Using DotNet_ANSA (see end of post for more info about this tool) I was able to show a number of security issues that exist with Azure Websites
BUT (Important disclaimer):
- I was not able to see data from other Azure websites hosted on the same server (since I was limited by the IIS user account used)
- This happens because of running .NET code under Full Trust (which is the default in most ASP.NET apps, since partial trust is dead now)
- Although this is nothing new, I was surprised by the number of ASP.NET Azure specialists that were not aware that it was possible to (for example) browse files/folders outside the allocated folder and start new processes on the azure server
- These are ‘Security Issues’ and ‘Areas of concern’ for Azure (and other) deployed websites.
- These are not ‘Security Vulnerabilities’ since they happen by ‘design’
- The key is to make sure that all parties understand that this is possible (namely remove process execution on cloud/hosted services)
- I didn’t upload any exploits or metasploit-like tools (since that would be pushing my Azure testing a bit too far), but as far as I can see, they should work
- I didn't spent a lot of time on this, and there are a number of other research areas that should be pursued
So what can be done in an Azure website using DotNet_ANSA and a couple custom O2 Platform REPL scripts?
Here are a couple examples:
View folder: D:\
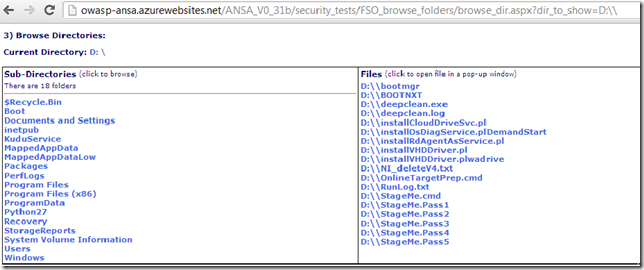
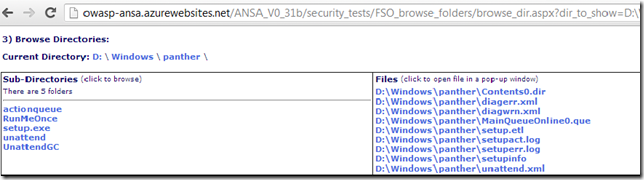
View folder: D:\windows\panther
View folder: D:\windows\System32

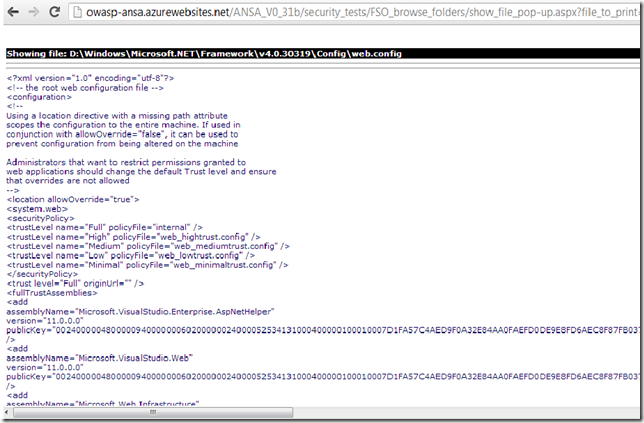
View file: …\Framework\v4.0.30319\config\web.config
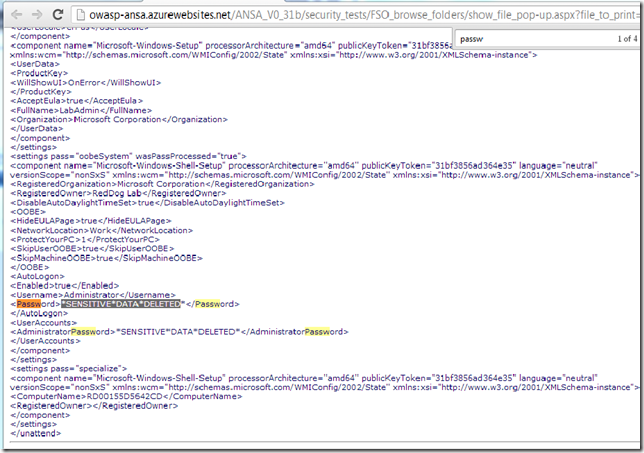
View file: Sysprep's unattend.xml (note that the admin pwd was removed)
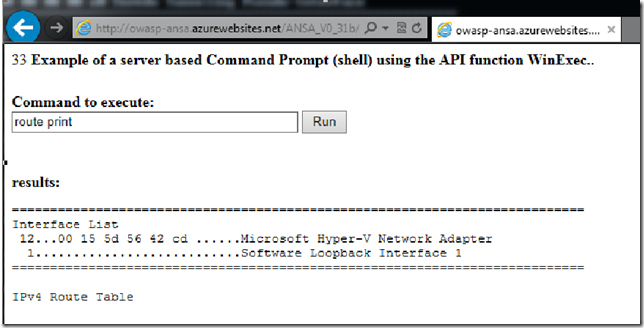
Execute via WinExe API: route print
Execute via cmd.exe: dir c:\

Execute via cmd.exe: ipconfig (access denied)

Execute via cmd.exe: ping (help contents)

Execute via cmd.exe: ping (execution fails)

