but-not-urgent activity that would make a massive difference in TM's overal security architecture.
To complicate matter worse, it is hard to make this type of code changes. Even after all my efforts to develop TM in a modular architecture, the technologies and frameworks used (Html, Javascript, jquery, .Net) promote/reward tight integration and inter-dependencies (for example it would be 'security by obscurity' to remove the edit-code from the front-end, but leave it all on the webservices back-end).
This is why when you look at most apps, the code is always in 'development activities blocks' instead of 'security focused blocks'
Another area that SecDDev would have to focus a lot is on UnitTests, since they would struggle to make/propose any meaningful change without the support and cushion of a solid Unit/Integration test suite. And anybody that gives me a working UnitTest for TM, is somebody that is adding value to me as a developer! (in fact, SI will even pay for those Unit Test :) )
Another interesting 'political' problem happens when the product managers/owners have a lot of power and want to 'lock-in the customer' into a product's technology. For example, a real secure way to create a 'read-only' version of TeamMentor, would be to remove 99% of its code (on both client and server sides) and built a flat-file version (i.e. pure HTML) protected by a simple OAuth-based authentication/authorisation layer (which could even be done as an external service). But this would mean that the 'TeamMentor' product would 'disappear' and all that would be left would be the Content. The good news (for TeamMentor) is that since SI's center of gravity is on the 'Content + Services side' there are no problems in following what is the best engineering route, but when you look at why some applications/websites are so bloated (and don't like to allow the exporting of its data), you will usually find that it happens due to political/strategic decisions instead of engineering ones)
Finally, where are we going to get those SecDDevs from? Well Mark has a good idea for that, see: Let's make this happen: "Investing in Developing Software Security Talent"
Solving the missing iOS library in teammentor.net
Here is a document containing 'draft' notes about an issue I had to deal last week, where the iOS Library disappeared from the hosted version of TeamMentor at http://teammentor.net
Labels:
TeamMentor
Creating the final TeamMentor with SI Library repository via multiple Git pulls and pushs
This is going to be a long one, so if you are interested in seeing Git and GitHub in action in a real-world application, grab a coffee/tee/beer and read on :)
This is the scenario at the start:
- We need to create the final TeamMentor 3.2.3 package for release
- The TeamMentor_SI_Library repository is at version 3.2
- The TeamMentor/Master repository is at version 3.2.3
- The Library_SI has a couple content changes since the last pull
- We need to do a pull of both TeamMentor/Master and Library_SI into TeamMentor_SI_Library and push the final result to GitHub
Labels:
Git,
TeamMentor
Saturday, 27 October 2012
Adding Tags to TeamMentor Master repository
With 3.2 out, its time to add some Git Tags to the main TeamMentor/Master repository (which at the moment has none):
Labels:
Git,
TeamMentor
New GitHub structure for the multiple TeamMentor development and deployment scenarios
After a lot of internal debate we finally arrived at the following GitHub architecture (the text below is based on Jason's last email):
Current set-up and logical Divisions:
For that reason we use a repo for the TM code, a repo for internal tools and unit tests, a repo for each tool integration and then a repo for each library.:TM code, TM Docs Library, Tm4tm library, Top Vulns Library and OWASP Library are public, the rest are private.
Customer Purchase:
When a customer purchases TM they need their own source tree to work within and to customize. It should not be visible to anyone else since it'll contain content that is their internal IP. We give each customer a repo that contains the code we delivered to them and then each time we ship a new version we'll push to that repo and merge changes.
GitHub Organization:
Current set-up and logical Divisions:
- TM code and app are free, we can give anyone access
- Tool integrations (like CX or CAT.NET) are free and delivered separately
- OWASP content is free (released under a CC license), we can give anyone access
- Top Vulns library is used by the services team and is free
- For each of the other libraries SI Customers have to pay for and they can be delivered as a combination or one at a time.
- There are internal tools, such as PowerTools and Unit Tests that aren't normally delivered to customers, but can be given for free
For that reason we use a repo for the TM code, a repo for internal tools and unit tests, a repo for each tool integration and then a repo for each library.:TM code, TM Docs Library, Tm4tm library, Top Vulns Library and OWASP Library are public, the rest are private.
Customer Purchase:
When a customer purchases TM they need their own source tree to work within and to customize. It should not be visible to anyone else since it'll contain content that is their internal IP. We give each customer a repo that contains the code we delivered to them and then each time we ship a new version we'll push to that repo and merge changes.
GitHub Organization:
- SecurityInnovation Organisation:
- Contains what's there now minus TeamMentor
- TeamMentor Organization (the 'Code' repos)
- Main TeamMentor codebase, but no content.
- Includes unit tests, power tools, tool integrations
- Example of repositories:
- Master , Unit Tests, Cat.NET, Power Tools
- TMContent Organisation (the 'Content' repos)
- All TeamMentor content libraries (there should be no code in these repos)
- Example of repositories (each a TM Library):
- OWASP (with CC License)
- TM Docs (public)
- Tm4tm Library (public) - Tm4tm = TeamMentor for TeamMentor
- Top Vulns (public)
- SI Library (private)
- .NET 2.0 , .NET 3.5 , .NET 4.0
- Android and iOs
- C++
- Java
- PHP
- CWE and PCI
- etc...
- TMClients Organisation (the 'Content + Data' repositories):
- Repos containing both TM source code and TM Library (in order to make it easier to track deployments and custom changes)
- Repos for each TeamMentor 'client; (which includes SI sites like the teammentor.net fork)
- TM + OWASP Library (the 'eval' version)
- TM + SI Library
- TeamMentor.net version
- demos.teammentor.net
- Customer A
- Customer B
- Customer C , etc..
