NOTE: I used the 'contact us' form at IIS.net to ask for a direct email to send the info below, and they said to 'post it on the support forum'. (see at the end of this blog entry a screenshot of the email I sent to IIS.NET)
Btw, since the issue is still there (a week later), I think this is a honeypot
Here is blog entry I was writing when I found this (saved as a draft since).
This is either a funny joke, or an attack gone wrong.
When I was adding some references to my What happens when Asp.Net not installed on Windows 8 server post, I noticed something weird with one of the urls used as references
http://www.iis.net/learn/get-started/whats-new-in-iis--1'%20or%20'82'='82/iis-80-using-aspnet-35-and-aspnet-45
Can you spot the issue?
What about like this:
http://www.iis.net/learn/get-started/whats-new-in-iis--1'%20or%20'82'='82/iis-80-using-aspnet-35-and-aspnet-45
Just to confirm that something hadn't happened with my copy and paste, I went to the browser and confirmed that it was the correct URL

Note how these variation of the original URL don't work
http://www.iis.net/learn/get-started/whats-new-in-iis :

http://www.iis.net/learn/get-started/whats-new-in-iis/iis-80-using-aspnet-35-and-aspnet-45 :

BUT, these work:
http://www.iis.net/learn/get-started/whats-new-in-iis--1'%20or%20'83'='83/iis-80-using-aspnet-35-and-aspnet-45
http://www.iis.net/learn/get-started/whats-new-in-iis--1'%20or%20'8'='8/iis-80-using-aspnet-35-and-aspnet-45

The last ones seems to imply that there is an SQL Injection here
Now the question is where do the links with the SQL Injection payload come from?
Weirdly, it looks like they come directly from their own website!
A search for: http://www.iis.net/search?searchterm=IIS%208.0%20Using%20ASP.NET%203.5%20and%20ASP.NET%204.5

shows the SQL injection payload in there:

Same thing in Google (note the full URL in the address bar):

And sure enough, there are more cases:
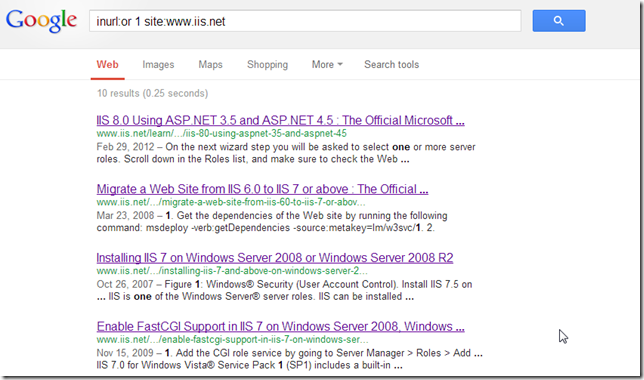
http://www.iis.net/learn/install/installing-iis-7'%20and%2070-68='2/installing-iis-7-and-above-on-windows-server-2008-or-windows-server-2008-r2

http://www.iis.net/downloads/-1'%20or%20'79'='79/2007/01/iis7-native-api-(cplusplus)-starter-kit
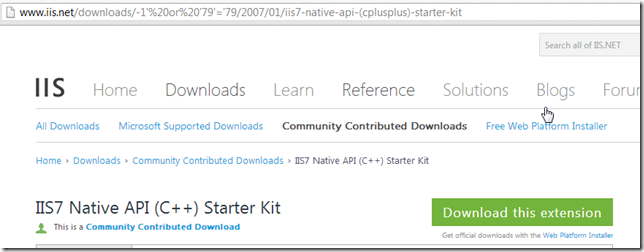
Humm, this is a bit weird, since It looks like an SQL Injection, but somehow I think this is a honeypot.
But since Google doesn't return any decent hits on that

And I’m not authorized to make any ‘SQL Injection’ tests on this side, I’m going to contact the website owners and see what they say about it
Note: Email sent to IIS.NET support team (note how they never replied to my 2nd email