Execute via .NET Process.Start: Notepad (process will start and asp.net thread will hang while notepad is still open (on the server))
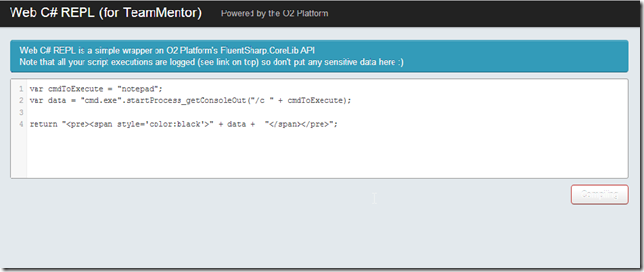
Execute via c# REPL: get process list (where we see the notepad process started above)

Execute via uploaded exe : hostname.exe

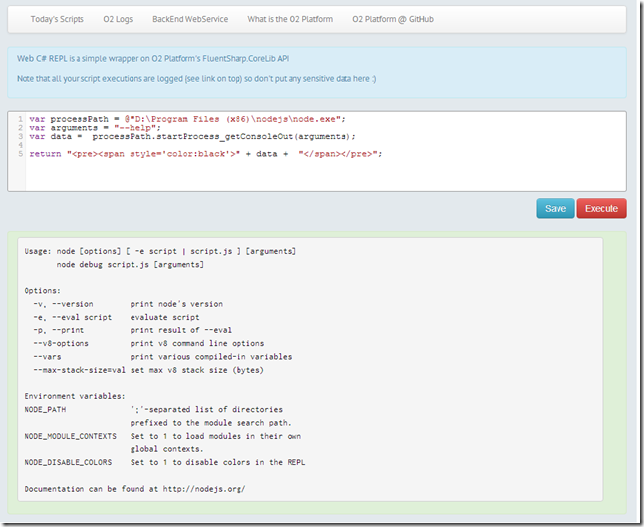
Execute via .NET Process.Start: Node.exe --help (Node JS)
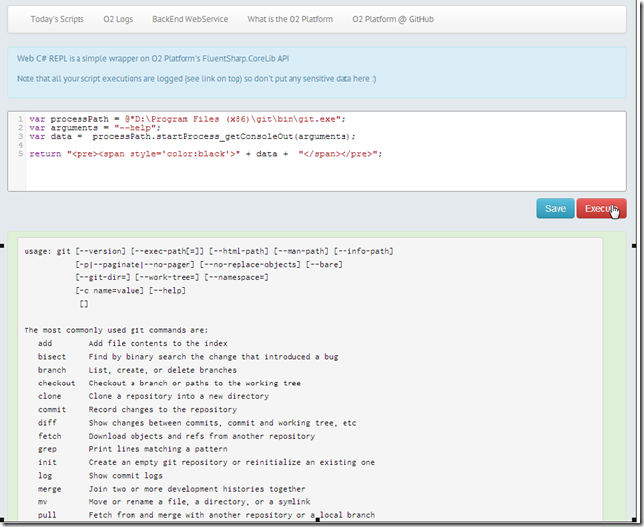
Execute via .NET Process.Start: git.exe --help
Executed via C# REPL Script (visualised locally): List Environment Variables:

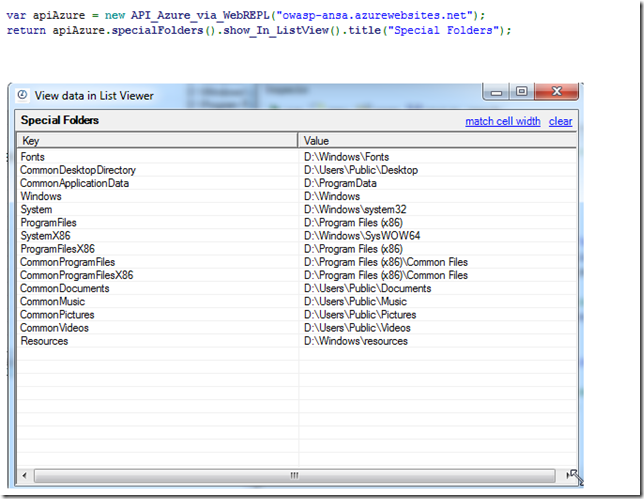
Executed via C# REPL Script (visualised locally): List special folders:
Executed via C# REPL Script (visualised locally): Environment values (via Reflection)

Executed via C# REPL Script: Environment.CommandLine

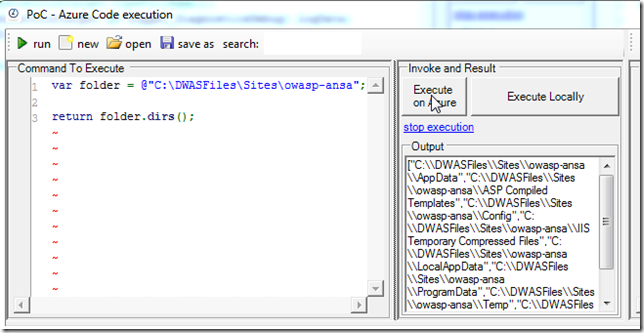
Executed via C# REPL Script: folders (value returned as JSON object)
Note: WMI is disabled which dramatically reduces the attack surface:

OWASP ANSA:
To create the screenshots shown above I used the OWASP ANSA webapp which I just pushed to the OWASP GitHub repo https://github.com/OWASP/DotNet_ANSA.
This is a very rough web app which is based on the original ASP and ASP.NET security research that I did years ago (2008 to be exact) with large parts of the code still written in VB and for .Net 1.1:
- https://www.owasp.org/index.php/ANSA (screenshots of what it looks like)
- https://www.owasp.org/index.php/ANBS
- https://www.owasp.org/index.php/ASP.NET_Reflector
In fact you can see by the evolution of the screenshots how I was fixing the code and styles during my research :)