One of the core ideas/objectives of this structure was to have a clean separation between Code and Data (i.e. TM Source code and TM Libraries). We arrived at a solution based on multiple GitHub Organisations because their website works better that way.
It also helps in the separation of duties/focus since the TeamMentor GitHub organisation is for developers, the TMContent is for content writers/editors and the TMClients is for TM Consumers (and DevOps). Each has its own timings, dynamics and workflow.
Interestingly there is another type of data that we will be soon creating a lot of, which is 'User specific' information. For example if we were to have detailed logs of user's activities, or allowed the user to perform particular actions to an article (see First pass at creating ‘user activities’ (to be removed from 3.0 release) ) where would we store that information?
Labels:
TeamMentor
CheckMarx Queries in TeamMentor with some Landing Pages
Here is a pretty cool PoC (still in draft mode) of the integration of TeamMentor (TM) with Checkmarx content
You can see it at http://checkmarx.teammentor.net/Library/CheckMarx_Queries (which should only open the CheckMarx_Queries library in your browser)
Here the main features/capabilities:
You can see it at http://checkmarx.teammentor.net/Library/CheckMarx_Queries (which should only open the CheckMarx_Queries library in your browser)
Here the main features/capabilities:
- there is a TM Library that holds the CheckMarx's Query's data (created from the data retrieved from this WebMethod)
- there is a TM Folder per language type - also mapped to the TM Article's Technology field
- there is a TM View per query type - also mapped to the TM Article's Phase field
- the Type field indicates if there is a TeamMentor Landing Page for a particular Query
- the Category field contains the CWE Id (good to see the cases when the same CWE is applied to multiple queries)
- The Article html content is made of:
- IFrame with TM Landing Page content (if there is a TM Landing Page)
- IFrame with CWE content (if CWE ID > 0)
- Query rule's Metadata
- Query rule's source (in Checkmarx meta C# language)
Labels:
Checkmarx
Friday, 26 October 2012
Get Html transformations of CWE Html from Checkmarx WebService
Next on the CheckMarx+TeamMentor path, I was curious to see if Checkmarx had rules for all the CWE entries on their database (which are about 865), so now that I have a nice way to get a dump of all their rules I was able to run a quick quick C# LINQ query to calculate the unique CWE ids and then download the current HTML (gist is here):


Labels:
Checkmarx
Util - CheckMarx Rule and Guidance Viewer (with C# SAST Rules and CWE data)
The more I look at Checkmarx the more I like it, for example here is a simple Rules and Guidance viewer that was created by just visualising the 2Mbs of data retrieved from the GetQueryCollection WebMethod
The code is here (Gist) and the standalone exe is at Util - CheckMarx Rule and Guidance Viewer v1.0.exe
The code is here (Gist) and the standalone exe is at Util - CheckMarx Rule and Guidance Viewer v1.0.exe
Labels:
Checkmarx
Tool - O2 Cmd SpringMVC v1.0.exe - as standalone exe
I just had a request for the O2's Spring MVC module (developed ages ago), and It was was a good opportunity to test the latest version of the 'O2 Standalone tool builder', since it now supports the embedding of the tools installed via an O2 Script (usually stored in the _ToolsOrApis folder).
You can download the Tool - O2 Cmd SpringMVC v1.0.exe (or build it using O2) which is the stand alone exe of the old O2_Cmd_SpringMvc.msi tool (See at the end of this post for details on how this exe was created)
You can download the Tool - O2 Cmd SpringMVC v1.0.exe (or build it using O2) which is the stand alone exe of the old O2_Cmd_SpringMvc.msi tool (See at the end of this post for details on how this exe was created)
Windows 8 Sandboxing - some links
I've always been a big fan of Application sandboxing because I really believe that is one of the best way to enforce application security (and to create an ecosystem that rewards secure coding and secure applications). As you can see on Past research on Sandboxing and Code Access Security (CAS) I have done quite a lot of thinking and research about it ... until I gave up because nobody really cared (and FullTrust .Net apps are still the norm).
Now Microsoft seems to be re-inventing the Sanboxing model (again) and giving it another go with Windows 8 RT (RT = RunTime).
I don't know a lot about how it all works, but here are some quick links about it that I found:
Now Microsoft seems to be re-inventing the Sanboxing model (again) and giving it another go with Windows 8 RT (RT = RunTime).
I don't know a lot about how it all works, but here are some quick links about it that I found:
- Application Sandboxing in Windows 8
- MSDN:
- App capability declarations (Windows Store apps)
- Capabilities and Capability
- Sandbox
- Common security scenarios (Windows Store apps)
- Capability based security in Windows 8/Windows Server 2012 (SO)
- Windows 8 is shaping up to be the most secure desktop and mobile OS
- Stronger Windows 8 Still Vulnerable Through Apps, Users
At quick glance I haven't see a lot about policy's or permission's management/visualisation/code-analysis (am I missing it?)
Labels:
Sandboxing,
Windows 8
Interesting preview of Blackberry 10 (now can they execute?)
Just saw this BBC Blackberry 10: Thorsten Heins's plan to revive RIM video interview of Blackberry CEO and it is amazing how I reacted to his new ideas vs how I reacted to Windows 8 Metro (which I still have not used since I can't see the point).
Thorsten seems to be a guy who undertands (in his own words) that 'Quality Matters' and if you get a platform right, you will gain traction.
Take for example his/Blackberry ideas on app multitasking and the hub/messaging central. THAT is big, they are moving from the App centric world (which Apple's App Store took to the next level) and are starting to think about how the user can interact with the Apps capabilities.
The idea that you can reply to something on Twitter (or Reddit, or TeamMentor) without having the application open is HUGE. That will require a whole new level of APIs and standards which will help our apps to work much better (for us)
So good on Blackberry, although I have never coded for it, they definitely seemed to be on the right direction.
