The power of this PoC is to show that we can have the best of both worlds and show security consultants and developers the best possible environment/UI for them to analyze, review and fix security vulnerabilities.
We start with an instance of Eclipse Juno with the Fortify Plug-in installed, where I opened the Fortify Audit perspective, in order to have access to the multiple Fortify specific views:
Next I opened an instance of WebInspect 10.0:

Since we need to add a couple panels into WebInspect (which is a .NET process), the first step is to inject an O2 REPL UI into the WebInspect process.
Note 1: if we were doing a pure Win32 Handle Hijacking this would not be needed, but in this case I want to control where the Fortify Views will be placed.
Note 2: since Web Inspect is running with elevated privileges (i.e. full admin), we will also need to run the O2 Platform with the same privileges (or the dll injection will not work).
The script/tool that I’m going to use is the Util - Inject O2 into other processes.h2, which can be executed from here:
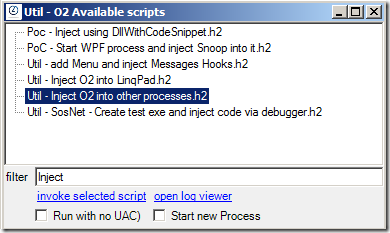
…or here:

On the Util - Inject O2 into other processes.h2 UI, find the WebInspect process on the left-hand-side process list (a screenshot of the process should be visible if we have enough privileges to inject into this process) and click on the ‘Inject O2 REPL into Process’ button:
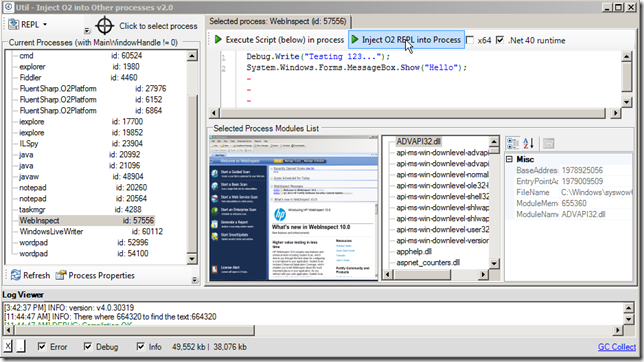
An C# REPL Editor should appear (a good clue that the injection worked ok is the fact that the top-left icon of the the REPL Form matches the icon of WebInspect):

Another way to confirm that this C# REPL script is indeed inside the WebInspect process, is to execute:
return Processes.getCurrentProcess();
… which will return the C# object of the current process (note the ProcessName value below):

