I just created a page on the OWASP WIKI for mapping the vulnerabilities,exploits and fixes of the IBM's AltoroMutual application:
http://www.owasp.org/index.php/AltoroMutual
If you have some cycles, please help in completing this page
A personal blog about: transforming Web Application Security into an 'Application Visibility' engine, the OWASP O2 Platform, Application/Data interoperability and a lot more
Thursday, 25 November 2010
O2 Platform Videos (Nov 2010)
If you new to the OWASP O2 Platform (or are still trying to get your head around it), here are a number of YouTube videos based on: a) known vulnerable applications (i.e HacmeBank, WebGoat), b) public websites (GMail, Twitter) and c) O2 scripts that I have written:
- http://www.youtube.com/watch?
v=T2XVufhJLig - Example of Unit Test Execution GUI that can be created using O2. In this example a number of HacmeBank vulnerabilities are shown using browser-automation (some of these vulnerabilities/exploits contain complex workflows, like for example: the 'login into admin section' exploit, which uses a ViewState vulnerability to access the dynamic password required to login as the administrator) - http://www.youtube.com/watch?
v=MdObVD53Iyg - Full PoC of Sql Injection for developers. Includes an real-time browser automation/animation of the multi-step vulnerability exploit (on the left), followed by an animation (on the right) of the vulnerability taint-flow path (on the source-code). It probably is hard to see on the video, but the trace created using O2 (Open Source modules/scripts) contains the following structure: - the trace starts with the 'URL + injection parameter' (which is what a BlackBox scanner will produce)
- maps the URL to the entry point on the source-code (at the Web Layer)
- follows the tainted-data (i.e. the variables with payload) all the way until the call to the Web Services
- maps the 'Web-Layer Web Services call' with the 'method that is invoked on the Web Services Layer' (i.e. connects the Web Services caller with the callee)
- follows the tainted-data all the way to the vulnerable Sql Execution (passing by the string concatenation that creates the SQL Injection vulnerability)
- http://www.youtube.com/watch?
v=1bbKNvyvLO0 - A similar example of the Unit test GUI that can be delivered to developers, this time using OWASP WebGoat as the target application - http://www.youtube.com/watch?
v=DpDiGpzaVw0 - Unit Test created in O2 that tests for a vulnerability in Twitter (the result is green because the vulnerability is currently patched) - http://www.youtube.com/watch?
v=rTD31e7HY4E - example of a complex browser-automation workflow: Create GMAIL account - http://www.youtube.com/watch?
v=Gu8Hg02Zv5c - example of a complex browser-automation workflow: Create Twitter account (different execution GUI from the GMAIL account creation script) - http://www.youtube.com/watch?
v=YsVX5-nGHWI - example of another type of dynamic GUIs that can be created using O2 (most of O2 GUIs are O2 Scripts dynamically compiled and executed). In this case this GUI allows the easy creation of XSS demos/PoCs - http://www.youtube.com/watch?
v=j0d3F3wqfRU - using O2 .NET Static Analysis engine to perform source code code reviews and to find vulnerabilities in .Net's Hacmebank - To see all O2 related videos, see http://www.youtube.com/
user/diniscruz#g/u (most of these videos where created using O2's Video creation tool/script)
Poll: "What do you think the future of software security deliverables will be?"
Matt Parsons who is a long time O2 user (and has even started a new blog that is mainly talking about O2) has published a poll (very inspired by this O2 Platform presentation) where he asks the following question:
Please take a minute and cast your vote here: http://polldaddy.com/poll/4143135/
Thanks
Thanks
OWASP CALL FOR TRAINERS!
Sandra (OWASP resource hired to create a training model for OWASP materials), just sent this email to the owasp-leaders that highlights the great work she is currently doing:
------------------------------------------------------------------------------------------
Dear OWASP Leaders,
In the context of the effort we are making to stabilize and consolidate an OWASP Training model that can be used as a powerful tool to spread OWASP’s knowledge and message, OWASP is looking for trainers to deliver training under the flag “OWASP projects and resources you can use today”. This is a model of training which is free for OWASP members, delivered by OWASP Leaders (with only travel expenses paid) and covering OWASP modules and/or projects.
If you are an OWASP Leader and would like to be included in OWASP's pool of trainers, this is your chance - add your name and info to the OWASP Trainers Database and be counted!
Do it now and become an OWASP Trainer! Check the Database and conditions here:
Follow all the developments on the OWASP Training here http://www.owasp.org/index.
We are looking forward to seeing your names online!
Best regards,
Sandra
Sandra Paiva
O2 Platform presentation
Hi, here are the slides from the O2 Platform presentation I delivered at the OWASP Brazil AppSec: OWASP O2 Platform - November 2010
I really like the first part of it (until the 'Real-world O2 usage' in slide 69), since I think I finally documented my key positioning for O2 (Note: the reason why there are a lot of pages is because the "Keynote to PDF" export created one PDF page per slide transition)
In Brazil I didn't made it to till the end, since I did a bunch of O2 demos and run out of time :)
I also did a full day of O2 Training which went very well (the students were new to O2, and by the end of the day they were all trying to figure out where to use O2 in their day-to-day jobs)
Starting an OWASP Chapter
Last week, while I was at the OWASP AppSec Brazil, it was decided to break the existing OWASP Brazil chapter into 5 new chapters (each focused on a Brazilian city).
This is something that should happen more often, since we have a very low 'barrier of entry' for the creation of OWASP Chapters (usually all we need is one local person that is motivated to do it).
So here is what you can do if you don't have a local active chapter in your area and want to create one (in the case of an inactive local chapter, then you should be joining the leadership of the existing chapter (note that each chapter should have at least 3 leaders, until there is a need to have elections)):
That's it.
This is something that should happen more often, since we have a very low 'barrier of entry' for the creation of OWASP Chapters (usually all we need is one local person that is motivated to do it).
So here is what you can do if you don't have a local active chapter in your area and want to create one (in the case of an inactive local chapter, then you should be joining the leadership of the existing chapter (note that each chapter should have at least 3 leaders, until there is a need to have elections)):
- Start by reading the info here: http://www.owasp.org/index.php/Category:OWASP_Chapter , specially the Chapter Leader Handbook: http://www.owasp.org/index.php/Chapter_Leader_Handbook
- Get an Wiki account on www.owasp.org
- If you want, once you have that Wiki account you can create create the Wiki page for your chapter (if you don't, Kate will create this for you)
- Email Kate with your request
- Start planning your first meeting and creating a target list for the people you want to invite once you have your mailing list in place
- Eventually Kate will create your Chapter mailing list, create/update the WIKI page, and add the new chapter to the list of OWASP Chapters (note that this might take a couple of days, depending on how busy Kate it)
- Once you have your new chapter mailing list, you will be automatically subscribed to the owasp-leaders list and it is usually a good idea to write a little intro about you and what are your plans/ideas for your chapter
That's it.