See, the Metro stuff (or what ever they will call the tiles duffer in Windows 8) fells and smells like a Microsoft's typical 'lets create something different' activity, where this Blackberry 10 stuff fells like 'here are a bunch of problems that we/you have, and here are some new ideas to address it'. I liked this presentation because it focused on the WHY, not the WHAT
They still need to pull it off, and it will be very interesting to see how open this platform is.
Thorsten seems to be a guy who undertands (in his own words) that 'Quality Matters' and if you get a platform right, you will gain traction.
Take for example his/Blackberry ideas on app multitasking and the hub/messaging central. THAT is big, they are moving from the App centric world (which Apple's App Store took to the next level) and are starting to think about how the user can interact with the Apps capabilities.
The idea that you can reply to something on Twitter (or Reddit, or TeamMentor) without having the application open is HUGE. That will require a whole new level of APIs and standards which will help our apps to work much better (for us)
So good on Blackberry, although I have never coded for it, they definitely seemed to be on the right direction.
See, the Metro stuff (or what ever they will call the tiles duffer in Windows 8) fells and smells like a Microsoft's typical 'lets create something different' activity, where this Blackberry 10 stuff fells like 'here are a bunch of problems that we/you have, and here are some new ideas to address it'. I liked this presentation because it focused on the WHY, not the WHAT
They still need to pull it off, and it will be very interesting to see how open this platform is.
Labels:
Tools
Taking a look at Checkmarx VistaDB database
Following from the VistaDB viewer I developed a while back I just updated it to work on x64.
It was mainly a case of fixing the references to VistaDB.Net20.dll and Checkmarx's CxDB.vdb3 file, like for example:
It was mainly a case of fixing the references to VistaDB.Net20.dll and Checkmarx's CxDB.vdb3 file, like for example:
Labels:
Checkmarx
Thursday, 25 October 2012
Going back in time using Git's checkout
I'm still amazed at Git's speed in moving back and forwards in time. For example I was trying to find a particular GUI that we created for TeamMentor and was able to use git checkout to look at previous versions:
Labels:
Git
Updating Checkmarx license
I just updated the server-side Checkmarx license on SI's test server.
Before the update, it looked like this (note the 10000 LOC limitation):
Before the update, it looked like this (note the 10000 LOC limitation):
Labels:
Checkmarx
Nice list of 20 online coding tools
There is definitely a lot of innovation happening in this space, check out the list at The top 20 online coding tools from .Net magazine.
And if we want to enable the next generation of developers to code securely we need to integrate our knowledge into their IDEs (like these ones). Humm .... I wonder how hard it will be to add TeamMentor integration to these IDEs?
Note that this is on a mainstream developer magazine and (predictably) a search for 'security' or 'owasp' has 0 hits on that page:
And if we want to enable the next generation of developers to code securely we need to integrate our knowledge into their IDEs (like these ones). Humm .... I wonder how hard it will be to add TeamMentor integration to these IDEs?
Note that this is on a mainstream developer magazine and (predictably) a search for 'security' or 'owasp' has 0 hits on that page:
Consuming CheckMarx WebServices
Checkmarx exposes three WebServices (one as ASMX and two as WCF) which are used by their clients tools, for example the VisualStudio Add-in (that can be downloaded from here)
CxWebInterface
Which is the main external interface to their engine and can be accessed at public URL like for example http://checkmarx.teammentor.net/CxWebInterface/ (the Checkmarx server used on their web trials is at https://www.cxprivatecloud.com/CxWebInterface/ )
CxWebInterface
Which is the main external interface to their engine and can be accessed at public URL like for example http://checkmarx.teammentor.net/CxWebInterface/ (the Checkmarx server used on their web trials is at https://www.cxprivatecloud.com/CxWebInterface/ )
Labels:
Checkmarx,
O2 Platform
Making TeamMentor run on UltiDev server
Since Checkmarx runs on UltiDev's web server, it makes sense to also host TeamMentor on it (vs IIS which might not be installed on the target server).
The installation process was quite easy:
The installation process was quite easy:
- downloaded the eval copy of TeamMentor (which is the full engine with the OWASP Library)
- added a website in UltiDev's gui
- configured the site to be an ASP.NET and pointed it to the TM_Website folder
- didn't use any virtual dir, since Checkmarx wasn't using it and TeamMentor likes it that way :)
- that was it
Labels:
Checkmarx,
TeamMentor
'About' page broken due to ClickJacking protection
We're just about to release TeamMentor 3.2 when a final round of QA noticed that the About page was not working:
As you can see by the screenshot and the issue opened (Fix about page which was broken due to ClickJacking protection) this was caused by the fixed applied to the ClickJacking vulnerability reported in TeamMentor.
So here is another nice example the TAX we developers have to pay due to security changes (the app was working great before the fix).
Also, note how the 'security vulnerability' information that I received made no reference to the problems that would be caused by applying the fixes!
Saying 'Enable the X-Frame-Options' is much easier than saying 'Enable the X-Frame-Options and here are the site effects on YOUR app of that change'
And this is the key message that I try to give to security professionals in my "Making Security Invisible by Becoming the Developer's Best Friends" presentations.
Providing information about a security vulnerability and some pointers on how to fix it, is not good enough!!!! Since that is JUST a small part of what is needed to fix that issue.
Usually more important is 'What are the side effects of applying that fix'
For another similar example see the Couple XSS issues and XSS-By-Design (in TeamMentor) post.