Since WebInspect is using .NET WinForms as its main windows host (there are a number of WPF controls in there, but the main window is an instance of System.Windows.Forms.Form), we can use this command to get the list of open forms:
var openForms = Application.OpenForms;
return openForms;
- the main WebInspect UI
- an hidden WebInspect update window
- the O2 platform C# REPL (currently executing the script)
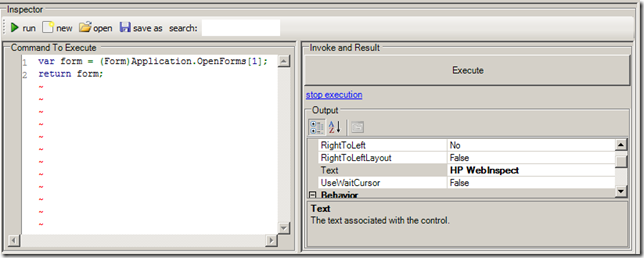
var form = (Form)Application.OpenForms[1];
return form;
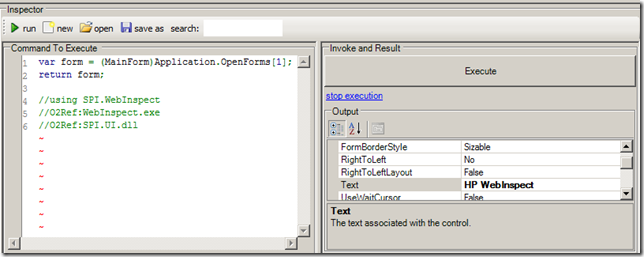
var form = (MainForm)Application.OpenForms[1]; return form; //using SPI.WebInspect //O2Ref:WebInspect.exe //O2Ref:SPI.UI.dll
var form = (MainForm)Application.OpenForms[1];
form.insert_Right()
.add_Script_Me(form);
return form;
//using SPI.WebInspect
//O2Ref:WebInspect.exe
//O2Ref:SPI.UI.dll
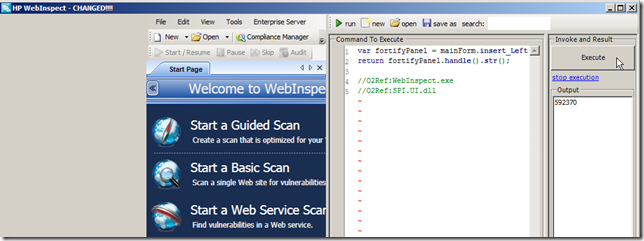
var fortifyPanel = mainForm.insert_Left(); return fortifyPanel.handle().str(); //O2Ref:WebInspect.exe //O2Ref:SPI.UI.dll
For example if we wanted to add a real cmd.exe command prompt to it we could execute:
var leftPanelHandle = 592370.intPtr();
var cmdExe_WindowHandle = "cmd.exe".startProcess()
.waitFor_MainWindowHandle()
.MainWindowHandle;
cmdExe_WindowHandle.setParent(leftPanelHandle);
return cmdExe_WindowHandle.str();
var leftPanelHandle = 592370.intPtr();
var cmdExe_WindowHandle = "notepad.exe".startProcess()
.waitFor_MainWindowHandle()
.MainWindowHandle;
cmdExe_WindowHandle.setParent(leftPanelHandle);
return cmdExe_WindowHandle.str();
But we can do the same thing for any child window.
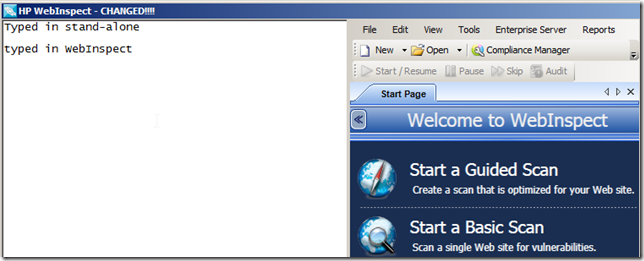
For example we could inject the actual Notepad Text Editor (vs the whole Notepad UI).
The following script:
var leftPanelHandle = 592370.intPtr();
var notepadProcess = "notepad.exe".startProcess();
var notepad_WindowHandle = notepadProcess.waitFor_MainWindowHandle()
.MainWindowHandle;
var notepadInnerWindow = notepad_WindowHandle.child_Windows().first();
10000.wait();
var originalParent = notepadInnerWindow.get_Parent();
notepadInnerWindow.setParent(leftPanelHandle);
notepadInnerWindow.window_Redraw();
10000.wait();
notepadInnerWindow.setParent(originalParent);