Friday, 12 November 2010
Amazing coverage of OWASP Projects
I just wrote the following email and it struck me the variety of OWASP projects and the potential that they have:
--------------
--------------
On OWASP here are a couple things you might find interresting:
- AppSec DC conference that just finished yesterday in DC
- List of the 16 OWASP Conferences in 2010 (with links to its websites/webpages)
- A review of the EU Conference
- Full List of OWASP Projects , and here are a couple that you should also check out:
- OWASP Legal Project
- Software Assurance Maturity Model
- OWASP Application Security Verification Standard Project
- OWASP Enterprise Security API (ESAPI) Project
- Security Ecosystem Project
- OWASP Security Spending Benchmarks
- OWASP Cloud ‐ 10 Project
- OWASP Positive Security Project
- OWASP Secure Web Application Framework Manifesto
- OWASP Web Application Scanner Specification Project
- OWASP Application Security Metrics Project
- OWASP PCI Project (still early days)
Finally if you want to see a great presentation and positioning, please take the time to see this video from David Rice (Geekonomics Author doing a Keynote presentation at OWASP AppSec USA) . Here are another 26 videos from this conference
Thursday, 4 November 2010
OWASP and certifications
(based on my answer to an email thread about OWASP Certifications started by SI)
Certification has historically been a hot topic at OWASP, with the reasons being a mix of 'alergy' to certifications by a considerable part of our community and the problems in creation an OWASP Certification that is compatible with OWASP Openness model.
James McGovern (a couple years ago) did a an amazing job at trying to create a Certification for OWASP, unfortunately it was probably too soon for the OWASP community and we (at the time) didn't have a good picture of how it could be made to work (and part of that is my fault since I was part of the group that had a problem with the 'need to have closed questions and answers' requirement).
Here are a couple comments, which will hopefully clarify the current situation:
Certification has historically been a hot topic at OWASP, with the reasons being a mix of 'alergy' to certifications by a considerable part of our community and the problems in creation an OWASP Certification that is compatible with OWASP Openness model.
James McGovern (a couple years ago) did a an amazing job at trying to create a Certification for OWASP, unfortunately it was probably too soon for the OWASP community and we (at the time) didn't have a good picture of how it could be made to work (and part of that is my fault since I was part of the group that had a problem with the 'need to have closed questions and answers' requirement).
Here are a couple comments, which will hopefully clarify the current situation:
- There is no problem in creating Certifications around OWASP materials (i.e. not 'OWASP Certifications' but 'Certifications on OWASP {put project name here}' (we could even have an generic 'Certification on OWASP'))
- The problem is in OWASP running this certification (which mainly for the need to have 'closed' questions is a non-starter)
- The only way I could see an 'OWASP Certification' to be created is one were ALL Questions and Answers are publicly available in the OWASP Website (and if you think about this idea for a bit, you'll see that it should work once the number of questions is significant larger than the questions asked the in exam)
- Even in the case where there is an 'OWASP Certification' or 'Certification around OWASP materials', there is no structure at OWASP that can handle the exam and certification process (and there is no plans to create on in the short to medium term)
- The best (and most realistic) scenario is one where 3rd party commercial companies (like SI) use OWASP as the 'body of knowledge' and manage themselves the Question generation, Certification brand and Exam process (of course that OWASP Leaders could be independently involved in this process (for example helping writing questions) but it is very important to understand that there is no structure at OWASP that could be officially involved in this process (for example if SI wants to hire an OWASP Leader to participate that will need to be a commercial arrangement between SI and that OWASP Leader)
- In terms of the focus of the Certifications, I would add another audience that Robert Hansen as tried to push OWASP to do, which is the QA professionals. I.e. create a 'OWASP for QA' Certification that focus on the minimum WebAppSec knowledge that these key SDL players should have.
- Ultimately there should be a number of 'OWASP based' Certifications in the market, and it should be the market to decide which one they trust.
- Although It would be hard for OWASP to 'officially' endorse a certification, we now have (in 2010) a number of ways that OWASP can give a lot of visibility to Certifications that are created around OWASP materials
- Public reviews of certifications delivered at OWASP Conferences (created by an OWASP Leaders who go through the proccess)
- Create an 'OWASP Quote' where OWASP Board+Leaders can make an 'on the record' comment on an OWASP-based certification. See http://www.owasp.org/index.php/Quotes for an example
- List Certification(s) on a 'Commercial Services' registry that is still under development but is a perfect medium for this (see http://www.owasp.org/index.php/OWASP_Related_Commercial_Services)
Friday, 22 October 2010
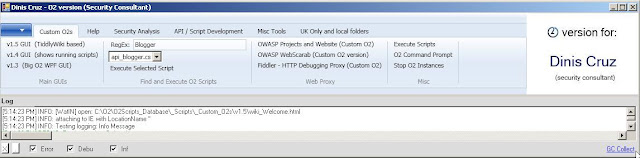
New (Temp) O2 GUI based on my own version of O2
If you open O2 today and do the requested update (which should happen either on the first run or 2nd (depending if you are executing a script directly of if you are clicking on the "OWASP O2 Platform (ClickOnce version)" desktop/start-menu link)) , you should see this new GUI:
The reason I'm pushing this to be the main O2 GUI for now, is because I think it is a a better representation of O2 than the current v1.4 GUI (and I use this GUI every day, so it's starting to be quite solid :) ).
The v1.5 of O2 is still under development and will be based on TiddlyWiki which is an awesome 1-page Wiki engine. You can see it in action if you click on the 'v1.5 GUI (TiddlyWiki based)' button of the 'Custom O2s' Tab, and it currently looks like this:
The reason I'm pushing this to be the main O2 GUI for now, is because I think it is a a better representation of O2 than the current v1.4 GUI (and I use this GUI every day, so it's starting to be quite solid :) ).
The v1.5 of O2 is still under development and will be based on TiddlyWiki which is an awesome 1-page Wiki engine. You can see it in action if you click on the 'v1.5 GUI (TiddlyWiki based)' button of the 'Custom O2s' Tab, and it currently looks like this:
Having an O2 Epiphany - your turn next :)
After sending this reply to one of O2 users
[Dinis Cruz]
"...
Thanks man, I really appreciate your words :)
You are spot on that O2 is all about the automation (of pentesters, code reviews, etc...).
In fact, that is what I'm trying to say with O2's tag line:
"O2 is designed to Automate Security Consultants Knowledge and Workflows and to Allow non-security experts to access and consume Security Knowledge." (from http://o2platform.com/wiki/
"O2 is designed to Automate Security Consultants Knowledge and Workflows and to Allow non-security experts to access and consume Security Knowledge." (from http://o2platform.com/wiki/
Another way to say it is 'Web Security UnitTests' or 'No more PDFs!!!" , but has you can see I still have not figured out the best way to communicate and present O2 :(
..."
[/Dinis Cruz]
Wednesday, 20 October 2010
(Can you help?) Updated CV and looking for 3-day-a-week Job
After 10 months of self funding O2 development, and although I have have solved the major technological and business-model problems with O2, the reality is that I still not able to generate enough revenue from the O2 Subscriptions, Pledges or Training services to financially support me (and the development resources I need to hire for O2).
This means that I will have to go to Plan B, which is to (ideally) get a '3 day a week' / '12 days a month' contract/job. This should give me enough cash-flow to spend the rest of the time on O2 (and servicing its subscription's clients).
I've just updated my CV at LinkedIn (http://uk.linkedin.com/in/diniscruz) and there is also an PDF version available here)
So if you are interested in hiring my services or know somebody who is, please get in touch at (dinis @ ddplus.net).
Thanks for the help
Dinis
This means that I will have to go to Plan B, which is to (ideally) get a '3 day a week' / '12 days a month' contract/job. This should give me enough cash-flow to spend the rest of the time on O2 (and servicing its subscription's clients).