Labels:
Security as TAX,
TeamMentor
Security #Fail UX Wifi Connection
So I'm on a local cafe and to access the wifi I have to enter a 13 UpperCase+LowerCase+Number password (given to me from the counter)
This means that it takes me an additional minute and 500% more brain power to login than I would want (and was expecting to). That minute might not sound a lot (and extra use of the brain), but when you are in the zone and with a good mojo, it can be the difference between an idea being implemented and being lost.
This is what the login (and password) looks like (at least they had the common sense to NOT mask the password):
This means that it takes me an additional minute and 500% more brain power to login than I would want (and was expecting to). That minute might not sound a lot (and extra use of the brain), but when you are in the zone and with a good mojo, it can be the difference between an idea being implemented and being lost.
This is what the login (and password) looks like (at least they had the common sense to NOT mask the password):
Labels:
Rant,
Security as TAX
Using Scripted (JS Editor from VMWare) to build Mobile Site
When I was creating the First working version of TeamMentor Mobile I gave scripted a test drive and I quite like it.
You can read more at Scripted: A Javascript Editor from vmware and this is what my GUI looked like:
Since the scripted stuff on the bin folder wasn't working (on Windows), to start scripted, I added the node.exe file to the server directory and launched scripted from there using node scripted.js
I really like the real-time feedback on JS Errors and it is nice to code on an IDE that understands Javascript.
What I really want to learn more is the use of Annotated JavaScript for the Closure Compiler (see https://developers.google.com/closure/compiler/docs/js-for-compiler) since this could be a great way to add type information to Javascript. Note how in the TM_Mobile.js file (screenshot above), it starts with /* global ... */ which tells the compiler to accept those variables as globals
One feature that I would like to see was an auto-preview of the code changes (in a browser window)
You can read more at Scripted: A Javascript Editor from vmware and this is what my GUI looked like:
Since the scripted stuff on the bin folder wasn't working (on Windows), to start scripted, I added the node.exe file to the server directory and launched scripted from there using node scripted.js
I really like the real-time feedback on JS Errors and it is nice to code on an IDE that understands Javascript.
What I really want to learn more is the use of Annotated JavaScript for the Closure Compiler (see https://developers.google.com/closure/compiler/docs/js-for-compiler) since this could be a great way to add type information to Javascript. Note how in the TM_Mobile.js file (screenshot above), it starts with /* global ... */ which tells the compiler to accept those variables as globals
One feature that I would like to see was an auto-preview of the code changes (in a browser window)
Labels:
NodeJS,
TeamMentor
Tuesday, 23 October 2012
First working version of TeamMentor Mobile
After the First working PoC of Tablet/Mobile site using JQueryMobile and Woody template I now got a fully working version of TeamMentor working on a mobile/Tablet design.
Folder(s):
View(s):
Article(s):
Article Content:
I have to say that JQuery Mobile was really nice to use, and I fell I just scratched the surface of what can be done with it.
You can try the latest version at http://tm-mobile-test.apphb.com/ (looks really nice on my IPhone and IPad)
And here it is in action:
Home page:
View(s):
Article(s):
Article Content:
Labels:
TeamMentor
Monday, 22 October 2012
Sometimes the best response is just say 'YES'
One of the most damaging things that can be done to somebody who is playing around with new idea (and have asked for some) support is to not say YES immediately!
Ideas are very fragile, and just like Jonathan Ive said about Jobs "...just as Steve loved ideas, and loved making stuff, he treated the process of creativity with a rare and a wonderful reverence. You see, I think he better than anyone understood that while ideas ultimately can be so powerful, they begin as fragile, barely formed thoughts, so easily missed, so easily compromised, so easily just squished...."
This means that when somebody asks for an opinion or some financial support (like Mark did with Investing in Developing Software Security Talent ), if we believe in the 'core values of the idea', our default answer should be YES!!!
If anything, throw a couple more ideas to the mix and try to evolve the thinking behind the core idea, like I did with Let's make this happen: "Investing in Developing Software Security Talent" (this could backfire since it is important for the person with the idea not to fully realize how complex and hard it will be, but I also believe that one should capture the ideas/thinking that we have (even if an raw state since usually there are some really good nuggets in there))
Now of course that ideas at this stage are still in a very raw state, and in 99.9% of the cases the final model (the one that actually works) will be very different (from an operational/implementation point of view).
Another very important thing is that the person with the idea is going to be in a powerful 'self delusion state' which is actually VERY important. When I look back at my best ideas (i.e. the ones that actually created something), there were always a moment that my faith, focus and value-analysis of that idea was WAY off the chart. BUT if I wasn't for that 'delusion state', the idea would had never happened (for example the O2 Platform or the 2008 and 2011 OWASP Summits). I now know that 'self delusion states' are very important (and even something that can be practiced, improved and managed)
It is at the early stages of the idea (when the 'self delusion state' is on maximum effect) that putting any roadblocks can be very damaging.
And if somebody says "Hey!! I have an idea, would you be able to support it with 1k, 5k or 10k", if the money is kinda available, then the right answer is "YES, sure, in principle count me in". This is the best of the both worlds , since it will give support to the original idea while asking the author to clarify its view and come up with an operational model. Note that no money is going to be spend NOW, this is just a promise of future support.
When I was an OWASP board member, for a while it used to drive me crazy how nobody couldn't do quick decisions for amounts less than 1 USD to 5k USD (they still can't :) ). So at for a while there was an item on the budget that said 'Board Funds' which was an amount that any Board Member could commit at any time for anything. In practice this meant that I was able to provide 'theoretical' financial support to a number of OWASP initiatives (namely chapters, conferences and educational activities). It usually went sometime like "...Hey Dinis, we would like to do XYZ, and at the moment we have a shortfall of $xyz USD, can you give us cover for that amount, in case we don't get $abc USD in sponsors/revenue..". And since a lot of these ideas/activities are Self-fulfiling Prophecies , in most cases the amount needed (if any at all) was much smaller than the one originally asked for.