return notepadInnerWindow.str();
Will:
- Open Notepad
- Get Notepad’s main window handle
- Get the first child window from that handle
- Save the parent of the first child window
- Wait 10 secs (to give us time to type something on the Notepad window, when running OUTSIDE the WebInspect UI
- Set the parent of the Notepad child window (the TextEditor) to be the Webinspect Panel
- Wait 10 sec (to give us time to type something on the Notepad window, when running INSIDE the the WebInspect UI)
- Reset the original Notepad Child window parent
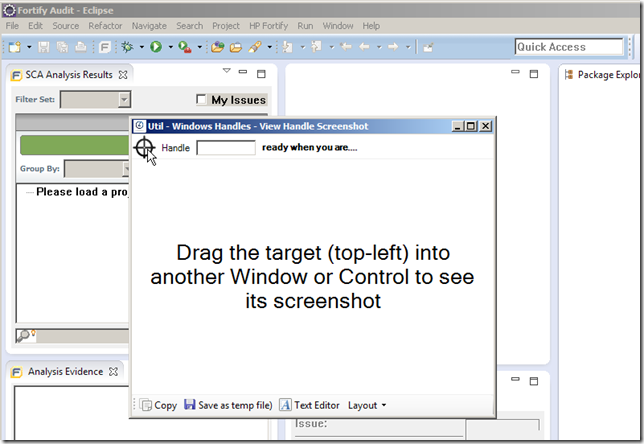
To do that we need to find the handle of the window we want to inject.
There are numerous ways to do this, one of them is to use the Util - Windows Handles - View Handle Screenshot.h2 script:
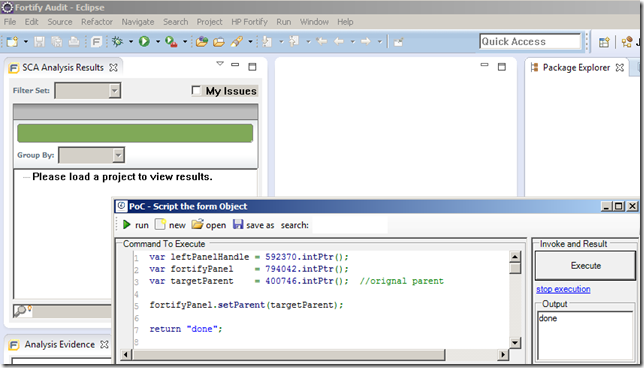
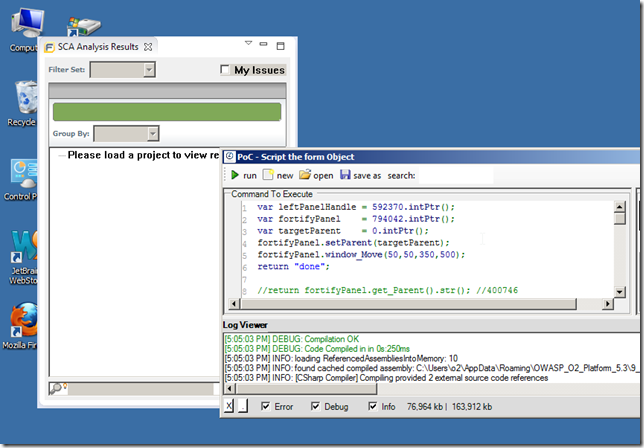
var leftPanelHandle = 592370.intPtr(); var fortifyPanel = 794042.intPtr(); //return fortifyPanel.get_Parent().str(); //400746 (backup in case we want to restore it) fortifyPanel.setParent(leftPanelHandle); return "done"; //using O2.XRules.Database.APIs //O2File:O2File:API_WinAPI.cs
In the screenshot above the Fortify Plug-in View was not correctly resized to its new parent. This can be corrected using this script:
var leftPanelHandle = 592370.intPtr();
var fortifyPanel = 794042.intPtr();
var rect = fortifyPanel.get_Parent().window_Rectangle();
fortifyPanel.window_Move(0,0,rect.Width,rect.Height);
Returning back the Fortify Eclipse Plugin View
Here are a couple interesting places to put the view back:
Example #1) The Desktop (using the parent handle 0)
Note that that window will not be movable or resizable (i.e. it is stuck in that location))
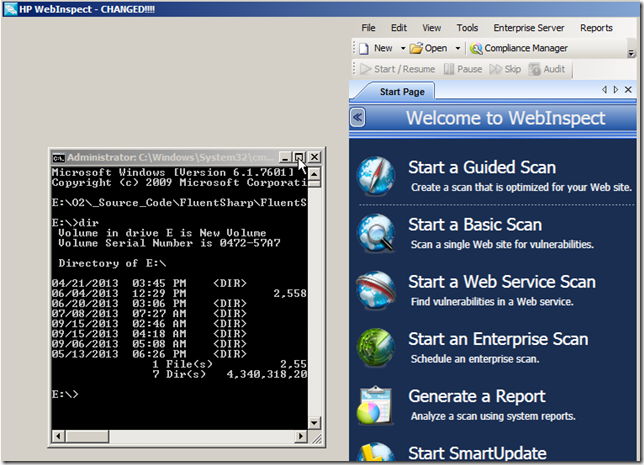
Example #2) Cmd.exe (using the cmd.exe MainWindowHandle as the parent)

Note that in cases like this, the host process can be resized but the injected window will remain in the same relative place (to its parent window)
So we can create GUIs like this, where the Fortify Plugin View is nicely positioned to the top right of a cmd.exe process:

Example #3) Notepad: (same technique as shown above)

Example #4) Eclipse (returning the view to its original parent)