I've just updated my CV at LinkedIn (http://uk.linkedin.com/in/diniscruz) and there is also an PDF version available here)
So if you are interested in hiring my services or know somebody who is, please get in touch at (dinis @ ddplus.net).
Thanks for the help
Dinis
Tuesday, 19 October 2010
Quickly edit the OWASP WIKI (using O2)
One of my pet issues with the OWASP Wiki has always been its interface, more specifically how slow the workflow was when making updates and performing actions like (for example) image uploads.
Labels:
MediaWiki
Drupal security and "why security sucks from a user's point of view"
While trying to create a simple website for new O2 users I tested a couple packages and using the great EC2 solution from http://www.turnkeylinux.org I settle on Drupal for try-o2.com.
This is what it looked like:
 I was happy with the design and funcionality of this site and Drupal, BUT the problem happened when I recently logged in into the admin section of the website and saw this:
I was happy with the design and funcionality of this site and Drupal, BUT the problem happened when I recently logged in into the admin section of the website and saw this:
Since is bound to happen in the future, and Drupal's update mechanisms is equal to 'brain surgery' (remember that I didn't install it, so I would have a bit a learning curve to do it properly), I'm left with no choice but to KILL the website (i.e. the Amazon EC2 image that powers it) and move to WordPress.com since at least they maintain the web application for me
See you at http://o2platform.wordpress.com (with time I will move the try-o2.com domain to over there)
Final comment: Super Kudos to the Drupal team for at least exposing the version status information so clearly. Unfortunately that is not good enough, and as a user I was left in a very uncomfortable position (where what I wanted was a 1-click 'server-side' upgrade button (with a backup/restore capability))
This is what it looked like:
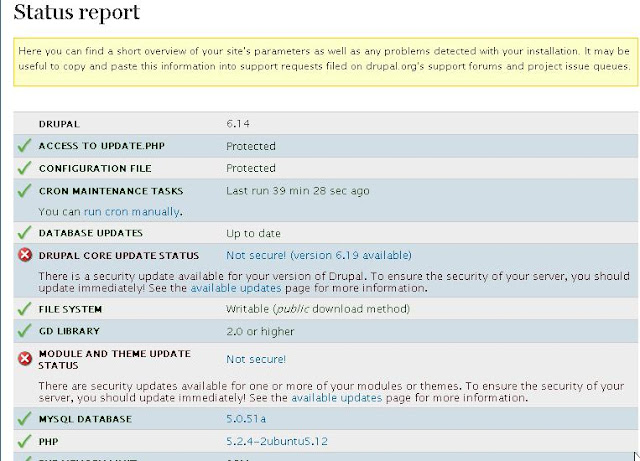
 I was happy with the design and funcionality of this site and Drupal, BUT the problem happened when I recently logged in into the admin section of the website and saw this:
I was happy with the design and funcionality of this site and Drupal, BUT the problem happened when I recently logged in into the admin section of the website and saw this:Ok, this doesn't sound good. I wonder what does 'One or more problems' really mean. Lets see what the 'status report' says:
OK, so it looks like I need to update the Drupal Core and some Module/Theme.
Let's try the 'available updates':
I have to say that it is great that Drupal is already able to give me this level of alerts and information, BUT, their solution is now dependent on me downloading a bunch of of gz files (http://ftp.drupal.org/files/projects/drupal-6.19.tar.gz and http://ftp.drupal.org/files/projects/devel-6.x-1.22.tar.gz) and INSTALL them !!!!.
WTF, I don't want to have to maintain this website, in fact I don't even know how it was created!! Remember that whole point of using something like Drupal 6 Appliance from TurnkeyLinux (http://www.turnkeylinux.org/drupal6) was to spend no time maintaining it (isn't the 'Applicance' concept supposed to be 'hands-free'!!!)
Just to make sure I was not missing something obvious I went to the 'Release Notes' for one of the updates
But it contained NO information on how to do the upgrade that I was asked to do. A quick browse on the website also didn't help!
And what is really infuriating from a user's point of view, is that I have NO information on:
a) WHY this is even relevant to me,
b) what is the RISK impact, and
c) what other alternative (but as effective) mitigating strategies there are.
How am I supposed to make a business decision to spend the time, money and resources to fix this issue if I don't know:
- If my current deployment of Drupal is affected by the security vulnerabilities discovered
- Where are the security vulnerabilities?
- Can I disable the modules that have it and be done with it?
- What is the impact of these vulnerabilities?
- Have they been exploited in higher profile Drupal installations?
- What does an attack looks like (i.e what are the early signs of exploitation)
- How do I know if I have been exploited?
- Are there other mitigating factors? For example can I use a WAF to protect the affected parts?
Since is bound to happen in the future, and Drupal's update mechanisms is equal to 'brain surgery' (remember that I didn't install it, so I would have a bit a learning curve to do it properly), I'm left with no choice but to KILL the website (i.e. the Amazon EC2 image that powers it) and move to WordPress.com since at least they maintain the web application for me
See you at http://o2platform.wordpress.com (with time I will move the try-o2.com domain to over there)
Final comment: Super Kudos to the Drupal team for at least exposing the version status information so clearly. Unfortunately that is not good enough, and as a user I was left in a very uncomfortable position (where what I wanted was a 1-click 'server-side' upgrade button (with a backup/restore capability))
Monday, 18 October 2010
OWASP WebScarab - Custom O2
The latest version of the O2 Platform has support for OWASP's WebScarb via a Custom O2 GUI that exposes a number of WebScarab's funcionality and allows its easy scripting and automation.
Here are the main features:
Here are the main features:
- Install and uninstall WebScarab
- Multiple Gui Automations
- Switch Interface Modes (from "Advanced -> Lite" and "Lite->Advanced")
- Save current Conversations
- Load previously saved Conversations
- IE Automation via dynamically compiled O2 Scripts (allowing the workflow where a dynamic script is executed by IE and the traffic captured by WebScarab)
- Load and filter saved convertations
- as a SQL-like dynamic query - and then using an GUI that allows the real-time execution of .NET LINQ Queries)
- as O2Findings (via a special WebScarab->O2Findings converter) - and then using O2 powerful Findings Filtering capabilities
Friday, 15 October 2010
Example of Gui Automation: Controlling Notepad from O2
Here is a good example of the O2's GUI Automation capabilities that really allow the instrumentation of other Windows Applications and to perform client side application security reviews:
- Wiki page: http://www.o2platform.com/wiki/O2_Script/PoC_-_Automating_Notepad.h2
- YouTube video: http://www.youtube.com/watch?v=as0Ov-Pfq7M
- O2 Script: http://code.google.com/p/o2platform/source/browse/trunk/O2_Scripts/APIs/Windows/White/PoC%20-%20Automating%20Notepad.h2
Thursday, 14 October 2010
Tool - Using OpenPgp to Encrypt or Decrypt.h2
I just published a new O2 script/gui that solves a long problem/pain that I had for a long, long time: the quick and easy PGPing of texts and files.