This is why my default answer to ideas (that make sense to me) and people with energy is YES, Go and Do it!
If they pull-it-off, great!
If they don't, we will be a step closer.
And sometimes we have to do this, even when we know that the idea is wrong and will not work. See, sometimes it is better to just have some movement (even if not 100% on the right direction) then to have no movement at all. This actually means that we also have to be careful when providing (too much) feedback at the early stages, since that might reduce the energy of the other side (an important part of the 'self delusion state' is to be able to ignore the real complexity of the problem at hand, which if fully understood too early, will in most cases be very demoralizing (i.e. it is easy to climb a big mountain in small milestones, without looking too much at how far the top is)
Another myth that also happens is that there is this feeling that 'if supported this will succeed very fast'. Nah, in the real world, the cases where something happens very fast are very small. What I found is that even when there are 'none or very small roadblocks/procedures' (for example with budgets pre-approved), it still takes a lot of effort to make something happen. It also helps to have a culture of proactive-encouragement and an operational machine to support it (the like the OWASP OpsTeam)
Finally, when Ofer Shezar in his The Science in Ideation blog post makes the point that we have to be careful in supporting 'ideas' like the one Mark had, he misses the points that I've tried to make on this post. Because if Ofer also believes that we need more 'developers with security knowledge' (like I do) then he should realize that Mark's idea is a step in that direction.
Now I happen to agree that Mark is not addressing the root cause of the problem, BUT, that is not relevant to this thread :)
And unless we (me and Ofer in this case) are prepared to spend some time on what we think are the 'root causes of the problem' , then we should support the ones that are going on the right direction, like Mark :)
Ideas are very fragile, and just like Jonathan Ive said about Jobs "...just as Steve loved ideas, and loved making stuff, he treated the process of creativity with a rare and a wonderful reverence. You see, I think he better than anyone understood that while ideas ultimately can be so powerful, they begin as fragile, barely formed thoughts, so easily missed, so easily compromised, so easily just squished...."
This means that when somebody asks for an opinion or some financial support (like Mark did with Investing in Developing Software Security Talent ), if we believe in the 'core values of the idea', our default answer should be YES!!!
If anything, throw a couple more ideas to the mix and try to evolve the thinking behind the core idea, like I did with Let's make this happen: "Investing in Developing Software Security Talent" (this could backfire since it is important for the person with the idea not to fully realize how complex and hard it will be, but I also believe that one should capture the ideas/thinking that we have (even if an raw state since usually there are some really good nuggets in there))
Now of course that ideas at this stage are still in a very raw state, and in 99.9% of the cases the final model (the one that actually works) will be very different (from an operational/implementation point of view).
Another very important thing is that the person with the idea is going to be in a powerful 'self delusion state' which is actually VERY important. When I look back at my best ideas (i.e. the ones that actually created something), there were always a moment that my faith, focus and value-analysis of that idea was WAY off the chart. BUT if I wasn't for that 'delusion state', the idea would had never happened (for example the O2 Platform or the 2008 and 2011 OWASP Summits). I now know that 'self delusion states' are very important (and even something that can be practiced, improved and managed)
It is at the early stages of the idea (when the 'self delusion state' is on maximum effect) that putting any roadblocks can be very damaging.
And if somebody says "Hey!! I have an idea, would you be able to support it with 1k, 5k or 10k", if the money is kinda available, then the right answer is "YES, sure, in principle count me in". This is the best of the both worlds , since it will give support to the original idea while asking the author to clarify its view and come up with an operational model. Note that no money is going to be spend NOW, this is just a promise of future support.
When I was an OWASP board member, for a while it used to drive me crazy how nobody couldn't do quick decisions for amounts less than 1 USD to 5k USD (they still can't :) ). So at for a while there was an item on the budget that said 'Board Funds' which was an amount that any Board Member could commit at any time for anything. In practice this meant that I was able to provide 'theoretical' financial support to a number of OWASP initiatives (namely chapters, conferences and educational activities). It usually went sometime like "...Hey Dinis, we would like to do XYZ, and at the moment we have a shortfall of $xyz USD, can you give us cover for that amount, in case we don't get $abc USD in sponsors/revenue..". And since a lot of these ideas/activities are Self-fulfiling Prophecies , in most cases the amount needed (if any at all) was much smaller than the one originally asked for.
This is why my default answer to ideas (that make sense to me) and people with energy is YES, Go and Do it!
If they pull-it-off, great!
If they don't, we will be a step closer.
And sometimes we have to do this, even when we know that the idea is wrong and will not work. See, sometimes it is better to just have some movement (even if not 100% on the right direction) then to have no movement at all. This actually means that we also have to be careful when providing (too much) feedback at the early stages, since that might reduce the energy of the other side (an important part of the 'self delusion state' is to be able to ignore the real complexity of the problem at hand, which if fully understood too early, will in most cases be very demoralizing (i.e. it is easy to climb a big mountain in small milestones, without looking too much at how far the top is)
Another myth that also happens is that there is this feeling that 'if supported this will succeed very fast'. Nah, in the real world, the cases where something happens very fast are very small. What I found is that even when there are 'none or very small roadblocks/procedures' (for example with budgets pre-approved), it still takes a lot of effort to make something happen. It also helps to have a culture of proactive-encouragement and an operational machine to support it (the like the OWASP OpsTeam)
Finally, when Ofer Shezar in his The Science in Ideation blog post makes the point that we have to be careful in supporting 'ideas' like the one Mark had, he misses the points that I've tried to make on this post. Because if Ofer also believes that we need more 'developers with security knowledge' (like I do) then he should realize that Mark's idea is a step in that direction.
