This is what it looked like:
 I was happy with the design and funcionality of this site and Drupal, BUT the problem happened when I recently logged in into the admin section of the website and saw this:
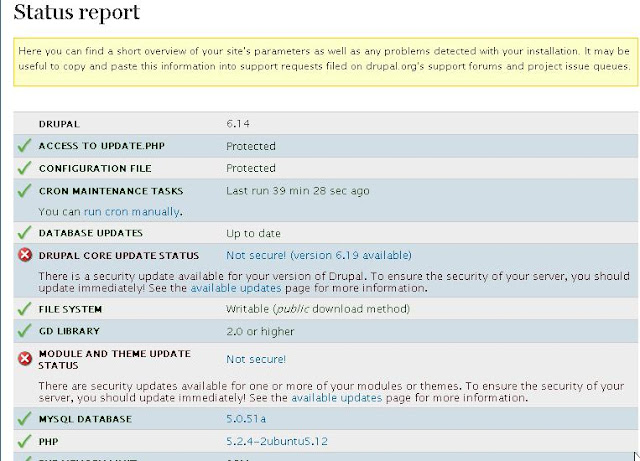
I was happy with the design and funcionality of this site and Drupal, BUT the problem happened when I recently logged in into the admin section of the website and saw this:Ok, this doesn't sound good. I wonder what does 'One or more problems' really mean. Lets see what the 'status report' says:
OK, so it looks like I need to update the Drupal Core and some Module/Theme.
Let's try the 'available updates':
I have to say that it is great that Drupal is already able to give me this level of alerts and information, BUT, their solution is now dependent on me downloading a bunch of of gz files (http://ftp.drupal.org/files/projects/drupal-6.19.tar.gz and http://ftp.drupal.org/files/projects/devel-6.x-1.22.tar.gz) and INSTALL them !!!!.
WTF, I don't want to have to maintain this website, in fact I don't even know how it was created!! Remember that whole point of using something like Drupal 6 Appliance from TurnkeyLinux (http://www.turnkeylinux.org/drupal6) was to spend no time maintaining it (isn't the 'Applicance' concept supposed to be 'hands-free'!!!)
Just to make sure I was not missing something obvious I went to the 'Release Notes' for one of the updates
But it contained NO information on how to do the upgrade that I was asked to do. A quick browse on the website also didn't help!
And what is really infuriating from a user's point of view, is that I have NO information on:
a) WHY this is even relevant to me,
b) what is the RISK impact, and
c) what other alternative (but as effective) mitigating strategies there are.
How am I supposed to make a business decision to spend the time, money and resources to fix this issue if I don't know:
- If my current deployment of Drupal is affected by the security vulnerabilities discovered
- Where are the security vulnerabilities?
- Can I disable the modules that have it and be done with it?
- What is the impact of these vulnerabilities?
- Have they been exploited in higher profile Drupal installations?
- What does an attack looks like (i.e what are the early signs of exploitation)
- How do I know if I have been exploited?
- Are there other mitigating factors? For example can I use a WAF to protect the affected parts?
Since is bound to happen in the future, and Drupal's update mechanisms is equal to 'brain surgery' (remember that I didn't install it, so I would have a bit a learning curve to do it properly), I'm left with no choice but to KILL the website (i.e. the Amazon EC2 image that powers it) and move to WordPress.com since at least they maintain the web application for me
See you at http://o2platform.wordpress.com (with time I will move the try-o2.com domain to over there)
Final comment: Super Kudos to the Drupal team for at least exposing the version status information so clearly. Unfortunately that is not good enough, and as a user I was left in a very uncomfortable position (where what I wanted was a 1-click 'server-side' upgrade button (with a backup/restore capability))