This O2 Tool (i.e. script) is already pushed to the SVN (available if you have the latest ClickOnce version) and has the following features:
http://www.o2platform.com/wiki/O2_Script/Tool_-_Using_OpenPgp_to_Encrypt_or_Decrypt.h2
Here is the YouTube Video http://www.youtube.com/watch?v=_Cd8AfZyWMs (created with the new O2 Video creator tool which helps me to quicklly create this type of videos)
And here are a couple screenshots

This O2 Tool (i.e. script) is already pushed to the SVN (available if you have the latest ClickOnce version) and has the following features:
- create PGP Keys
- store PGP configuration on xml files (which are easy to move around
- GUI to encrypt Text
- GUI to decrypt Text
- GUI to encrypt and decrypt Files
- Supports workflow where the PassPhase is kept private and the Public + Private keys are sent unencrypted to the client
http://www.o2platform.com/wiki/O2_Script/Tool_-_Using_OpenPgp_to_Encrypt_or_Decrypt.h2
Here is the YouTube Video http://www.youtube.com/watch?v=_Cd8AfZyWMs (created with the new O2 Video creator tool which helps me to quicklly create this type of videos)
And here are a couple screenshots

Wednesday, 6 October 2010
UnitTest for Twitter "XSS Vuln in ManageDomains"
This script is focused on a recently disclosed and patched XSS vulnerability in Twitter :
- WIKI page with technical details and the script's source code: http://www.o2platform.com/wiki/O2_Script/UnitTest_Twitter_XSS_Vuln_in_ManageDomains.cs
- YouTube Video that shows this script in action: http://www.youtube.com/watch?v=DpDiGpzaVw0
Labels:
O2 Platform
O2 Platform script to create Twitter accounts (with CAPTCHA support)
Part of the challenge of automating/scripting web application security vulnerabilities is the need to handle multi-stage data inputs.
A good example (and PoC) are account creation wizards, which these days (for example) include a captcha question.
To show how this can be done in O2, I've just coded a script that shows this in action:
A good example (and PoC) are account creation wizards, which these days (for example) include a captcha question.
To show how this can be done in O2, I've just coded a script that shows this in action:
- Tool_-_Twitter_Account_Creation.h2 - Wiki page with technical details and screenshots
- O2 Platform - Tool - Create Twitter Accounts.avi - YouTube Video
Labels:
O2 Platform,
WatiN
Tuesday, 5 October 2010
Using a MAC address to find your physical location (via Google Location Services)
If you see Samy's presentation "How I meet your Girlfriend" you will be shown a very good example of what I think is a "perfect storm". Amongst the multiple examples he give, he shows how from a MAC address (which he gets via a router XSS) he is able to discover the girlfriend's address.
And how does Samy does it? He uses Google's Location Services REST API, which returns a nice populated JSON response, filled with location information (longitude, latitude, address, accuracy, etc...), when provided a valid/known-to-Google MAC address. Google knows about MAC addresses from the data feeds provided either by Google's Street View cars or by passing-by pedestrians using Android phones.
After seeing a couple times Samy's presentation I was curious to see if it really worked that way, and unfortunately (for privacy) it does.
For more details on how this works see the O2 Platform script that I wrote in a couple hours yesterday which will find your local router and show you your current location. This wiki page has more technical details and screeshoots: Tool_-_Find_Physical_Location_via_MAC_Address_(using_Google's_APIs).h2
Here are a couple screenshots of the script in action:
And how does Samy does it? He uses Google's Location Services REST API, which returns a nice populated JSON response, filled with location information (longitude, latitude, address, accuracy, etc...), when provided a valid/known-to-Google MAC address. Google knows about MAC addresses from the data feeds provided either by Google's Street View cars or by passing-by pedestrians using Android phones.
After seeing a couple times Samy's presentation I was curious to see if it really worked that way, and unfortunately (for privacy) it does.
For more details on how this works see the O2 Platform script that I wrote in a couple hours yesterday which will find your local router and show you your current location. This wiki page has more technical details and screeshoots: Tool_-_Find_Physical_Location_via_MAC_Address_(using_Google's_APIs).h2
Here are a couple screenshots of the script in action:
Saturday, 2 October 2010
With O2, I am a Curator of Open Source Software
A couple days ago I saw the amazing and highly recomended Jason Fried Web 2.0 Keynote – Be a Software Curator video presentation (from 37 Signals) where Jason made the argument that as software developers we have to be curators (as in a Museum Curator) when selecting the features we chose to implement for the software or web applications we are developing.
In that presentation, one of his strongest analogies is the fact that Software has no physical properties (as in weight, shape, smell, transparency, etc...) which makes it very hard for its users to provide immediate feedback on the software/webapp they are about to use, and, more importantly, it denies the developers with valuable information on how well ‘designed’ their application is (not designed as in 'look-and-feel + graphics', but ‘designed’ as in ‘Design the experience’)
This means that we as software developers must be very disciplined on which customers/users we listen to, and what we decide to do with our limited development resources.
And this is exactly what Curators do in Museums. They understand what their target audience wants, they find the artists + exhibitions items that match his/hers (the Curator) vision and then finally he/she ‘Designs’ the user experience in order to maximize the user’s benefit from attending the exhibition.
After thinking about this concept for a while, I realized that it also fits very well with what I try to do in the O2 Platform when I:
Basically, I’m a Curator for Open Source with the responsibility to research, test, select and customize APIs to solve specific Web Application Security problems.
In that presentation, one of his strongest analogies is the fact that Software has no physical properties (as in weight, shape, smell, transparency, etc...) which makes it very hard for its users to provide immediate feedback on the software/webapp they are about to use, and, more importantly, it denies the developers with valuable information on how well ‘designed’ their application is (not designed as in 'look-and-feel + graphics', but ‘designed’ as in ‘Design the experience’)
This means that we as software developers must be very disciplined on which customers/users we listen to, and what we decide to do with our limited development resources.
And this is exactly what Curators do in Museums. They understand what their target audience wants, they find the artists + exhibitions items that match his/hers (the Curator) vision and then finally he/she ‘Designs’ the user experience in order to maximize the user’s benefit from attending the exhibition.
After thinking about this concept for a while, I realized that it also fits very well with what I try to do in the O2 Platform when I:
- have a particular problem (let’s say I want to automate a Browser workflow/exploit/UnitTest),
- do a research on the currently available Open Source tools that could address that problem (Selenium, WatiN, .NET Browser Control, multiple CodePlex projects, etc...),
- try a couple that look like the best fit (writing APIs to help consuming them)
- use these APIs in real work engagements
- based on the success use of the original API + O2 Customizations (and Extension Methods Wrappers), arrive at a conclusion on which one is the best Open Source API to use (in this case WatiN)
- Package the chosen API in easy to use modules that are then exposed to the wider O2 community
Basically, I’m a Curator for Open Source with the responsibility to research, test, select and customize APIs to solve specific Web Application Security problems.
Friday, 1 October 2010
Using O2 to Parse WSDL files and submit requests/payloads
The .NET's SDK comes with a tool that creates a C# file from a WSDL (which is what Visual Studio uses when adding a Web Reference).
This file can can then be used to automatically enumerate methods + parameters, and provide nice C# stubs to send requests or fuzz payloads (and that is just a warm up on what you can do with it).
O2 has support for WSDL creation via this script: http://code.google.com/p/
To see it in action here is a example of how to consume it using O2's C# Scripting Environment http://www.o2platform.com/
This file can can then be used to automatically enumerate methods + parameters, and provide nice C# stubs to send requests or fuzz payloads (and that is just a warm up on what you can do with it).
O2 has support for WSDL creation via this script: http://code.google.com/p/
To see it in action here is a example of how to consume it using O2's C# Scripting Environment http://www.o2platform.com/
Great Comments on the O2 Subscription Model
OWASP Leader Michael Coates had a some great comments on the O2 Subscription model when I asked a while back if it was compatible with OWASP's values and mission.
Here are his words (slightly edited since the original version was commenting on the previous version which had a couple extra OWASP membership related items):
"...To my knowledge, this is the first OWASP project that has attempted a financing model. It is important for us (OWASP leaders) to be open and communicate the correct ways for OWASP projects to offer services that are not free. Below I've included the OWASP principles and my thoughts on their relation to Dinis's idea.
OWASP Principles - http://www.owasp.org/index.
Free & Open
As Dinis mentioned, his code is open to everyone at no charge. The O2 tool can be downloaded and used without paying any of the subscription fees. No problem here.
Governed by rough consensus & running code
Not relevant to this issue except that the overall consensus of the OWASP leaders should be considered.
Abide by a code of ethics
No problems here
Not-for-profit
OWASP itself is not for profit. But what about individual projects? The O2 project is rightfully (in my opinion) charging for Dinis's time to offer premium support to commercial customers. Many of us, Dinis included, volunteer large amounts of time to OWASP. However, volunteering and providing commercial grade support or two totally different things. This is a fine move in my opinion. Many companies will not adopt an open source software if a formal support policy cannot be established. So although I don't personally have any problems here, how do we reconcile this situation with our principles? Perhaps the answer is related to point #2 (rough consensus) and this sort of email discussion
Not driven by commercial interests
Although O2 technically would become "commercial" in a small way I don't see any problem here. This item is meant to address the overall objectivity of OWASP in always promoting the best security advice that is not tainted by a particular company's motivation.
Risk based approach
Not a problem. In fact O2 reinforces this principle.
Overall I think Dinis's approach to a subscription model for support is not a problem. This model is used by other open source organizations such as red hat (https://www.redhat.com/wapps/
...
Conclusion
..."
Here are his words (slightly edited since the original version was commenting on the previous version which had a couple extra OWASP membership related items):
"...To my knowledge, this is the first OWASP project that has attempted a financing model. It is important for us (OWASP leaders) to be open and communicate the correct ways for OWASP projects to offer services that are not free. Below I've included the OWASP principles and my thoughts on their relation to Dinis's idea.
OWASP Principles - http://www.owasp.org/index.
Free & Open
As Dinis mentioned, his code is open to everyone at no charge. The O2 tool can be downloaded and used without paying any of the subscription fees. No problem here.
Governed by rough consensus & running code
Not relevant to this issue except that the overall consensus of the OWASP leaders should be considered.
Abide by a code of ethics
No problems here
Not-for-profit
OWASP itself is not for profit. But what about individual projects? The O2 project is rightfully (in my opinion) charging for Dinis's time to offer premium support to commercial customers. Many of us, Dinis included, volunteer large amounts of time to OWASP. However, volunteering and providing commercial grade support or two totally different things. This is a fine move in my opinion. Many companies will not adopt an open source software if a formal support policy cannot be established. So although I don't personally have any problems here, how do we reconcile this situation with our principles? Perhaps the answer is related to point #2 (rough consensus) and this sort of email discussion
Not driven by commercial interests
Although O2 technically would become "commercial" in a small way I don't see any problem here. This item is meant to address the overall objectivity of OWASP in always promoting the best security advice that is not tainted by a particular company's motivation.
Risk based approach
Not a problem. In fact O2 reinforces this principle.
Overall I think Dinis's approach to a subscription model for support is not a problem. This model is used by other open source organizations such as red hat (https://www.redhat.com/wapps/
...
Conclusion
- I support Dinis's plan to offer a subscription service for commercial support of O2 and believe this type of model is necessary to take OWASP projects to the next level
- I believe this is inline with OWASP principles
- ....
..."
Update on O2 Subscription Model
Following the feedback received when I pushed the first version of the O2 Subscription model , I've made a number of changes which should be a better fit for the community and target user base.
As before, there are 3 Subscription levels, but this time around there is much bigger focus on the creation and support of an customized version of O2 for each subscriber (and based on the comments made I removed the OWASP-related options)
Here is a table that represents the new model:
Currently there are 3 companies subscribed and I'm working with them on their custom version of O2.
For more details see this O2 - Commercial Services presentation or visit the O2 Subscriptions page at the O2 Website
------------------------------------------------
Important note: this is NOT a service provided by OWASP and the OWASP foundation has no direct involvement or responsibility in the delivery or fulfillment of these subscriptions
As before, there are 3 Subscription levels, but this time around there is much bigger focus on the creation and support of an customized version of O2 for each subscriber (and based on the comments made I removed the OWASP-related options)
Here is a table that represents the new model:
Currently there are 3 companies subscribed and I'm working with them on their custom version of O2.
For more details see this O2 - Commercial Services presentation or visit the O2 Subscriptions page at the O2 Website
------------------------------------------------
Important note: this is NOT a service provided by OWASP and the OWASP foundation has no direct involvement or responsibility in the delivery or fulfillment of these subscriptions
Sunday, 26 September 2010
Why do we think we can comment on the 'easiness' level of XSS?
Here is an important question: "What gives Security Consultants the right to comment on how 'easy' it is to fix an XSS vulnerability?"
After all, it is not the Security Consultant's that:
1) needs to figure out:
- the root-cause analysis of the XSS reported?
- where it should be fixed?
- what is the REAL impact to the business?
- what are the side effects of applying the code changes?
2) has to make business case to fix it (and delaying XYZ feature)
3) has to actually fix the vulnerability
4) will be fired if the fixed is applied wrongly
5) will be the one that has the deal any side-effects created by the fixes
6) has to pay for it
Surely the only people qualified (and entitled) to make this 'easiness' assessment (i.e. of how 'easy' it is to fix a particular vulnerability) are the application developers and business owners!
Now think about how it must feel from the other side (i.e. the developers) when we (security consultants) tell them that it is 'easy' to fix what we just reported them.
And just to add insult to injury, we also like to tell them (the developers) that they need 'Training' (i.e. "...we think that you should go back to School and learn about security before you are allowed to write more code...")
It is 'easy' to say that that is 'easy' to fix...
... specially by the crowd whose responsibility ends when the problem/XSS is reported
After all, it is not the Security Consultant's that:
1) needs to figure out:
- the root-cause analysis of the XSS reported?
- where it should be fixed?
- what is the REAL impact to the business?
- what are the side effects of applying the code changes?
2) has to make business case to fix it (and delaying XYZ feature)
3) has to actually fix the vulnerability
4) will be fired if the fixed is applied wrongly
5) will be the one that has the deal any side-effects created by the fixes
6) has to pay for it
Surely the only people qualified (and entitled) to make this 'easiness' assessment (i.e. of how 'easy' it is to fix a particular vulnerability) are the application developers and business owners!
Now think about how it must feel from the other side (i.e. the developers) when we (security consultants) tell them that it is 'easy' to fix what we just reported them.
And just to add insult to injury, we also like to tell them (the developers) that they need 'Training' (i.e. "...we think that you should go back to School and learn about security before you are allowed to write more code...")
It is 'easy' to say that that is 'easy' to fix...
... specially by the crowd whose responsibility ends when the problem/XSS is reported
How many 'easy-to-fix' XSS have we fixed in the last 12 months
On the topic of 'easy-to-fix' XSS, one question that we should be able to answer (as an industry) is 'How many of those easy-to-fix have been actually fixed and pushed into production'.
