Note that I didn’t expect any of this to work in IE since fuzzing is part of Microsoft’s SDL (and so should be for anybody that creates C++ that parses binary data).
The first step was to generate the 'Fuzzed' images, which were created using this script (see Gist at the end of this post):

This script takes an base image (for example a gif, png or ico):

And creates 1000s of files with only a series of bits changed on all bytes.
For example, here are 8330 images based on a Gif mage with 1.62kb in size (with generateAllBytes=false):

… here are 5745 images based on a ICO mage with 1.12kb in size (with generateAllBytes=false):

… here are 11,415 images based on an Png of size 2.23kb in size (with generateAllBytes=false):

… here are 426,496 images based on the Gif mage with 1.62kb in size (with generateAllBytes=true):

To test this files, I created this base O2 Script:
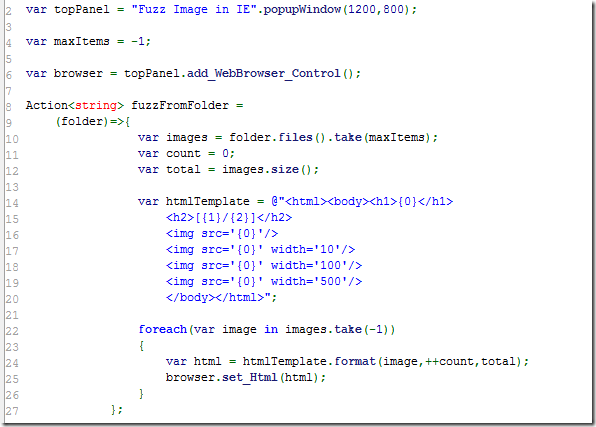
which was then imported by this script, for the GIF fuzzing:

.. this script for the PNG fuzzing:
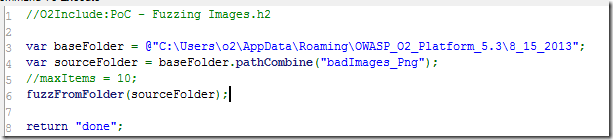
… and this script for the ICO fuzzing:

The basis of the test is to create an temp HTML page that is opened in IE and that loads up the fuzzed image in a couple difference sizes (to make sure the browser renders them)
In order to be able to run these tests separately (including under a debugger to catch any unhanded exceptions), I created stand-alone exes for each of these scripts.
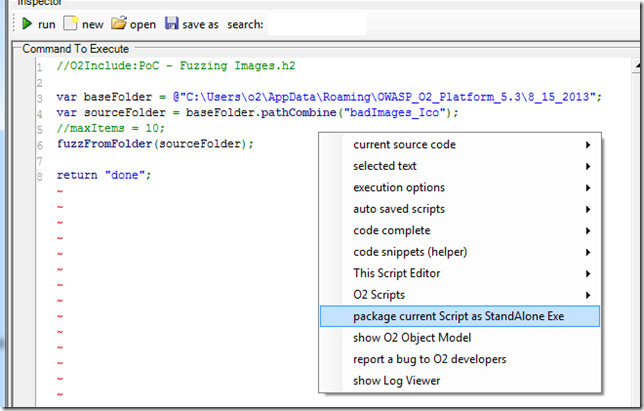
Here is the exe based on the the GIF fuzzing script:
.. the PNG fuzzing script:

… the ICO fuzzing script
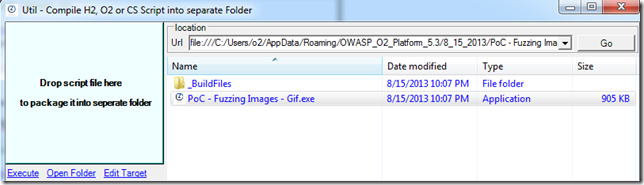
The final step is to run each of these exes (here all copied into a separate folder)
… and see if any crashes IE:
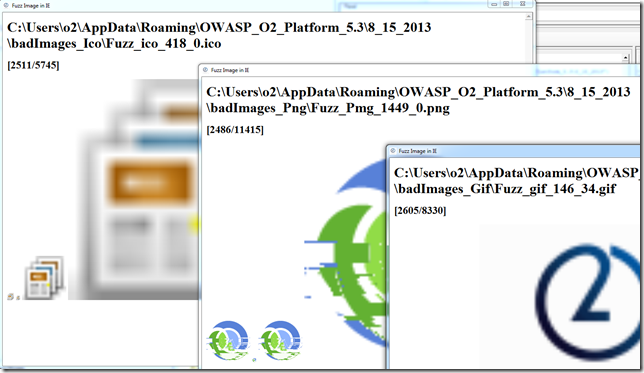
If you run this, you will see some pretty funky images (which make sense since we are creating corrupted images). And the good news is that in 2013 IE is able to handle them (a couple years back it didn’t)
For example like this one:
Note: you always run the fuzzing processes under a debugger. See Install Debugging Tools for Windows as a Standalone Component for an example.
Source code of the scripts shown in this post:
