You can participate online (London) or remotely. Get your ticket here

What are GDPR Patterns?
They are reusable mappings of data journeys across specific threat modeling scenarios.
The idea is to take the diagram below and map specific scenarios to it.

‘Based on Threat Models?’
Threat models diagrams are perfect sources of data mappings since they already mapped the flows of data (where it comes from and where they go to)
Here is an example of a Threat model created at the last Summit’s Working session on Threat Modeling (on OWASP Juice shop application).
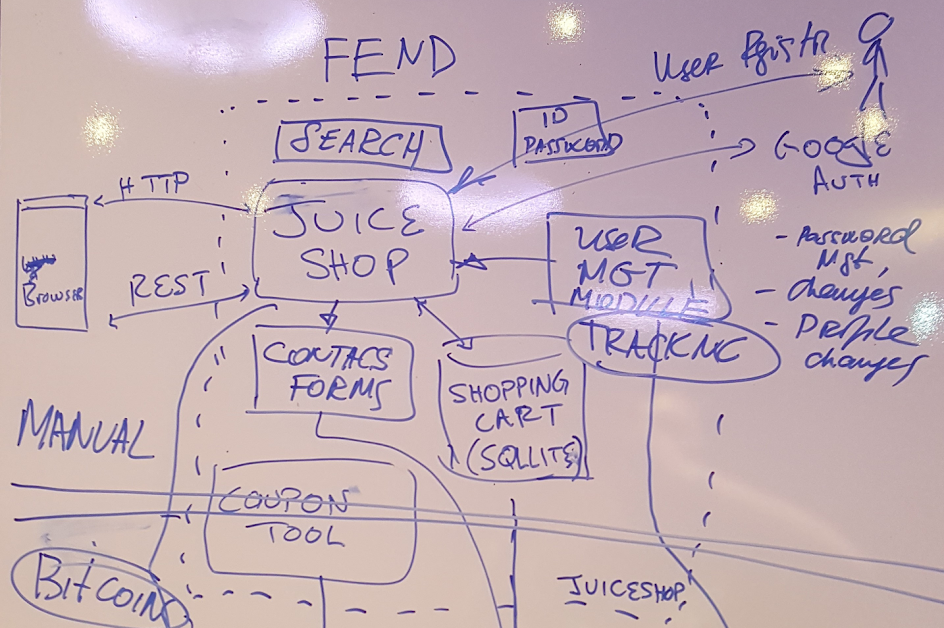
GDPR Pattern driven by Threat Model
Here is an example of what the ‘GDPR Pattern driven by Threat Model’ mapping looks like when it is done (for a service that regularly fetches data from Paypal and feeds it to AWS Redshift).
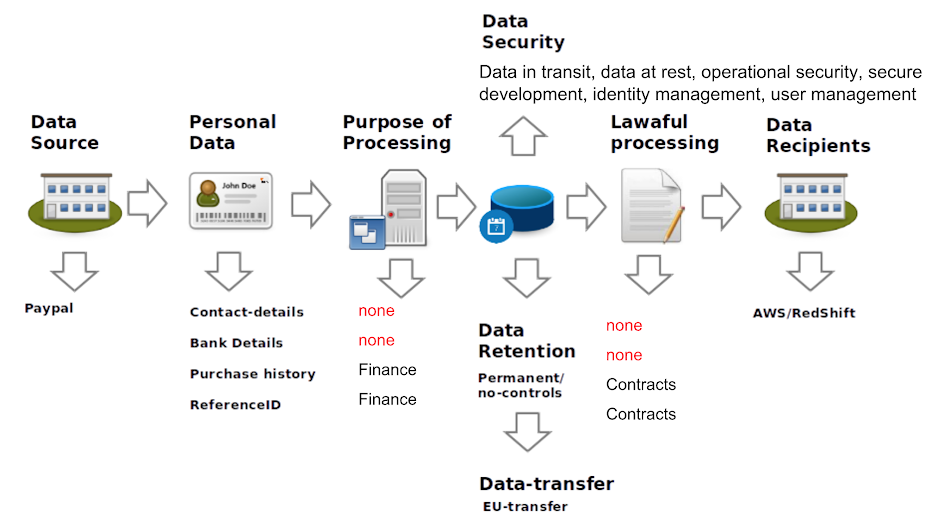
Maping GDPR Appropriate Security Measures
To help with the appropriate security controls, we use this table:
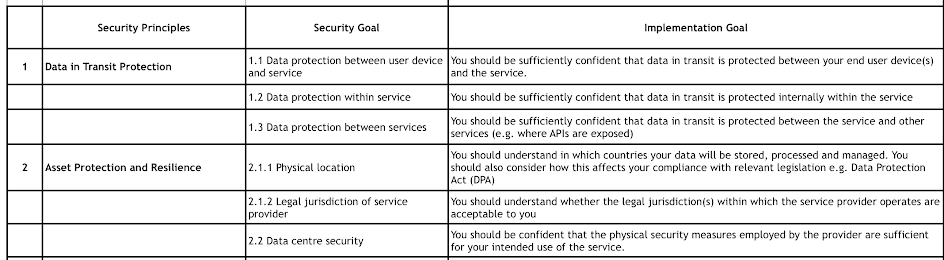
OWASP GDPR Patterns
The GDPR patterns is an OWASP Project and all materials created are released under an open source license, allowing for internal and commercial use.
All content is hosted at the https://github.com/OWASP/gdpr-patterns repo
OWASP Working Sessions
We passionately believe that the hard problems and challenges that our industry faces can only be solved by working together in a collaborative and open environment.
These OWASP Working Sessions are such events, where the community comes together, and works tirelessly on topics that they are passionate about.
Here are some photos from the last Owasp Working Sessions (on GDPR), hosted by Photobox Group Security team


Come and join us next Tuesday 20 March 2018 for more discussions.