After all, if they are 'easy' to fix (and cheaper to create,test, deploy, etc...) surely that means that the affected parties (application owners and developers) will have very little resistance in doing those fixes, right?
So where can I find these numbers? What I am after are three values:
1) # number of 'easy-to-fix' XSS discovered on real-world applications
2) # number of 'easy-to-fix' XSS discovered that were actually fixed and pushed into production
3) % of XSS discovered that fall into the 'easy-to-fix' category
If we don't have these numbers, how do we know we are being effective? and that they are indeed 'easy-to-fix'
On a Twitter thread after my previous blog post, Chris from Veracode commented that he guesses (i.e. no hard-data) that about 50% of the 'easy-to-fix' XSS that they have found at Veracode are now fixed and deployed into production.
Even assuming that that 50% number is correct (which looks a bit high to me, and if I remember correctly WhiteHat's numbers are much lower), shouldn't the 'easy-to-fix' number be much higher? After all they are 'easy-to-fix'
.....
As you can tell by my use of quotes on the 'easy-to-fix' concept, I don't buy that fixing XSS are easy to fix.
Even in the cases where the 'fix' is 'just' applying an encoding to particular method (let's say from Response.Write(Request["name"]) to Response.Write(AntiXSS.HtmlEncode(Request["Name"])) ) there is a big difference between 'making a code change' and 'pushing it into production'.
Here is a quick list of what should happen when a developer knows about an 'easy-to-fix' XSS vulnerability:
1) XSS is discovered by security consultant
2) XSS is communicated to the development team
3) Development team analyse the XSS finding:
- reproduce the XSS reported
- discover what causes the XSS (root-cause analysis)?
- what is the DOM context of the XSS injection point (Html, Attribute, Javascript block, CSS)
- was it a single instance/mistake or is it a systemic flaw?
- where can it be fixed?
- of the multiple places it can be fixed what is the one with the least impact?
- can it be solved/mitigated without making code changes, for example using an config setting or a WAF? (i.e. virtual patching)
- is there a clear understanding of the side-effects of applying the fixes?
- are there cases (or potential) for double encoding problems? (i.e. is there understanding of all the code + data paths that lead to the location of the fix?)
- were other parts of the application created with the assumption that there would be no encoding on that particular field? (which will break once the fix is applied)
- who is going to pay for the fix? the developers? the client?
4) Once a strategy is created to fix the XSS, put it on the development schedule and apply the fix
5) Test the fix and make sure:
- that the XSS was correctly resolved/mitigated (who will do this? the current testers/developers that were not aware of the XSS in the first place, or the original security consultant?)
- is there any business impact (i.e. does the application still behaves the same way and there is NO user-experience impact). Ideally this should be done by the QA team
6) Deploy the fix into production
(note that this is a simplified version of what tends to happen in the real world, since there are many other factors that affect this: from internal/external politics, to management support for security fixes, to lack of attacks, to the fact that the original team that created the application is long gone and the developer allocated to do the 'easy-to-fix' change doesn't really know how the application he/she is about to fix actually works,etc...)
Some would call the above process 'easy-to-fix' ....
For me 'easy-to-fix' code changes (if there is such a thing) are actions that:
- don't take much time,
- the amount of work (and side effects) that needs to be done is easy to understand/visualise
- are cheap
- can be deployed into production quickly and without worries
- DON'T have any potential to create business/user impact (this is the most important one)
- are in essence, invisible to just about all parties involved
I think the crowd that calls XSS 'easy-to-fix' are confusing 'looks easy to make the code change that I think would work' with 'making a code change that accurately resolves the reported problem without causing any impact to the application' (which is what matters to the developers/business-owners)
My fundamental problem with the 'easy-to-fix' concept is that it is calling the developers (and application owners):
- names (as in: "you guys are stupid for not fixing those problems, after all they are 'easy-to-fix'),
- it is alienating them, and
- it is showing them that we don't have a very good idea on how their applications and business work.
To see a more detailed explanation of this gap between security consultants 'recommendations' and what the business/developers think of it, see John Viega's Keynote at OWASP's AppSec Ireland conference
After all, if they are 'easy' to fix (and cheaper to create,test, deploy, etc...) surely that means that the affected parties (application owners and developers) will have very little resistance in doing those fixes, right?
So where can I find these numbers? What I am after are three values:
1) # number of 'easy-to-fix' XSS discovered on real-world applications
2) # number of 'easy-to-fix' XSS discovered that were actually fixed and pushed into production
3) % of XSS discovered that fall into the 'easy-to-fix' category
If we don't have these numbers, how do we know we are being effective? and that they are indeed 'easy-to-fix'
On a Twitter thread after my previous blog post, Chris from Veracode commented that he guesses (i.e. no hard-data) that about 50% of the 'easy-to-fix' XSS that they have found at Veracode are now fixed and deployed into production.
Even assuming that that 50% number is correct (which looks a bit high to me, and if I remember correctly WhiteHat's numbers are much lower), shouldn't the 'easy-to-fix' number be much higher? After all they are 'easy-to-fix'
.....
As you can tell by my use of quotes on the 'easy-to-fix' concept, I don't buy that fixing XSS are easy to fix.
Even in the cases where the 'fix' is 'just' applying an encoding to particular method (let's say from Response.Write(Request["name"]) to Response.Write(AntiXSS.HtmlEncode(Request["Name"])) ) there is a big difference between 'making a code change' and 'pushing it into production'.
Here is a quick list of what should happen when a developer knows about an 'easy-to-fix' XSS vulnerability:
1) XSS is discovered by security consultant
2) XSS is communicated to the development team
3) Development team analyse the XSS finding:
- reproduce the XSS reported
- discover what causes the XSS (root-cause analysis)?
- what is the DOM context of the XSS injection point (Html, Attribute, Javascript block, CSS)
- was it a single instance/mistake or is it a systemic flaw?
- where can it be fixed?
- of the multiple places it can be fixed what is the one with the least impact?
- can it be solved/mitigated without making code changes, for example using an config setting or a WAF? (i.e. virtual patching)
- is there a clear understanding of the side-effects of applying the fixes?
- are there cases (or potential) for double encoding problems? (i.e. is there understanding of all the code + data paths that lead to the location of the fix?)
- were other parts of the application created with the assumption that there would be no encoding on that particular field? (which will break once the fix is applied)
- who is going to pay for the fix? the developers? the client?
4) Once a strategy is created to fix the XSS, put it on the development schedule and apply the fix
5) Test the fix and make sure:
- that the XSS was correctly resolved/mitigated (who will do this? the current testers/developers that were not aware of the XSS in the first place, or the original security consultant?)
- is there any business impact (i.e. does the application still behaves the same way and there is NO user-experience impact). Ideally this should be done by the QA team
6) Deploy the fix into production
(note that this is a simplified version of what tends to happen in the real world, since there are many other factors that affect this: from internal/external politics, to management support for security fixes, to lack of attacks, to the fact that the original team that created the application is long gone and the developer allocated to do the 'easy-to-fix' change doesn't really know how the application he/she is about to fix actually works,etc...)
Some would call the above process 'easy-to-fix' ....