Now I happen to agree that Mark is not addressing the root cause of the problem, BUT, that is not relevant to this thread :)
And unless we (me and Ofer in this case) are prepared to spend some time on what we think are the 'root causes of the problem' , then we should support the ones that are going on the right direction, like Mark :)
Labels:
Philosophy
First working PoC of Tablet/Mobile site using JQueryMobile and Woody template
After Buying a mobile site-template from ThemeForest , I'm spending some time using/refactoring the Woody theme for a Tablet/Mobile version of TeamMentor (and learning how jQueryMobile works).
I just reached a key milestone, where I created a PoC that shows the most important technical challenge that I had: The dynamic creation of GUI elements from TM WebServices calls.
In the image below, the important parts are the 2 'Available Libraries' List Items. They are dynamically created via AJAX calls to the TM's GetLibraries WebServices method:
I just reached a key milestone, where I created a PoC that shows the most important technical challenge that I had: The dynamic creation of GUI elements from TM WebServices calls.
In the image below, the important parts are the 2 'Available Libraries' List Items. They are dynamically created via AJAX calls to the TM's GetLibraries WebServices method:
You can try it in action at http://tm-mobile-test.apphb.com (automatic AppHarbor deployment via GitHub), but at the moment the Libraries links open the 'About' page and the other Items (Blog, Portfolio and Contact) still show the original Woody template content.
Labels:
TeamMentor
Pixlr - Great Online Image Editor
Finally I found what It looks like an easy and fast online site to manipulate images.
I was able to upload a psd (photoshop file) to Pixlr.com:
Very cool on Pixlr.com to make it so easy (I'm sure there is a cost of using this service, but for now, I got what I needed, so I can go back to coding)
I was able to upload a psd (photoshop file) to Pixlr.com:
And in less that one minute I had what I wanted: a smaller version of the TM logo in a transparent background:
Very cool on Pixlr.com to make it so easy (I'm sure there is a cost of using this service, but for now, I got what I needed, so I can go back to coding)
Labels:
Tools
Sunday, 21 October 2012
You will not have your best ideas when you are in a position of Power
Here is a simple idea that should explain why I'm blogging so much these days (i.e. I'm trying to find a place to store my ideas (good and bad)).
Statistically it doesn't make sense to think that you will have your best ideas when you are in a position of power.
This could also be said as "You will not have 'Simple Solutions' when you are in Power"
By 'Power' I don't mean that you can just 'order' others what to do, it could be just as well that your opinion and ideas are wanted, and you happen to be so well respected that your ideas will be executed/implemented. I mean 'Power' to have your ideas implemented
By 'Simple Solutions' I mean, solutions that have gone though multiple refactoring of good and bad ideas and 'are just right' (there is nothing more to add or remove)
I actually think that what happens, is that where you are in a position of power, the amount of time available to 'think' and come up with the best/innovative solutions is very small.
It also doesn't help if all ideas are executed since there is a finite amount of energy and resources, and sometimes it is very damaging to spend to much time on a bad (or half-baked idea).
Statistically it doesn't make sense to think that you will have your best ideas when you are in a position of power.
This could also be said as "You will not have 'Simple Solutions' when you are in Power"
By 'Power' I don't mean that you can just 'order' others what to do, it could be just as well that your opinion and ideas are wanted, and you happen to be so well respected that your ideas will be executed/implemented. I mean 'Power' to have your ideas implemented
By 'Simple Solutions' I mean, solutions that have gone though multiple refactoring of good and bad ideas and 'are just right' (there is nothing more to add or remove)
I actually think that what happens, is that where you are in a position of power, the amount of time available to 'think' and come up with the best/innovative solutions is very small.
It also doesn't help if all ideas are executed since there is a finite amount of energy and resources, and sometimes it is very damaging to spend to much time on a bad (or half-baked idea).
Labels:
Philosophy
Handling content changes made on hosted site created by Git clone (with auto Git commits and pushes?)
Here is the next interesting TeamMentor (TM) and GitHub problem to solve:
"How to deal with content changes made using TM's online editing capabilities"
Labels:
Git,
TeamMentor
Let's make this happen: "Investing in Developing Software Security Talent"
Mark posted yesterday an 'draft' idea which I think is GREAT!
Please read it at Investing in Developing Software Security Talent
Although I think that Mark is on a great path, one that is consistent with his views of bringing developers to security (not security to developers), I have a couple comments on is proposed model :)
Here are my key proposed changes:
This is how I would slice it:
Master version (the 'code'): "Developing Software Security Talent" Programme:" - Improving the Software Security Talent of a new Generation of Software developers and 'code fixers'.
The focus of this program is to help Developers or Security Professionals who want to write secure code or fix security vulnerabilities. The model proposed is one based on Internships and Mentorships.
Fork #1 (the 'data) "Seconauts participation in "Developing Software Security Talent" Programme:
Seconauts will:
Fork #2: XYZ Company ....
Fork #3: XYZ University ....
Fork #4: UK Government ....
Fork #5: OWASP ....
etc...
Remember that the objective is to develop Security Talent, so it doesn't really matter how it is done, as long as it happens.
It is also important to take into account that some companies or organisations have a 'Not invented here' syndrome, and it is important to present them with ideas that they can consume, re-brand and execute
Rough/Draf notes
Since Mark's original post was in a 'Draf' mode', here are a bunch of semi-related notes and ideas that I had when reading and thinking about this.
Starting with some comments on the proposed model, I'm going to use SI (Security Innovation) as an example of a company that could participate on the mentoring and hiring activities (note that I have not spoken with the SI guys about this, it is just easier to have a specific example in mind):
Bottom line: Good luck Mark
More Secure Coding talent is something we desperately need, so I hope that this idea really comes into life and I'm happy to help as much as I can.
Why I have experience in making this comments
(originally I had this at the beginning of the post, but I figured out, that this will only be relevant to the readers that are reading it all the way to the end):
-----------------------------------------------------------------------------
I'm going to comment on this as somebody who as already implemented a similar program at OWASP namely the OWASPs Seasons of code who had a similar number of moving parts and activities:
I was also very involved with Paulo Coimbra and the GPC on the management of OWASP projects, where we did a lot of thinking about this:
Please read it at Investing in Developing Software Security Talent
Although I think that Mark is on a great path, one that is consistent with his views of bringing developers to security (not security to developers), I have a couple comments on is proposed model :)
Here are my key proposed changes:
- Separate the 'creating security talent' from Seconauts (ie 'separate code from data', or using a git analogy 'fork the main repository')
- Expand the concept to include current Developers and Security Professionals
- Create a financial model that is easy to implement, transparent and morally effective
This is how I would slice it:
Master version (the 'code'): "Developing Software Security Talent" Programme:" - Improving the Software Security Talent of a new Generation of Software developers and 'code fixers'.
The focus of this program is to help Developers or Security Professionals who want to write secure code or fix security vulnerabilities. The model proposed is one based on Internships and Mentorships.
- The key objective is to create the next generation of developers who will:
- know how to write secure code,
- work with the multiple SDL parties in the multiple secure coding/architecture activities and
- fix security vulnerabilities
- The program will measure its success by the number of 'conversions' made over a period of time:
- # of students that are now focus on secure coding
- # of real-world developers who have added 'secure coding' to their skill set
- # of developers (and job applications) that have 'secure coding' on its job spec
- # of Application Security professionals who have acquired 'secure coding' skills and can talk with developers (in the developer's language) and are able (when requested) to sit down and fix code
- A desired site-effect is the creation of an open community and 'high-quality body of work', that supports the millions of developers who need to write secure code worldwide, and ask 'secure coding questions' everyday.
- How these 'conversions' are made, is not an important detail:
- The 'Seconauts model' (descibed below) is just one way to achieve this goal
Fork #1 (the 'data) "Seconauts participation in "Developing Software Security Talent" Programme:
Seconauts will:
- Find the sponsors and mentors
- Handle the logistics (from payments, to selections, to contacts, to introductions, to public reporting, etc..)
- Define the selection criteria, select the candidates and allocated them to the mentors
- Define the Seconauts projects that will be worked on (by the candidates) and ensure that there is enough high-quality reviewers at hand to help with task allocation and questions raised (by the candidates)
- Help and brief the Mentors (with clear definitions of what are the expectations and responsibilities of each party)
- ...see mark's post for a specific details (like the number of mentors, what each one should do, etc...)
Fork #2: XYZ Company ....
Fork #3: XYZ University ....
Fork #4: UK Government ....
Fork #5: OWASP ....
etc...
Remember that the objective is to develop Security Talent, so it doesn't really matter how it is done, as long as it happens.
It is also important to take into account that some companies or organisations have a 'Not invented here' syndrome, and it is important to present them with ideas that they can consume, re-brand and execute
Rough/Draf notes
Since Mark's original post was in a 'Draf' mode', here are a bunch of semi-related notes and ideas that I had when reading and thinking about this.
Starting with some comments on the proposed model, I'm going to use SI (Security Innovation) as an example of a company that could participate on the mentoring and hiring activities (note that I have not spoken with the SI guys about this, it is just easier to have a specific example in mind):
- I think that the amount paid to the 'candidate' should 'be defined' by the 'contracting party', in this case SI. Since SI would want to get the best talent, it can chose to pay more (this will also depend on the geographical location of the candidate)
- Although I'm a big believer of openness, in this case, the 'financial arrangement' should be a private matter between SI and the candiate
- I like the ideas to give the candidate some money, but this should ONLY be used to cover expenses (computer equipment, travel, hosting services, software, etc). In a similar way that I wrote on Why OWASP can't pay OWASP Leaders the moment the sponsorship money is used as 'payment to the candidate' the social contract between the organisation, the mentors and its participants is broken:
- See previous point on how I'm NOT saying that the candidate should NOT be paid
- I'm saying that the candidate SHOULD be paid, just not by this program (whose funds should only be used for 'expenses')
- With this in mind, the candidate should be given $4000, where HE/SHE decides where to spend that money (and in time there would be a good number of documented examples of where others spent it)
- Like I wrote in the problem of paying OWASP leaders and in the OWASP GSD Project (GSD = Get Stuff Done) proposal, the concept is one where the candidate cannot NOT pay himself, or any company/individual he/she is associated with (this is a great self-regulated system, and it would dramatically reduce the management, monitoring and 'expense approval' requirements / overhead)
- This can be easily executed on a worldwide basis as long as the pieces are in place
- I don't think that the 'need for the candidate to go everyday' to an office is a critical one.
- It raises the bar and complexity of the arrangement
- It goes against the model of the 'distributed' development environment that we have today in the 'GitHub' generation
- Development is sometimes better done in isolation than in groups
- Again, not saying that it shouldn't happen, just that it shouldn't be a big criteria
- For example I have no idea of where some of my good colleagues at SI are (even when I talk to them by voice, email, github, code everyday). They could be somewhere in Europe , in the Boston or Seattle offices or in the middle of the US)
- So I would change this requirement to be 'the candidate must have a physical connection with the mentors every week, which could range from hours to 5 days'
- If the cost allocated to each candidate is $4000, then the sponsorship packages should be multiples of that:
- $4k pays for 1
- $8k pays for 2
- $12k pays for 3
- $20k pays for 5 .... etc...