For me 'easy-to-fix' code changes (if there is such a thing) are actions that:
- don't take much time,
- the amount of work (and side effects) that needs to be done is easy to understand/visualise
- are cheap
- can be deployed into production quickly and without worries
- DON'T have any potential to create business/user impact (this is the most important one)
- are in essence, invisible to just about all parties involved
I think the crowd that calls XSS 'easy-to-fix' are confusing 'looks easy to make the code change that I think would work' with 'making a code change that accurately resolves the reported problem without causing any impact to the application' (which is what matters to the developers/business-owners)
My fundamental problem with the 'easy-to-fix' concept is that it is calling the developers (and application owners):
- names (as in: "you guys are stupid for not fixing those problems, after all they are 'easy-to-fix'),
- it is alienating them, and
- it is showing them that we don't have a very good idea on how their applications and business work.
To see a more detailed explanation of this gap between security consultants 'recommendations' and what the business/developers think of it, see John Viega's Keynote at OWASP's AppSec Ireland conference
Saturday, 25 September 2010
Can we please stop saying that XSS is boring and easy to fix!
XSS (Cross Site Scripting) is probably one of the harder problems to solve in a web application because fixing it properly implies that one has a perfect understanding of what is 'code' and what is 'data'
The problem with XSS (and most other web injection variation) is that the attacker/exploit is able to move from a 'data' field into a 'code' execution environment.
So saying that XSS is easy to fix and eradicate is the same thing as saying that Buffer Overflows are easy to fix and eradicate.
Also, saying that we know how to solve XSS is a red-herring because we DON'T know how to solve it. What do know is how to mitigate it and for the cases where we DO understand were we are mixing code and data, we can apply special protections.
But even today, in 2010, protecting against XSS is something that the developers MUST do, versus something that happens (and is enforced) by default by the frameworks/APIs used.
Take .NET for example. Although there is quite a lot of XSS protection in the .NET framework (auto-detection against common XSS exploits, most controls have auto-encoding by default, etc...) we still see a lot of XSS on ASP.NET applications. The reason these exists is because it is very hard for developers to have a full understanding of the encoding and location of the outputs they are creating. And until we solve this 'visibility' problem, we will not solve XSS
On a positive note, the SRE (Security Runtime Engine) that ships with the Anti-XSS API is an amazing tool because it transparently adds encoding to .NET Web Controls (and it takes into account double encoding problems which is what makes it amazing)
The only way we will ever start dealing properly with XSS is if:
a) the framework(s) developers use have context-aware-encoding on ALL outputs
b) there is no easy way to write raw HTML directly to the response-stream
c) there is no easy way for developers to mix HTML code with Data
d) when HTML needs to be created programatically, that needs go be outputted via an HTML DOM aware encoding API/method (like the ones that .NET AntiXSS has)
e) there are static analysis rule packs for each of the frameworks that document (in rules) the programmatically combinations that make XSS possible (in that framework/API)
f) the developers have immediate (or before checking-in code into production) feedback when they create an XSS in their applications
g) web applications have a communication channel with browsers, which will allow browsers to better understand what is code and what is data (Mozilla CSP is a great step in this direction)
The key to really deal with XSS is e) and f) , since these take into account the scenario that developers will mix code, and even in the best designed APIs/Frameworks there will ALWAYS be combinations that create XSS. Also, without this understanding of the data/code mappings (which is where XSS lives) we will struggle to create mappings for g)
One of my key strategies when developing the O2 Platform was to create an environment that helps the creation and propagation of these 'Framework Rule Packs', since from my point of view, every version of every framework (and APIs) will need one of theses Rule Packs.
Remember that: security knowledge, that is not available, in an consumable format by tools or humans, AT the exact moment when it is needed (by developers, system architects, etc...), is almost as good as non-existent.
For example: "... an MSDN article that explains that the FormsAuthentication cookie is not invalidated on logout... " is not good enough
what we need is an "...alert or note that only appears when the developers use FormsAuthentication that explains (with PoCs) the fact that (on sign out) the only thing that happens is that the client side cookies are deleted from the user's browser...". The PoCs (dynamic or static) are very important in this example, since in most cases the real vulnerability will only be relevant in more feature-rich versions of the application.
Bottom line: Solving XSS means solving the separation of Code vs Data in web applications
And THAT ... is something that we are still quite far off
The problem with XSS (and most other web injection variation) is that the attacker/exploit is able to move from a 'data' field into a 'code' execution environment.
So saying that XSS is easy to fix and eradicate is the same thing as saying that Buffer Overflows are easy to fix and eradicate.
Also, saying that we know how to solve XSS is a red-herring because we DON'T know how to solve it. What do know is how to mitigate it and for the cases where we DO understand were we are mixing code and data, we can apply special protections.
But even today, in 2010, protecting against XSS is something that the developers MUST do, versus something that happens (and is enforced) by default by the frameworks/APIs used.
Take .NET for example. Although there is quite a lot of XSS protection in the .NET framework (auto-detection against common XSS exploits, most controls have auto-encoding by default, etc...) we still see a lot of XSS on ASP.NET applications. The reason these exists is because it is very hard for developers to have a full understanding of the encoding and location of the outputs they are creating. And until we solve this 'visibility' problem, we will not solve XSS
On a positive note, the SRE (Security Runtime Engine) that ships with the Anti-XSS API is an amazing tool because it transparently adds encoding to .NET Web Controls (and it takes into account double encoding problems which is what makes it amazing)
The only way we will ever start dealing properly with XSS is if:
a) the framework(s) developers use have context-aware-encoding on ALL outputs
b) there is no easy way to write raw HTML directly to the response-stream
c) there is no easy way for developers to mix HTML code with Data
d) when HTML needs to be created programatically, that needs go be outputted via an HTML DOM aware encoding API/method (like the ones that .NET AntiXSS has)
e) there are static analysis rule packs for each of the frameworks that document (in rules) the programmatically combinations that make XSS possible (in that framework/API)
f) the developers have immediate (or before checking-in code into production) feedback when they create an XSS in their applications
g) web applications have a communication channel with browsers, which will allow browsers to better understand what is code and what is data (Mozilla CSP is a great step in this direction)
The key to really deal with XSS is e) and f) , since these take into account the scenario that developers will mix code, and even in the best designed APIs/Frameworks there will ALWAYS be combinations that create XSS. Also, without this understanding of the data/code mappings (which is where XSS lives) we will struggle to create mappings for g)
One of my key strategies when developing the O2 Platform was to create an environment that helps the creation and propagation of these 'Framework Rule Packs', since from my point of view, every version of every framework (and APIs) will need one of theses Rule Packs.
Remember that: security knowledge, that is not available, in an consumable format by tools or humans, AT the exact moment when it is needed (by developers, system architects, etc...), is almost as good as non-existent.
For example: "... an MSDN article that explains that the FormsAuthentication cookie is not invalidated on logout... " is not good enough
what we need is an "...alert or note that only appears when the developers use FormsAuthentication that explains (with PoCs) the fact that (on sign out) the only thing that happens is that the client side cookies are deleted from the user's browser...". The PoCs (dynamic or static) are very important in this example, since in most cases the real vulnerability will only be relevant in more feature-rich versions of the application.
Bottom line: Solving XSS means solving the separation of Code vs Data in web applications
And THAT ... is something that we are still quite far off
Monday, 9 August 2010
New O2 Subscription Model
Just launched at: http://www.o2platform.com/index.php/O2 Subscriptions
------------------------------------------------------------------------------------------
In order to fully support to the companies that commit to using O2 and use it on commercial engagements, the following subscription-based services are now available:
Bronze : 1,000 USD per Quarter
- Certified Monthly Build (with some customization of modules included)
- Monthy Documentation (with some customization of modules included)
- 1x copy of O2 Book(s) (when released)
- 1x shared amazon EC Image (containing latest version of O2 and demo files)
- Private discusion forum
- 1x OWASP Individual Membership
- Officially recognized as 'O2 Platform BRONZE Service Provider'
Silver: 5,000 USD per Quarter
- Certified Monthly Build (with major customization of modules included)
- Monthy Documentation (with major customization of modules included)
- 3x copy of each O2 Book(s) (when released)
- 3x shared amazon EC Images + 1x dedicated amazon EC Image (containing latest or the customized version of O2)
- Private discusion forum (with 10x priority tickets)
- 4h of Personalized Training (remote)
- 2x Tickets to an OWASP Conference
- 5x OWASP Individual Membership
- Officially recognized as 'O2 Platform SILVER Service Provider'
Gold: 15,000 USD per Quarter
- Certified Monthly Build (with customization of modules included and GUI Branding)
- Monthy Documentation (with customization of modules included and GUI Branding)
- 5x copy of each O2 Book(s) (when released)
- 5x dedicated amazon EC Image (containing latest or the customized version of O2)
- Private discusion forum (with 20x priority tickets)
- 2 days of personalized training (either remote or locally (if logistically possible))
- 5x Tickets to an OWASP Conference
- 1x OWASP Corporate Membership (with the 40% of 5000USD membership allocated to the O2 Platform)
- Officially recognized as 'O2 Platform GOLD Service Provider'
These subscription can be started or canceled at any time, and could follow periods of increased activity around O2.
For custom or focused O2 development see the O2 Pledges
Note that this is NOT a service provided by OWASP and the OWASP foundation has no direct involvement or responsibility in the delivery or fulfillment of these subscriptions
------------------------------------------------------------------------------------------
OWASP/O2 US Tour Aug 9-17 (6 cities in 8 days)
Hi I'm about to embark on a great adventure and I hope you will be able to join me along the way.
For the next 8 days I will be traveling to 6 US cities, visiting the local OWASP chapter and doing OWASP/O2 presentations. This is also a great opportunity to meet a number of local chapter/project leaders and have a number of brainstorming sessions on OWASP.
Here is my itinerary:
For the next 8 days I will be traveling to 6 US cities, visiting the local OWASP chapter and doing OWASP/O2 presentations. This is also a great opportunity to meet a number of local chapter/project leaders and have a number of brainstorming sessions on OWASP.
Here is my itinerary:
- Mon 9th: NYC http://www.owasp.org/index.
php/NYNJMetro - Tue 10th: Minneapolis http://www.owasp.org/index.
php/Minneapolis_St_Paul - Wed 11th: Seatle http://www.owasp.org/index.
php/Seattle - Thu 12th: Atlanta http://www.owasp.org/index.
php/Atlanta_Georgia#tab= Chapter_Meetings - Fri 13th: San Antonio http://www.owasp.org/index.
php/San_Antonio - Sat 14th: San Antonio
- Sun 15th: Washington DC
- Mon 16: Washington DC , Virginia (TBC) http://www.owasp.org/index.
php/Virginia - Tue 17: Washington DC
If you are around this area and want to meet up to talk about OWASP or O2, then ping me directly and lets make it happen
See you on the road......
Friday, 30 July 2010
What is going on with you (Jul 2010) and are you at BlackHat / DefCon?
Since I have a number of similar questions on my Inbox, it will be easier to reply to them here :)
No, I'm at at BlackHat and DefCon (I'm an independent contractor now so I have no company to send the bills to and I was not able to get O2 to generate enough revenue to organize a BH/DC gathering)
Regarding what has been going on, here is a selection of blog posts that cover the last couple months:
Labels:
OunceLabs
O2 Platform, ideas on where to start
If you want to delve deeper into O2's world I would say that your first step is to replicate the BlackBox and WhiteBox examples that I have already created and published with O2 (check out the Demo's Tab in the main GUI).
Some pointers:
- If you are on a 32bit box, I would recommend that you use the latest version of O2 (which is only available via the ClickOnce install ) since it as a ton of new features
- Install HacmeBank and WebGoat locally
- Write a BlackBox script to exploit an SQL Injection in HacmeBank and an XSS in WebGoat
- From HacmeBank's Source Code, build its MethodStreams and find the SQL Injections on the WebServices, and connect the WebLayer with the WebServices Layer
- Transform the above scripts in Unit tests
- Create a document with your experiments containing tons of screenshots about it
- Create a video with your experiments (and publish it, or send it to me)
If you have any issues, join the O2 Platform mailing list and ask a question.
There is also an Amazon EC2 image that I have with O2 fully configured which I can give you access if you ping me directly
Wednesday, 28 July 2010
New funding model for O2's Development
This is the first of a series of blog entries that I will write on the topic of "O2 Funding model and the multiple Business Modules that are (in my point of view) 100% compatible with O2's Open Source positioning."
----- (content from the current version of http://o2platform.com/wiki/O2_Pledges
With the objective to create a funding source for O2's development, the following Pledges have been set-up at Pledgie.com:
O2 Specific
Framework specific
- O2 Platform - 'SharePoint/MOSS' Rule Pack
- O2 Platform - 'ASP.NET MVC' Rule Pack
- O2 Platform - 'J2EE Struts' Rule Pack
- O2 Platform - 'J2EE Spring MVC' Rule Pack
Industry sector specific
- O2 Platform - 'BlackBox / Penetration Testing' RulePack
- O2 Platform - 'WhiteBox / Source Analysis' Rule Pack
- O2 Platform - 'WAF/IDS' Rule Pack
Not an OWASP activity
Please not that the above pledges are NOT OWASP driven activities and OWASP has no responsibility on the allocation of the funds pledged. This is an experiment to see how this model could be used to generate funds for OWASP Projects.
Thursday, 8 July 2010
First major release of the OWASP O2 Platform - please download and try it
After 6 months of dedicated development, I'm happy to announce that I finally published a first major release of the OWASP O2 Platform (with an installer, documentation+videos and a number of key/unique capabilities).
There is a brand new GUI which makes a massive difference in finding the available scripts, tools and APIS that exist inside O2 (if you tried the previous versions you will really appreciate this) . You can see the new GUI and access the download link at this page: http://www.o2platform.
This is the moment when I'm asking you to PLEASE TRY IT, and provide feedback on: what you like, what works, what doesn't work, what could be improved, etc... (if you want to file a bug, please use this web interface http://code.google.com/p/
There is enough functionality + capabilities + power in this version of O2, that I finally have the confidence to make this direct request for you, knowing that no matter what area of Web Application Security you are involved in, there will be an O2 Script/Module/Tool that will make you more productive.
Since the new GUI is very recent, most documentation and videos available start with the previous GUI. But since I can now easily create detailed WIKI documentation pages and/or videos using O2 , my plan is to reply to your questions that way (i.e. with a video or wiki page)
In addition to the new GUI, there are a number of key O2 features and capabilities that I was finally able to piece together last week (for example the creation of a 'complete trace+animation for an HacmeBank vulnerability' packaged as a UnitTest). I will be documenting these in the next days/weeks. I will also be posting soon details about a new funding & commercial-services model for O2 and 3rd party companies.
So, have a go, try it and please post on this list as much details on your 'O2 experience' as possible.
Thanks for the help
Subscribe to:
Comments (Atom)