- This could be set-up on a recurring basis so that the sponsoring companies could view it as a recurring subscriptions.
- I think that there should be NO requirement on either party regarding the next contracts (i.e. namely no obligation for the candidate to work 18 months for the mentoring company).
- For example I would expect that if a candidate did a successful internship at SI, and he liked SI that he wanted to join the company, and SI liked his/her work so much that it would offer a job:
- there would be no need for a 'mandatory 18 months contract'
- the contract offerend by SI should be competitive and fair ,
- such '18 months requirement to work for SI' would dramatically change the negotiation dynamics (putting a lot of power in the hands of SI) and would most likely leave a bitter taste in everybody involved
- The focus should be on writing secure code and fixing existing code at Open Source projects, BUT we shouldn't have very high hopes that the code created will be of a very high standard since by definition these are inexperience 'secure development' developers (which will take more than 6 months to change)
And here is a brain dump of 'stuff' that needs some more thinking:
- it is going to be hard to find a significant number of mentors (which is a catch 22 ,since once the model is proven, they will be easier to find)
- I would say that this is the hard part. At OWASP's Projects (see links below) we had a simpler workflow (which was project leader working with 2 reviewers) and it was REALLY hard to get good reviews created (it does take a lot of time to review something properly). I don't think it should be underestimated how much effort it will take from the mentors and helpers
- There is usually a great difference between the amount of people who will put their hand up and say 'I can do it, I can review that or mentor him/her' to the ones who will actually be able to do it (and sometimes it is not that the reviewer/mentor are not good enough, it is just that it takes a lot of time and effort to do it properly)
- Creating a selection criteria and executing it will be hard, and the best way is to do it 100% in the open (learn from the OWASP seasons of code experience (see links below))
- Expand the target audience (it should also be focused on current professional developers that want to get into application security). We need this NOW for developers that are coding today:
- In fact most companies that write a lot of software need this TODAY for a number of their current dev teams
- I don't like the word 'intern' is sounds like it is for a somebody leaving school (or university). This is why I used the word 'candidate' on this post.
- ex-students should be only one of the target audiences
- The work created by the 'candidates' is most likely NOT going to be production quality (since by default they will be amateurs at it). Only experienced developers (with security awareness/knowledge) are able to create that. So let's not raise the expectations bar too high
- Mark's maths are wrong:
- $4000 will be barely enough to buy: a decent laptop, airfare expenses, hotels, hosting, software,etc... (over a period of 6 months). It will help if outside the US/UK, but we are talking about 800 USD per month (which is less than you get flipping burgers)
- It also doesn't take into account all the back-office admin costs that it will take to make this happen (which I agree that shouldn't be paid from the $4000 sponsorship money)
- I like this idea as a good way to get talent to work on Seconauts (but i can see some critics saying that this is just a cheap way to kickstart a community)
- This is very similar to what happens on a number of companies, and it is called 'Interns' :)
- in fact a number of OWASP members have such programs at their companies (which could be leveraged to kickstart this idea)
- This will not work without operational support/staff, in fact the first thing to do should be to hire / appoint a project manager to run this (Mark is currently doing that role, but he will soon run out of time/energy)
- There is already lot of mentoring happening at OWASP and I am personally involved in a couple of mentoring cases (not within an explicit framework, but achieving the same goals). So some of those efforts could be recycled to kickstart this idea
- There are already a good number of targets for mentorship at OWASP, namely some newer OWASP leaders who are still getting their heads around WebAppSec
- The irony is that OWASP would be the perfect place to do this, since it has the infrastructure, the funds, the community, the brand, etc...
- That said, I think the concept is great, and since Mark is focused on it (and nobody is at OWASP), I will ask the Owasp community to support it and commit to at least 10k. I also will raise this idea at SI and see if they would like to participate
Bottom line: Good luck Mark
More Secure Coding talent is something we desperately need, so I hope that this idea really comes into life and I'm happy to help as much as I can.
Why I have experience in making this comments
(originally I had this at the beginning of the post, but I figured out, that this will only be relevant to the readers that are reading it all the way to the end):
-----------------------------------------------------------------------------
I'm going to comment on this as somebody who as already implemented a similar program at OWASP namely the OWASPs Seasons of code who had a similar number of moving parts and activities:
- Autumn of Code 06,
- Spring of Code 07,
- Summer of Code 08 (whose results were presented at first OWASP Summit 2008)
I was also very involved with Paulo Coimbra and the GPC on the management of OWASP projects, where we did a lot of thinking about this:
- https://www.owasp.org/index.php/Assessment_Criteria_v1.0 (more mature model)
- https://www.owasp.org/index.php/Assessment_Criteria_v2.0 (note how at the end of this page there is a reference to Project Mentors (there was more on mentoring concept, but I couldn't easily find that page/info))
- https://www.owasp.org/index.php/Tool_Assessment_Criteria
- https://www.owasp.org/index.php/Documents_Assessment_Criteria
- https://www.owasp.org/index.php/Research_and_Activities_Criteria
- https://www.owasp.org/index.php/Assessing_Project_Health
- https://www.owasp.org/index.php/Assessing_Project_Releases
For reference, before Paulo Coimbra left OWASP, we were really close to implementing a similar program at OWASP (the idea was to start with getting reviewers involved into projects (in a 'Season of Quality') and then evolve it into mentorships).
And has Paulo's departure showed, without such back-office support it is impossible to do this.
Btw, to give you an idea of the amazing work Paulo was doing on OWASP projects, take a look at https://www.owasp.org/index.php/OWASP_Projects_Dashboard_2.0 (you will be amazed). The good news is that we now have Samantha (Owasp new project manager) who is going to bring things back on track
Labels:
OWASP MIA
Subscribe to:
Posts (Atom)